Commercial Safe Drilling Services are a Dying Art. We’ve Got You Covered
By Ryan Kaullen, Field Services Manager at Kenton Brothers
 Safes are made to keep items secure and for the most part they do a really good job, sometimes too good a job. When safe locks fail, get tampered with, and can’t be unlocked, you have a few options.
Safes are made to keep items secure and for the most part they do a really good job, sometimes too good a job. When safe locks fail, get tampered with, and can’t be unlocked, you have a few options.
One option is having a certified and trained safe professional try to manipulate and open it using a variety of techniques. Second, depending on the type of safe, you can cut the hinges or bolts. And third, you can perform a drilling process. Using the drilling technique can take hours to even days, especially if it is a GSA high security safe.
There are preventative measures you can take to try and help avoid a safe lock from failing:
- Preventative maintenance. Having a certified professional come on site to perform quarterly or yearly maintenance. They can assess how the safe is operating, provide proper testing, apply proper mechanical lubricants, and advise of any issues before a lock fully fails. Sometimes, locks just fail… but at Kenton Brothers we have seen time and time again preventative maintenance extending the life of the locks. This helps our clients get ahead of any potential issues with their safe(s) which helps financially in the long run.
- Do not use WD-40 on locks. WD-40 will do more damage to your safe lock than helping it. If you want to apply the right lubricant, please contact Kenton Brothers and we would be happy to sell you the correct products to use on your safe.
- Use the right locks for the right applications. This is a consistent issue. Our techs go on site and find safe locks that are not the correct rating, or not the right application, for their use requirements. Depending on the nature of your business, or what you are storing in the safe, there are certain requirements from a government level (GSA) that have to be met by law. We are obligated to report these situations when we find them. There are two options to resolve this situation: 1) Provide pricing to bring the safe up to standard or 2) Strip the safe of its certifications and fill out appropriate paperwork.
- Always keep track of your safe combinations in a safe/secure location. This is an easy way to avoid service calls.
- Make sure the company you are hiring to work on your safe/safe locks is certified. Your security provider must have experience with safe locks. Just because they are a mechanical locksmith does not mean they are certified to work on safe locks. Unauthorized fixes or attempts to fix can void warranties and cause damage to the equipment.


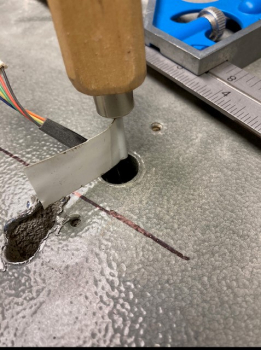
A real world story about why this matters.
Recently, we received a service call about a high security safe that was not opening. When our technician arrived on site, he found seven GSA Red Label containers. All seven had the wrong locks on them. (Remember, we are required to report these types of infractions.) We provided our customer with two options: replace all the safe locks or strip them of their certifications. The customer chose to bring one of their safes up to code and strip the rest. This was an expensive process for the customer because we had to drill one of the safes and supply the correct lock, and then do a considerable amount of government related paperwork.
Our customer could have avoided the expense of fixing incorrect locks if they had reached out to a certified GSA company when installing the containers in the first place. We would have advised them on the proper procedures and protocols. They wouldn’t have had to make the decision to decertify six expensive safes. The moral of the story is that hiring certified professionals to work on your safes may be more expensive initially, but in the long run it will be worth the investment!
We have been fortunate to work on safes of every size and level of security.
We have three GSA certified, trained, and continually educated technicians on our team. Let Kenton Brothers be the partner who keeps your safes operating correctly (or allow us to open them when you can’t!)
To schedule service of your safe please give us a call or email service@kentonbrothers.com.





 Key Management Software, especially for larger companies, schools, and companies with multiple locations is a powerful way to keep track of all the keys floating around. The Key Management Software solution that we install and configure for our clients has the following capabilities:
Key Management Software, especially for larger companies, schools, and companies with multiple locations is a powerful way to keep track of all the keys floating around. The Key Management Software solution that we install and configure for our clients has the following capabilities: Over the past decade, companies within the physical security industry have come out with electronic key tracking boxes. The idea is to secure physical keys, manage who issued keys, and make sure keys that are taken are also returned. The electronic key management boxes we install include the following features:
Over the past decade, companies within the physical security industry have come out with electronic key tracking boxes. The idea is to secure physical keys, manage who issued keys, and make sure keys that are taken are also returned. The electronic key management boxes we install include the following features: By
By  Just like other door hardware, door closers also come in different grades and standards for the type of opening they are being installed into. For instance, an exterior opening that sees a lot of foot traffic during the day should have a Grade 1 closer whereas a closet internal to the building that may be used rarely may not need a Grade 1 closer. A Grade 2 closer would be sufficient in this instance.
Just like other door hardware, door closers also come in different grades and standards for the type of opening they are being installed into. For instance, an exterior opening that sees a lot of foot traffic during the day should have a Grade 1 closer whereas a closet internal to the building that may be used rarely may not need a Grade 1 closer. A Grade 2 closer would be sufficient in this instance.