By David Strickland, Vice President of Kenton Brothers
With a tremendous focus on Cybersecurity right now, many organizations are investing substantial resources in protecting their digital assets from online threats. However, amidst the ever-evolving landscape of security risks, the significance of physical security and it’s role in a holistic approach to protecting people property and possessions should not be underestimated.
A robust physical security plan, employing the principle of defense by design, can fortify businesses against a myriad of threats, ranging from cybersecurity threats, theft and vandalism to unauthorized access and violence in the workplace. In this blog, we’ll explore how businesses can see substantial benefits by implementing a proper physical security plan centered around defense by design.
Understanding Defense by Design
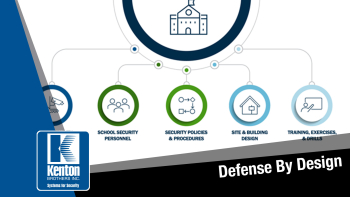 Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy.
Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy.
One of the primary benefits of adopting defense by design principles in physical security planning is the enhanced protection it offers against various threats. By strategically incorporating barriers, access controls, surveillance systems, and other security features into the layout of a facility, businesses can significantly reduce the likelihood of unauthorized access, theft, or vandalism.
For instance, installing perimeter fencing, access gates with electronic locks, and surveillance cameras can create a formidable first line of defense against intruders. Additionally, implementing measures such as biometric access controls, motion sensors, and alarm systems further reinforce security layers, making it increasingly difficult for unauthorized individuals to breach the premises undetected.
Mitigation of Risks and Liabilities
Effective physical security not only safeguards assets but also helps mitigate risks and liabilities associated with security breaches. Businesses operating in industries handling sensitive information, valuable assets, or high-risk materials are particularly vulnerable to potential threats. A robust physical security plan reduces the likelihood of security incidents, thereby minimizing the risk of theft, property damage, or regulatory non-compliance.
Moreover, in the event of a security breach, having comprehensive security measures in place can demonstrate due diligence on the part of the business, potentially mitigating legal liabilities and financial losses. By investing in defense by design, businesses not only protect their assets but also safeguard their reputation and maintain trust with stakeholders.
Safeguarding Personnel and Assets
In addition to protecting physical assets, a well-executed physical security plan prioritizes the safety and well-being of personnel. Employees are vital assets to any business, and ensuring their safety within the workplace is paramount. By implementing measures such as access control systems, emergency response protocols, and secure areas for sensitive operations, businesses create a secure environment that fosters employee confidence and productivity.
Furthermore, defense by design principles extend beyond the protection of physical assets to safeguarding intellectual property and confidential information. Secure storage facilities, restricted access areas, and surveillance systems help prevent unauthorized access to sensitive data, reducing the risk of intellectual property theft or corporate espionage.
Cost-Efficiency and Long-Term Sustainability
While implementing a comprehensive physical security plan requires an initial investment, the long-term benefits far outweigh the costs. By proactively addressing security vulnerabilities through defense by design, businesses can minimize the need for reactive security measures and costly incident response procedures.
Moreover, the deterrent effect of visible security measures can dissuade potential threats, reducing the likelihood of security incidents and associated expenses. Over time, the cost savings achieved through enhanced security and risk mitigation contribute to the long-term sustainability and profitability of the business.
At Kenton Brothers Systems for Security we work with organizations with a wide range of needs for physical Security. We have specific recommendations on how to implement a proper physical Security Plan that incorporates a holistic approach to our customer’s needs.
The following is a top 10 list of ways to get started:
1. Conduct Comprehensive Risk Assessment
Begin by conducting a thorough risk assessment of your premises and operations. Identify potential security threats and vulnerabilities, considering factors such as location, industry, and business assets. This assessment forms the foundation for developing an effective physical security plan tailored to your specific needs. We offer this service free of charge to help support the communities we serve.
2. Define Clear Security Objectives
Establish clear security objectives aligned with your business goals and risk assessment findings. Determine what assets and areas require protection, whether it’s sensitive data, equipment, or personnel. Clearly defined objectives provide a roadmap for designing and implementing targeted security measures. This can be overwhelming at first, Kenton Brothers can help guide you through this process.
3. Design Secure Perimeter Barriers
Create a secure perimeter around your facility using physical barriers such as fencing, walls, locked perimeter doors or bollards. Choose materials and designs that deter unauthorized access and provide visibility for surveillance. Incorporate access control points with electronic locks and gates to regulate entry and exit. The idea here is to extend your threat detection perimeter as much as possible to allow more time to bring resources to bear on the threat.
