Commercial Security: Redundancy Servers and Why They Matter
By Ryan Kaullen, Field Services Manager at Kenton Brothers
 Redundancy servers are put in place to keep things up and running in the event of a hardware failure. The engineering definition of redundancy is, “the inclusion of extra components which are not strictly necessary to functioning, in case of failure in other components.”
Redundancy servers are put in place to keep things up and running in the event of a hardware failure. The engineering definition of redundancy is, “the inclusion of extra components which are not strictly necessary to functioning, in case of failure in other components.”
Redundancy servers can be put in place for access control systems and commercial video surveillance systems. There are also a couple of types of redundancy server options called “hot” and “cold”. In this blog, we will talk about these types and options and how they work to make your commercial security system more resilient.
Access Control Redundancy Server
Access control systems already have some redundancy built into them. The door controllers have on board memory, so they will continue to operate even if the main server fails. However, any changes that would need to be made to the card holders or door schedules in the event the main server fails can’t happen until the server is repaired. This is where a redundancy server for the access control system comes into play. Depending on if you have a hot or cold redundancy server (we will discuss the differences later in this article) you will see either a shortened down time or almost no down time.
Commercial Video Surveillance System Redundancy Server
 Commercial video surveillance systems rarely have server redundancy. If a server fails, the cameras will no longer be recording. Some management systems have capabilities for server failover built into the software. Unlike with an access control redundancy server where you have the hot or cold option, a video redundancy is likely going to be a hot redundancy server. If the initial server goes down, the redundancy server starts recording the video streams. Obviously, the big win in this scenario is that you mitigate the risk of lost video when you have a hardware failure at the worst possible time (when a security event is happening).
Commercial video surveillance systems rarely have server redundancy. If a server fails, the cameras will no longer be recording. Some management systems have capabilities for server failover built into the software. Unlike with an access control redundancy server where you have the hot or cold option, a video redundancy is likely going to be a hot redundancy server. If the initial server goes down, the redundancy server starts recording the video streams. Obviously, the big win in this scenario is that you mitigate the risk of lost video when you have a hardware failure at the worst possible time (when a security event is happening).
Hot and Cold Redundancy Server Options
A “Hot” redundancy server is one that runs in parallel with the main server. If the main server goes down, the redundancy server immediately picks up when the other one failed. This is usually a more expensive option as there can be more licenses, hardware, and integration needed so that it is running in parallel. The major pro here is that failover times are measured in milliseconds and after the initial set up requires no intervention from an IT team.
 A “Cold” redundancy server is one that is set up and has the systems already installed, but is not running in parallel. While it is ready to be put into production if the main server fails, there is some setup that has to occur. At minimum, restoring services requires booting up the redundancy server. However, other requirements might include installing the latest backup of card holders, schedules, routing all devices to the new server, getting the IT team and daily operations team involved. While all of those things are happening, the primary server is down. No changes to the configuration can be applied across an access control system and no video streams are being recorded until the cold redundancy server is brought online.
A “Cold” redundancy server is one that is set up and has the systems already installed, but is not running in parallel. While it is ready to be put into production if the main server fails, there is some setup that has to occur. At minimum, restoring services requires booting up the redundancy server. However, other requirements might include installing the latest backup of card holders, schedules, routing all devices to the new server, getting the IT team and daily operations team involved. While all of those things are happening, the primary server is down. No changes to the configuration can be applied across an access control system and no video streams are being recorded until the cold redundancy server is brought online.
Having back-ups in place for any commercial security system is critical. Redundancy servers play a huge role in making that a reality. Our security consultants will work with your organization to help you identify the right redundancy server option for your facility. If you would like to know more, please reach out to us today to start a discussion on how to provide redundancy for your systems.





 5 MP video with two-way audio.
5 MP video with two-way audio. The AXIS W110 Body Worn Camera provides security personnel with a powerful tool for documenting incidents and enhancing situational awareness. Compact and lightweight, this body-worn camera can be easily attached to uniforms or vests, enabling hands-free operation without impeding mobility.
The AXIS W110 Body Worn Camera provides security personnel with a powerful tool for documenting incidents and enhancing situational awareness. Compact and lightweight, this body-worn camera can be easily attached to uniforms or vests, enabling hands-free operation without impeding mobility. The AXIS D2210-VE Radar represents a paradigm shift in perimeter protection, leveraging advanced radar technology to detect and track intrusions with unparalleled accuracy. Unlike traditional motion sensors, which are prone to false alarms triggered by environmental factors, this radar device offers reliable detection capabilities in all weather conditions and lighting environments.
The AXIS D2210-VE Radar represents a paradigm shift in perimeter protection, leveraging advanced radar technology to detect and track intrusions with unparalleled accuracy. Unlike traditional motion sensors, which are prone to false alarms triggered by environmental factors, this radar device offers reliable detection capabilities in all weather conditions and lighting environments.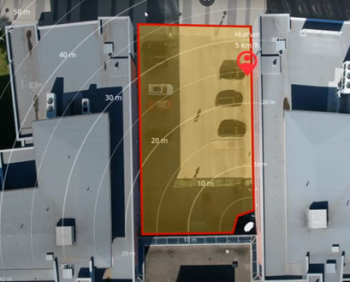 AXIS D2210-VE offers a 95° field of detection and can detect, classify, and track humans up to 60 m (200 feet) and vehicles up to 90 m (295 feet). And, with road monitoring profile enabled, the detection range for vehicles increases up to 150 m (492 feet). The radar also provides the exact position of the detected objects. AXIS D2210-VE can be used stand-alone for non-visual monitoring while safeguarding privacy. Or it can be used to steer a PTZ camera for visual verification. Furthermore, with smart coexistence functionality, it’s possible to combine up to eight AXIS D2210-VE radars in close proximity. And, you can even expand the installation with up to six AXIS D2110-VE radars and customize your detection area depending on your needs.
AXIS D2210-VE offers a 95° field of detection and can detect, classify, and track humans up to 60 m (200 feet) and vehicles up to 90 m (295 feet). And, with road monitoring profile enabled, the detection range for vehicles increases up to 150 m (492 feet). The radar also provides the exact position of the detected objects. AXIS D2210-VE can be used stand-alone for non-visual monitoring while safeguarding privacy. Or it can be used to steer a PTZ camera for visual verification. Furthermore, with smart coexistence functionality, it’s possible to combine up to eight AXIS D2210-VE radars in close proximity. And, you can even expand the installation with up to six AXIS D2110-VE radars and customize your detection area depending on your needs. In a distant medieval realm, nestled between rolling hills and dense forests, there existed a peaceful village named Eldoria. The villagers, content in their simple lives, lived in harmony with the land. However, peace is a fragile thing, and the tranquility of Eldoria was shattered when rumors of marauding bandits spread like wildfire. Travelling caravans spoke of their perils and the destruction left behind by these marauders.
In a distant medieval realm, nestled between rolling hills and dense forests, there existed a peaceful village named Eldoria. The villagers, content in their simple lives, lived in harmony with the land. However, peace is a fragile thing, and the tranquility of Eldoria was shattered when rumors of marauding bandits spread like wildfire. Travelling caravans spoke of their perils and the destruction left behind by these marauders.


