Active Shooter: Real world stories about lockdowns in schools saving lives.
By David Strickland, Vice President of Kenton Brothers
On November 14th, 2017 at 7:30 am, shots ring out near Rancho Tehama Elementary in Northern California. It’s an all too familiar but tragic scenario these days. One moment children are playing on a full playground, the next, panic, confusion and the succession of two more shots. This time however, the outcome is different than some of the other school shootings you may have heard about.
The staff members of the elementary school went into lockdown mode and followed the procedures they’d practiced and drilled multiple times. The staff knew what to do, and they did it in the face of true and present danger.
The secretary immediately sent out the signal for LOCKDOWN.
 Students were rushed into the building by staff members. Family members still present in the school yard were corralled by school support personnel. Teachers and staff members locked their internal doors and barricaded external doors. They huddled in their rooms away from the windows and out of the line of sight of the shooter. Hugging each other and the most solid wall in their classroom for safety.
Students were rushed into the building by staff members. Family members still present in the school yard were corralled by school support personnel. Teachers and staff members locked their internal doors and barricaded external doors. They huddled in their rooms away from the windows and out of the line of sight of the shooter. Hugging each other and the most solid wall in their classroom for safety.
Within seconds, two-thirds of the school was in lockdown. An then the shooter drove his pickup truck through the school fence and barreled toward the front entrance. The school custodian was busy getting parents into the school. He paused to look and see how far away the shooter was and, “looked the shooter in the eye as the shooter shot at him.” After the shot rang out, “The shooter was struggling with his weapon at this time. The gun appeared to be jammed, and he was having trouble loading ammunition.”
The gun jamming bought the staff, kids and parents precious seconds to finish their lockdown procedure. Everyone made it inside and all access to the school rooms and offices was now secure. The shooter, now fully loaded, entered the middle quad of the school 8 seconds later.
“The school secretary recognizing the threat made all the difference between 100 kids being around today and dozens being shot or killed. Those eight seconds were critical!”
The shooter was angry and frustrated and began to shoot into the classrooms and offices. In between shooting, the gunman tried to get into classrooms and the main office, but was unable to gain entry. He checked the bathroom, which was open but empty.
One 6 year old child was injured but survived and no one was killed. Six minutes after the shooting started, the gunman drove away. Hundreds of lives were changed forever, but everyone survived.
The Rancho Tehama Elementary School staff had practiced drills and executed lockdowns before, so even though they’ve never had an active shooter on campus, they knew what to do. It had become second nature.
The superintendent said, “The lockdown procedure was implemented flawlessly. The reason that we have a situation where I have one student injured on campus and nothing worse happening on campus is because of the heroic actions of all members of my school staff.”
Oxford High School in 2021
 The same techniques and lockdown training were used in Michigan at Oxford High School on November 30, 2021. Just after lunch, shots rang out inside the school in the main hallway. A 15 year-old student opened fire on his classmates. School staff, students and parents in the school that day followed the LOCKDOWN call and began to follow their training. “They had drilled this exact scenario so much that everyone knew exactly what to do next.”
The same techniques and lockdown training were used in Michigan at Oxford High School on November 30, 2021. Just after lunch, shots rang out inside the school in the main hallway. A 15 year-old student opened fire on his classmates. School staff, students and parents in the school that day followed the LOCKDOWN call and began to follow their training. “They had drilled this exact scenario so much that everyone knew exactly what to do next.”
In the hours after the shooting outside Detroit on Tuesday, Oakland County Sheriff Michael Bouchard said that without the measures taken by students, the tragedy would have been worse. “It is also evident from the scene that the lockdown protocols, training and equipment Oxford schools had in place saved lives.”
David Riedman, lead researcher on the K-12 School Shooting Database, said that the lockdown procedures that were deployed in Oxford, in which students sheltered and stayed out of sight, “absolutely saved lives.” The training that appeared to be on display in Michigan is similar to what students all over the country are taught, he said.