4. Implement Access Control Systems
Deploy access control systems to manage and monitor entry points throughout your facility. Utilize technologies such as key cards, biometric scanners, or PIN codes to authenticate individuals and restrict access to authorized personnel only. Integrate access control systems with surveillance cameras and alarms for enhanced security.
5. Install Surveillance Cameras and Monitoring Systems
Strategically place surveillance cameras and monitoring systems to provide comprehensive coverage of your premises. Install cameras in key areas such as entry points, parking lots, and critical infrastructure to deter theft, vandalism, and unauthorized activities. Ensure proper lighting and resolution for clear video footage.
6. Establish Secure Entry and Exit Procedures
Develop secure entry and exit procedures to control the flow of personnel and visitors. Implement protocols for visitor management, including check-in processes and temporary access badges. Train employees on security procedures and reinforce the importance of vigilance in identifying and reporting suspicious behavior.
7. Harden Physical Infrastructure
Strengthen physical infrastructure by reinforcing doors, windows, and other potential entry points. Use tamper-resistant locks, security bars, and shatter-resistant glass to deter break-ins and unauthorized access. Consider implementing intrusion detection systems to alert security personnel of attempted breaches.
8. Create Secure Areas for Sensitive Operations
Designate secure areas within your facility for sensitive operations, data storage, or high-value assets. Restrict access to these areas using additional layers of security such as biometric authentication or keypad entry. Implement measures to prevent unauthorized tampering or theft of sensitive materials. Concentric circles of tighter and tighter security help organizations keep their people and assets secure.
9. Develop Emergency Response Plans
Develop comprehensive emergency response plans to address various security scenarios, including intrusions, natural disasters, or workplace violence. Conduct regular drills and training exercises to ensure employees are prepared to respond effectively to emergencies. Establish communication protocols and evacuation procedures to minimize risks to personnel and assets. There is no better resource than a well-trained team member that knows what to look for and how to react in a threating situation.
10. Regularly Evaluate and Update Security Measures
Stay informed about emerging security technologies and best practices to enhance your defense by design approach. Continuously evaluate and update your physical security measures to adapt to evolving threats and vulnerabilities. Conduct regular audits and assessments to identify weaknesses and areas for improvement. This is a critical piece of defense by design. Stay vigilant in your efforts. There are many stories of the convenience of a propped door and how it led to tragedy.
By following these ten specific steps, businesses can effectively incorporate physical security measures based on defense by design principles, creating safer environments for their People, property and possessions.
Still can’t get started? Give Kenton Brothers Systems for Security a call today to help.
 There are reasons why you might want to increase security or safety by adding more features to your current access control system. Why? Copying and emulating an access card has become easier, due to new technology like a flipper zero and other skimming devices.
There are reasons why you might want to increase security or safety by adding more features to your current access control system. Why? Copying and emulating an access card has become easier, due to new technology like a flipper zero and other skimming devices. Anti-passback is the access control term when we want to prevent someone from entering a door and then passing back the card to another person, who then uses the card to enter. Most access control systems have that technology available. When this feature is enabled, you also know when a person is leaving the area. If you know when they are in the area and you know when they leave an area, then you also know where they shouldn’t appear in the building. In other words, if the cardholder is already in the building, you should not grant access to the building again.
Anti-passback is the access control term when we want to prevent someone from entering a door and then passing back the card to another person, who then uses the card to enter. Most access control systems have that technology available. When this feature is enabled, you also know when a person is leaving the area. If you know when they are in the area and you know when they leave an area, then you also know where they shouldn’t appear in the building. In other words, if the cardholder is already in the building, you should not grant access to the building again.
 Redundancy servers are put in place to keep things up and running in the event of a hardware failure. The engineering definition of redundancy is, “the inclusion of extra components which are not strictly necessary to functioning, in case of failure in other components.”
Redundancy servers are put in place to keep things up and running in the event of a hardware failure. The engineering definition of redundancy is, “the inclusion of extra components which are not strictly necessary to functioning, in case of failure in other components.” Commercial video surveillance systems rarely have server redundancy. If a server fails, the cameras will no longer be recording. Some management systems have capabilities for server failover built into the software. Unlike with an access control redundancy server where you have the hot or cold option, a video redundancy is likely going to be a hot redundancy server. If the initial server goes down, the redundancy server starts recording the video streams. Obviously, the big win in this scenario is that you mitigate the risk of lost video when you have a hardware failure at the worst possible time (when a security event is happening).
