Enhancing Physical Security with Kenton Brothers Systems for Security CSEIP Certified Engineers
By David Strickland, Vice President of Kenton Brothers
 Federal Agencies are continuously seeking robust solutions to safeguard their assets and personnel. Physical security plays a pivotal role in this endeavor, encompassing a range of measures to Protect People Property and Possessions from unauthorized access or harm. Among these measures, Identity, Credential, and Access Management (ICAM) systems integrated with Physical Access Control Systems (PACS) have emerged as a cornerstone for ensuring comprehensive security solutions. In this blog, we delve into the significance of having Certified Security Engineer Identity Professional (CSEIP) certified engineers managing ICAM PACS and explore real-world use cases across government agencies.
Federal Agencies are continuously seeking robust solutions to safeguard their assets and personnel. Physical security plays a pivotal role in this endeavor, encompassing a range of measures to Protect People Property and Possessions from unauthorized access or harm. Among these measures, Identity, Credential, and Access Management (ICAM) systems integrated with Physical Access Control Systems (PACS) have emerged as a cornerstone for ensuring comprehensive security solutions. In this blog, we delve into the significance of having Certified Security Engineer Identity Professional (CSEIP) certified engineers managing ICAM PACS and explore real-world use cases across government agencies.
Understanding ICAM PACS:
ICAM PACS integrates physical access control with identity management, enabling organizations to efficiently manage and control access to their facilities. These systems authenticate and authorize individuals based on their credentials, ensuring that only authorized personnel can enter designated areas. ICAM PACS solutions often encompass a variety of technologies such as smart cards, biometrics, and multi-factor authentication, providing layers of security to mitigate risks effectively.
Benefits of CSEIP Certified Engineers:
 CSEIP certification is a testament to an engineer’s expertise in designing, installing, and maintaining advanced security systems, including ICAM PACS. Expertise in ICAM PACS Integration: CSEIP certified engineers possess in-depth knowledge of ICAM PACS technologies and standards, ensuring seamless integration with existing security infrastructure. Their expertise enables organizations to optimize system performance while maintaining compliance with regulatory requirements.
CSEIP certification is a testament to an engineer’s expertise in designing, installing, and maintaining advanced security systems, including ICAM PACS. Expertise in ICAM PACS Integration: CSEIP certified engineers possess in-depth knowledge of ICAM PACS technologies and standards, ensuring seamless integration with existing security infrastructure. Their expertise enables organizations to optimize system performance while maintaining compliance with regulatory requirements.
By leveraging the expertise of CSEIP certified engineers, organizations can implement robust security measures tailored to their specific needs. From designing access control policies to configuring authentication mechanisms, these professionals ensure that security vulnerabilities are effectively addressed, bolstering overall protection.
With CSEIP certified engineers leading the way, organizations can mitigate the risk of security breaches and unauthorized access attempts. These experts implement industry best practices and deploy advanced security features to fortify ICAM PACS against evolving threats, safeguarding critical assets and sensitive information.
CSEIP certified engineers possess the skills to diagnose and resolve issues promptly, minimizing downtime and ensuring uninterrupted security operations. Their proactive approach to maintenance helps organizations identify potential vulnerabilities early on, preempting security risks before they escalate.
Use Case Scenarios:
Let’s explore how government agencies can benefit from having CSEIP certified engineers managing ICAM PACS:
Department of Defense (DoD):
 The Department of Defense operates a vast network of facilities and installations worldwide, each requiring stringent access control measures to safeguard classified information and sensitive equipment. By employing CSEIP certified engineers to manage ICAM PACS, the DoD ensures that only authorized personnel gain access to restricted areas. These professionals design and implement multifactor authentication systems, incorporating biometric verification and smart card technology to enhance security while streamlining access for authorized personnel.
The Department of Defense operates a vast network of facilities and installations worldwide, each requiring stringent access control measures to safeguard classified information and sensitive equipment. By employing CSEIP certified engineers to manage ICAM PACS, the DoD ensures that only authorized personnel gain access to restricted areas. These professionals design and implement multifactor authentication systems, incorporating biometric verification and smart card technology to enhance security while streamlining access for authorized personnel.
Federal Bureau of Investigation (FBI):
As the principal federal law enforcement agency, the FBI relies on robust security protocols to protect its headquarters, field offices, and forensic laboratories. CSEIP certified engineers play a crucial role in designing and maintaining ICAM PACS solutions tailored to the FBI’s specific security requirements. By deploying advanced authentication mechanisms and intrusion detection systems, these professionals help safeguard sensitive investigative materials and ensure the integrity of the agency’s operations.
Department of Homeland Security (DHS):
The Department of Homeland Security oversees critical infrastructure and coordinates efforts to protect the nation from security threats. CSEIP certified engineers support DHS initiatives by implementing comprehensive ICAM PACS solutions across various agencies and facilities. These experts collaborate with stakeholders to design access control policies aligned with DHS mandates, enhancing situational awareness and emergency response capabilities.
By entrusting ICAM PACS management to CSEIP certified engineers, organizations can reap the benefits of enhanced security, reduced risk, and streamlined operations. As demonstrated through real-world use cases in government agencies, the expertise of CSEIP certified engineers is indispensable in safeguarding critical assets and ensuring the integrity of physical security systems.
Kenton Brothers Systems for Security is proud to offer our services to our Federal Agency partners.
Please give us a call today to see how we can help support your organization!

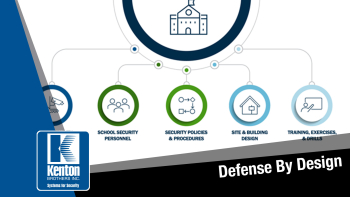 Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy.
Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy.



 Where do you feel safe? Home? Work? In your car?
Where do you feel safe? Home? Work? In your car? Is the congregation and board willing to make these changes?
Is the congregation and board willing to make these changes?




