The Kenton Brothers Technology Stack (Pyramid)
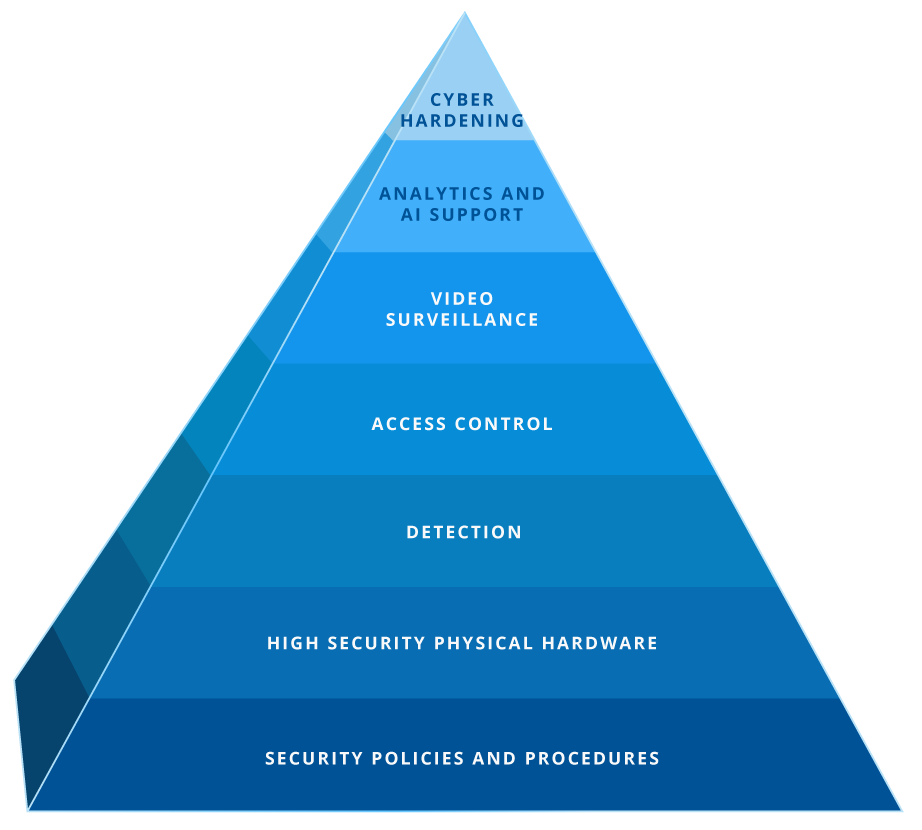
Cyber Hardening
The process of securing a computer system/network/application to make it more difficult for attackers to gain access to data resulting in unauthorized usage of information, theft or damage.
Analytics/AI support
The use of data and image analysis, machine learning and artificial intelligence to enhance decision making and problem solving.
Video Surveillance
The use of cameras to watch and record people, places or activities for security, safety or monitoring purposes.
Access Control
Electronically securing a facility to limit entry to authorized individuals.
Detection
Intrusion Detection, Perimeter Detection, Weapons Detection, Threat Detection
High Security Mechanical Locking Hardware
Commercial locks and related components that provide advanced protection against tampering, picking, key duplication and other forms of unauthorized access.
Security Policies and Procedures
Visitor management, compliance, background search, penetration testing, system health monitoring, maintenance, training
Cyber Hardening
The process of securing a computer system/network/application to make it more difficult for attackers to gain access to data resulting in unauthorized usage of information, theft or damage.
Analytics/AI support
The use of data and image analysis, machine learning and artificial intelligence to enhance decision making and problem solving.
Video Surveillance
The use of cameras to watch and record people, places or activities for security, safety or monitoring purposes.
Access Control
Electronically securing a facility to limit entry to authorized individuals.
Detection
Intrusion Detection, Perimeter Detection, Weapons Detection, Threat Detection
High Security Mechanical Locking Hardware
Commercial locks and related components that provide advanced protection against tampering, picking, key duplication and other forms of unauthorized access.
Security Policies and Procedures
Visitor management, compliance, background search, penetration testing, system health monitoring, maintenance, training

