Why are door closers so important and how do they affect the security of my building?
 By Ryan Kaullen, Field Services Manager at Kenton Brothers
By Ryan Kaullen, Field Services Manager at Kenton Brothers
It is important to understand that door closers play a pivotal role in the security of your buildings and helping keep spaces secured. What are some of the features door closers offer? Are there different types of grades on door closers?
The simple task of a door closer is to help make sure that when a door opens, it closes and helps with door latching when it returns. Door closers serve other safety and security capacities such as helping maintain the fire-rating of fire rated openings, preventing damage and wear to other door hardware, and helping doors to close quietly and not slam shut. Door closers are vital to the integrity and safety of an opening. Do not overlook them!
What are some of the features door closers offer?
Door closers offer security and safety as mentioned above, but can also offer building environment benefits as well. You may ask, “What do you mean by building environment?” Just like at your house, when a door isn’t closed your home becomes susceptible to the elements, bugs, unwanted visitors, etc. The same is true for the doors at your workplace. By adding a door closer to applicable doors, you are helping with all of these scenarios.
Preventing damage is another great feature door closers offer. Door closers slow the closing of a door and help them securely latch by pulling the door shut. Damage can come in several forms, including damage to the opening itself or even injury to a person as they are using the opening. By preventing slamming, door closers lengthen the life of the door, the frame, and other door hardware on the opening.
Door closers also offer different options in regards to functionality of a door such as wider degree openings, hold open options, longer arms, heavier duty arms, and more. When evaluating the door and type of closer needed, it’s important to evaluate what the opening is typically used for to help select the right grade, which I will get into later, and any specialty features needed. It is also important to remember that the features we’ve talked about so far are just some of the major benefits door closers offer.
Grades of door closers
 Just like other door hardware, door closers also come in different grades and standards for the type of opening they are being installed into. For instance, an exterior opening that sees a lot of foot traffic during the day should have a Grade 1 closer whereas a closet internal to the building that may be used rarely may not need a Grade 1 closer. A Grade 2 closer would be sufficient in this instance.
Just like other door hardware, door closers also come in different grades and standards for the type of opening they are being installed into. For instance, an exterior opening that sees a lot of foot traffic during the day should have a Grade 1 closer whereas a closet internal to the building that may be used rarely may not need a Grade 1 closer. A Grade 2 closer would be sufficient in this instance.
Grade 1 vs. Grade 2 also comes down to industry standards for cycle count efficiency (how many times that door can be opened before the closer fails.) Grade 1 closers offer double the cycle efficiency of a Grade 2 closer. This is another reason it’s so important to understand the usage/foot traffic the door is going to see in a day. Grade 1 closers cost more than Grade 2 closers, but you need to look at the situation to determine the investment. If one of your doors has a ton of foot traffic every day, and you opt to go with a lower grade closer, you will be replacing it sooner (and more often) than a Grade 1 closer. Often, Grade 1 closers are the better long term financial decision.
When it comes down to selecting a door closer, it’s important to pick the right closer for the given application. Safety and security play a huge role in this decision. Kenton Brothers installs hundreds (if not thousands) of door closers every year. Our Security Consultants can provide insight and industry best practice suggestions for your openings to help you pick the right door closers. Give us a call to discuss!

 Commercial grade hardware is built to withstand areas with higher amounts of traffic than residential buildings require. Essentially what you put on your home isn’t the same as what goes on the front door of a highly used commercial space. Along with commercial hardware being heavier duty, most commercial buildings have specific requirements when it comes to meeting certain specifications such as UL Listings, ADA compliance, or other life safety conditions.
Commercial grade hardware is built to withstand areas with higher amounts of traffic than residential buildings require. Essentially what you put on your home isn’t the same as what goes on the front door of a highly used commercial space. Along with commercial hardware being heavier duty, most commercial buildings have specific requirements when it comes to meeting certain specifications such as UL Listings, ADA compliance, or other life safety conditions.

 By
By 


 Safes are made to keep items secure and for the most part they do a really good job, sometimes too good a job. When safe locks fail, get tampered with, and can’t be unlocked, you have a few options.
Safes are made to keep items secure and for the most part they do a really good job, sometimes too good a job. When safe locks fail, get tampered with, and can’t be unlocked, you have a few options.

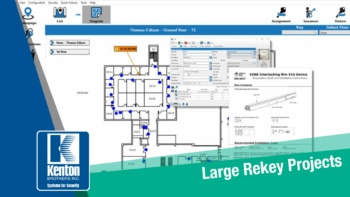 In a company or organization, it’s up to the organizational leaders to make sure that their people, property and possessions are kept safe and secure. Part of the strategy relies on the keying method used in the building(s). Kenton Brothers has been helping companies with large rekey projects since 1897.
In a company or organization, it’s up to the organizational leaders to make sure that their people, property and possessions are kept safe and secure. Part of the strategy relies on the keying method used in the building(s). Kenton Brothers has been helping companies with large rekey projects since 1897.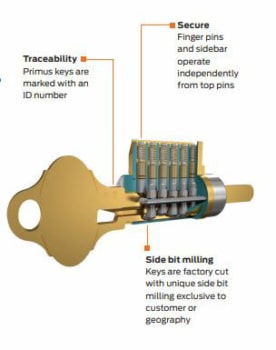 Setting up a master key system for one large facility, a campus environment with multiple buildings, or even a scenario where there are different buildings across the country can all be handled by setting up a master key system that allows for growth/expansion and the flexibility within that system to do so.
Setting up a master key system for one large facility, a campus environment with multiple buildings, or even a scenario where there are different buildings across the country can all be handled by setting up a master key system that allows for growth/expansion and the flexibility within that system to do so. So now that a master key system has been agreed upon, pricing approved, and materials are on order, what are the next steps? At this point, you will have chosen the path of how you will manage your key system; either internally or through a company such as Kenton Brothers. 80% of the effectiveness of the new keying system is in maintaining control of the keys!
So now that a master key system has been agreed upon, pricing approved, and materials are on order, what are the next steps? At this point, you will have chosen the path of how you will manage your key system; either internally or through a company such as Kenton Brothers. 80% of the effectiveness of the new keying system is in maintaining control of the keys! The install itself will begin with a Project Manager (PM) introducing you to the technicians who will be working on the project. The PM makes sure that once on site, the techs have clear expectations of their daily goals, know the location of material being stored onsite (if applicable), and any other project related questions they might have. Then the work begins!
The install itself will begin with a Project Manager (PM) introducing you to the technicians who will be working on the project. The PM makes sure that once on site, the techs have clear expectations of their daily goals, know the location of material being stored onsite (if applicable), and any other project related questions they might have. Then the work begins!