Commercial video surveillance systems rarely have server redundancy. If a server fails, the cameras will no longer be recording. Some management systems have capabilities for server failover built into the software. Unlike with an access control redundancy server where you have the hot or cold option, a video redundancy is likely going to be a hot redundancy server. If the initial server goes down, the redundancy server starts recording the video streams. Obviously, the big win in this scenario is that you mitigate the risk of lost video when you have a hardware failure at the worst possible time (when a security event is happening). A “Cold” redundancy server is one that is set up and has the systems already installed, but is not running in parallel. While it is ready to be put into production if the main server fails, there is some setup that has to occur. At minimum, restoring services requires booting up the redundancy server. However, other requirements might include installing the latest backup of card holders, schedules, routing all devices to the new server, getting the IT team and daily operations team involved. While all of those things are happening, the primary server is down. No changes to the configuration can be applied across an access control system and no video streams are being recorded until the cold redundancy server is brought online.
A “Cold” redundancy server is one that is set up and has the systems already installed, but is not running in parallel. While it is ready to be put into production if the main server fails, there is some setup that has to occur. At minimum, restoring services requires booting up the redundancy server. However, other requirements might include installing the latest backup of card holders, schedules, routing all devices to the new server, getting the IT team and daily operations team involved. While all of those things are happening, the primary server is down. No changes to the configuration can be applied across an access control system and no video streams are being recorded until the cold redundancy server is brought online. Federal Agencies are continuously seeking robust solutions to safeguard their assets and personnel. Physical security plays a pivotal role in this endeavor, encompassing a range of measures to Protect People Property and Possessions from unauthorized access or harm. Among these measures, Identity, Credential, and Access Management (ICAM) systems integrated with Physical Access Control Systems (PACS) have emerged as a cornerstone for ensuring comprehensive security solutions. In this blog, we delve into the significance of having Certified Security Engineer Identity Professional (CSEIP) certified engineers managing ICAM PACS and explore real-world use cases across government agencies.
Federal Agencies are continuously seeking robust solutions to safeguard their assets and personnel. Physical security plays a pivotal role in this endeavor, encompassing a range of measures to Protect People Property and Possessions from unauthorized access or harm. Among these measures, Identity, Credential, and Access Management (ICAM) systems integrated with Physical Access Control Systems (PACS) have emerged as a cornerstone for ensuring comprehensive security solutions. In this blog, we delve into the significance of having Certified Security Engineer Identity Professional (CSEIP) certified engineers managing ICAM PACS and explore real-world use cases across government agencies. CSEIP certification is a testament to an engineer’s expertise in designing, installing, and maintaining advanced security systems, including ICAM PACS. Expertise in ICAM PACS Integration: CSEIP certified engineers possess in-depth knowledge of ICAM PACS technologies and standards, ensuring seamless integration with existing security infrastructure. Their expertise enables organizations to optimize system performance while maintaining compliance with regulatory requirements.
CSEIP certification is a testament to an engineer’s expertise in designing, installing, and maintaining advanced security systems, including ICAM PACS. Expertise in ICAM PACS Integration: CSEIP certified engineers possess in-depth knowledge of ICAM PACS technologies and standards, ensuring seamless integration with existing security infrastructure. Their expertise enables organizations to optimize system performance while maintaining compliance with regulatory requirements. The Department of Defense operates a vast network of facilities and installations worldwide, each requiring stringent access control measures to safeguard classified information and sensitive equipment. By employing CSEIP certified engineers to manage ICAM PACS, the DoD ensures that only authorized personnel gain access to restricted areas. These professionals design and implement multifactor authentication systems, incorporating biometric verification and smart card technology to enhance security while streamlining access for authorized personnel.
The Department of Defense operates a vast network of facilities and installations worldwide, each requiring stringent access control measures to safeguard classified information and sensitive equipment. By employing CSEIP certified engineers to manage ICAM PACS, the DoD ensures that only authorized personnel gain access to restricted areas. These professionals design and implement multifactor authentication systems, incorporating biometric verification and smart card technology to enhance security while streamlining access for authorized personnel. Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy.
Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy. Commercial grade hardware is built to withstand areas with higher amounts of traffic than residential buildings require. Essentially what you put on your home isn’t the same as what goes on the front door of a highly used commercial space. Along with commercial hardware being heavier duty, most commercial buildings have specific requirements when it comes to meeting certain specifications such as UL Listings, ADA compliance, or other life safety conditions.
Commercial grade hardware is built to withstand areas with higher amounts of traffic than residential buildings require. Essentially what you put on your home isn’t the same as what goes on the front door of a highly used commercial space. Along with commercial hardware being heavier duty, most commercial buildings have specific requirements when it comes to meeting certain specifications such as UL Listings, ADA compliance, or other life safety conditions.

