Is anyone really monitoring your security activities? You’ve invested so much…
By Kevin Whaley, CPP, Sr. Security Consultant at Kenton Brothers
Prior to the September 11 terrorist attacks on the World Trade Center and the Pentagon, the most significant threat to the United States was the former Soviet Union. At that time, governments believed that only foreign state actors or representatives posed a significant threat to national security. Security measures were based around this belief that a great security threat only existed in the form of state actors, putting the responsibility for security into the hands of the government.
Today the threat of attacks and their intended targets has expanded to not only government entities, but private organizations as well. These attacks have evolved from identifiable state actors, to adversaries with no state affiliation. The conflicts of today are no longer fought on open battlefields – but instead fought daily against adversaries who are not easily identified. Similarly, much like our adversaries have evolved, so have their tactics. When new protection measures are implemented, adversaries adapt their tactics, and so the cat and mouse game continues.
Goals of a Security Program
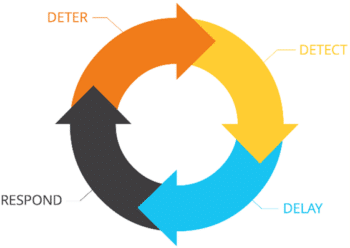
The goal of any security program is to deter, detect, delay, and respond as efficiently and effectively as capable. To ensure this, organizations must regularly re-evaluate their security programs to ensure that they are staying up to date with current technologies, best practices, and the modus operandi used by adversaries. Failure to do so will only increase the vulnerabilities and risks to the organization. It is current best-practice and recommended by security professionals that a security assessment be conducted annually to assist in ensuring your organization is mitigating risks or minimizing the consequences.
Unfortunately, there is no “one-size-fits-all” approach to conducting a security assessment. Depending on your industry, there may be minimum standards that must be met, which can assist you in development and evaluation of your security program. However, each assessment must be tailored to each organization’s unique operating environment.
The basics of any security assessment should consider items including but not limited to:
- Policies
- Processes/Procedures
- Crime Analysis
- Historical Incidents
- Critical assets
- Threats
- Vulnerabilities to those threats
- Risks associated with threats
- Security systems operational capabilities
- Access Control
- Video Surveillance
- Intrusion Detection
Annual Security Evaluation
Conducting an annual evaluation of at least the aforementioned can help your organization ensure that your security program is operating as intended, assist in identifying areas for improvement, and staying up-to-date with industry best-practices. These assessments can typically be completed by in-house security personnel or by third-party consultants.
In-house assessments are beneficial since in-house personnel typically already have the institutional knowledge and may know what the issues and/or possible solutions are. However, the old adage of “if it’s not broken, don’t fix it” usually comes into play. In-house assessors may be “complacent” during the assessment. I don’t mean that they get lazy or lack attention to detail but rather, have a higher probability of overlooking potential issues simply because they are used to it or “That’s how it’s always been,” or “Well, that type of incident will never happen here.”
An example to consider…

My favorite example of this exact scenario playing out is when while working for a former employer, we were attempting to sell a consulting project to a client. During one of our meetings, one of the executives stated, “I don’t know why we need to do this assessment. Nothing has happened here and really what are the chances of [incident] happening?” Less than two months later, that exact incident occurred. The next week, I received a call from the same company, asking us to please do the assessment. The security leadership already knew a lot of what we explained in our report, but recognized quite a few issues that they had been overlooking for years.
Additionally, in-house assessments may typically have a harder time getting buy-in from management or the executive team. An outside consultant can assist in providing an outside perspective. They are able to look at the program with a fresh set of eyes and identify issues that may have gone previously unnoticed. Additionally, a consultant can offer substantiation to the findings and recommendations. Not only should a thorough assessment contain “findings” and “recommendations” but should also explain the why and how behind them and how they can be harmful or beneficial. Consultants can also offer insights into similar environments and experience from other industries.
Vetting Security Consultants

It is just as important to thoroughly vet any potential consultants as it is to conduct a proper security assessment. Professional security consulting services should be completely technology and product agnostic. Look for consultants with professional designations (i.e. CPP, PSP, CSC). These show that the professional stays up-to-date with the latest best-practices through continuing education and can provide unbiased, objectively based information to the end user. Make sure to identify other assessments they’ve done, ask for references, and even a sampling of their work so that you can gauge the quality of the assessment and report.
The assessment report identifies the findings and recommendations of the assessment. This is the meat and potatoes of the report and in my opinion, the most important. The content and level of detail of the report will be based on the scope of work. This report tells the story of the security posture. This is meant to be a medium to communicate to the management/executive team or decision makers. The report should be answering who, what, where, why, and how. I did not include “when” because the occurrence of a future incident can’t be determined. If we could predict a security incident, we security professionals would be out of a job! Each “finding” should be clearly defined in the report and details of what the finding is, why it’s bad, how an adversary may take advantage, and potential risks. Similarly, each finding should be followed by a recommendation(s) to mitigate. Again, this should also include what, why it’s beneficial, and how it may improve security and mitigate the finding. I emphasize “may” because unfortunately, nothing is 100% preventable. A truly determined and dedicated adversary will find a way. In other words, show me a 10’ fence and I’ll show you an 11’ ladder.
These detailed narratives again are used to tell a story and should help to obtain buy-in needed. The report may truly be the “make or break” factor in making decisions regarding security program changes.
While conducting an assessment, part of my responsibilities included reviewing previous assessments that were completed for an organization. What really struck me was the overwhelming lack of detail and reasoning in the report. For example, a “finding” in the report stated, “The parking lot is not sufficiently illuminated.” And the recommendation was, “Recommend install more lighting in parking lot.” Wow!
Types of Security Recommendations
Not only are the details of the report important, but just as important are the types of recommendations. There are numerous people who claim to be a “security expert” or “consultant” when in reality they may have little to no experience in this field. Or they may be trying to sell you their own products and their recommendations are based around what products/services they offer as a company. This can lead to unnecessary recommendations, which can mislead the client and may cause them to spend lots of money on something that may not truly be needed.
Sometimes, the best solution may be a simple one. Not everything needs to be solved with technology or a person. Sometimes, the best solution is possibly an administrative change. Maybe something can be mitigated with a new policy or procedure, training, or just a simple discussion. Again, sharing an example from my experience, during my time with a previous organization and during my initial assessment, I noticed that there was security technology installed in places that were completely unnecessary or used inappropriately. A fifth-floor balcony, with no other means of access besides the doors leading to the balcony itself, had card readers leading into the building. When I reviewed the previous report, it literally stated that someone could grapple up to the balcony and gain entrance. Possible? Yes. Probability? Very low if not non-existent. So the organization had spent thousands of dollars of something that could have been solved with a mechanical lock like a deadbolt on the inside of the door. Additionally, they had fisheye cameras installed in areas that these cameras weren’t designed for. They were on exterior walls, monitoring doors, hallways, etc. The cameras weren’t being used to their full potential, and ended up costing thousands more than installing a different camera that would have worked better for the desired field of view. Those fisheyes I mentioned? Half of the field of view was a brick wall.
Product/Service Agnostic
Finally, if you do use a third-party consultant, it’s important that they are completely product/service agnostic. Their reports should not recommend specific products. Instead, they should keep recommendations generic. For example, instead of recommending a brand of video surveillance, the recommendation should be “a video surveillance system”. However, they should include what types of functions it should be able to accomplish and other general specifications. They may also provide examples of brands. In my reports, I would state, “recommend video surveillance system that can…..(i.e. Brand, Brand 2, other). This way, it’s left to the client to decide which products will meet their needs.
In conclusion, conducting an annual security assessment can assist with ensuring your security program stays up to date, is operating as intended, and identify areas for improvement. Whether it’s done by in-house personnel or third-party consultants should be carefully considered. However, it’s highly recommended that a third-party consultant be used in an alternating manner with in-house assessments. For example, maybe an assessment is completed in-house, but every other year or third year a consultant is utilized to help keep the assessments unbiased and to allow for a fresh view point of the security program.
At Kenton Brothers, we have a team of certified security professionals that have years of experience conducting assessments in industries across the board from education, critical infrastructure, local/state/federal organizations, healthcare, correctional facilities, etc. Our consultants remain dedicated to ensuring that we are able to help you protect your people, property, and possessions. We are here to assist you in making the decisions that work best for you and your organization.
For more information regarding security assessments, please give us a call.




Leave a Reply
Want to join the discussion?Feel free to contribute!