LOCKDOWNS took on new meaning during the heights of the COVID-19 Pandemic.
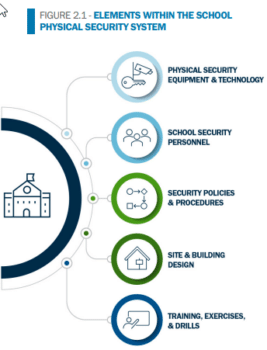 In the physical security world, lockdowns mean locking down a building so that no one can enter or leave for a period of time. The location stays locked down until an all-clear signal is given. This seems like a pretty straight forward premise. It is – IF you plan correctly and have the right systems and procedures in place to make a LOCKDOWN effective.
In the physical security world, lockdowns mean locking down a building so that no one can enter or leave for a period of time. The location stays locked down until an all-clear signal is given. This seems like a pretty straight forward premise. It is – IF you plan correctly and have the right systems and procedures in place to make a LOCKDOWN effective.
Kenton Brothers uses several access control platforms to make it easy and quick to lock down a school. When a panic button is pressed, all the school doors lock. And alarms and mass communications go out audibly through speakers and electronically through mobile devices and computers throughout the school.
One of our manufacturers, Gallagher, allows you to not only lock down the school, but also send out emergency messaging to any staff members or parents who are not at the school. This would allow them to stay away or help support police in their efforts to bring the situation under control. Gallagher also has the ability to remotely muster or check off each person from a pre-determined list to be sure 100% of the people on-site are accounted for. This is a powerful benefit in the aftermath of these incidents.
Police can also remotely operate and IP Surveillance cameras in the building to gain situational intelligence on the location of the shooter and the direction they’re headed. This is just one example of how these security systems can help support the training, processes and procedures during a Lockdown situation.
Kenton Brothers Systems for Security helps guide schools and other entities through the process of identifying risks around active shooters and the techniques in protecting your people, property and possessions. Kenton Brothers’ qualified consultants will perform a no cost physical security assessment with recommendations for security system components, processes and procedures that will help prepare your staff. Just give us a call.

 We’ve all heard that before. I typically don’t “rave” about a specific product but rather, I always try to find the solution that I believe will meet my client’s needs. By offering various options and products, I make sure that the customer has all the info they need to make an informed decision.
We’ve all heard that before. I typically don’t “rave” about a specific product but rather, I always try to find the solution that I believe will meet my client’s needs. By offering various options and products, I make sure that the customer has all the info they need to make an informed decision.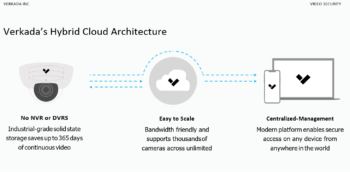
 Need intrusion detection? They’ve got that covered, plus a lot more. No more need to purchase and install multiple sensors that only do one thing. Get one sensor for motion, noise, and even environmental data like temperature, humidity, air quality, vape detection, PM2.5 and TVOCs. (If you don’t know these terms, we should probably talk…)
Need intrusion detection? They’ve got that covered, plus a lot more. No more need to purchase and install multiple sensors that only do one thing. Get one sensor for motion, noise, and even environmental data like temperature, humidity, air quality, vape detection, PM2.5 and TVOCs. (If you don’t know these terms, we should probably talk…)
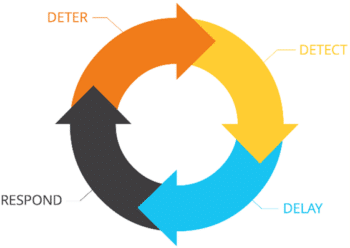
 Red Teams will test physical penetrations with your company’s physical assets (buildings, vehicles, networks, people) and measure the company’s response and how long it took to detect and act on those tests. They will measure the effectiveness of your policies and procedures and how they affect your deterrence and detection systems.
Red Teams will test physical penetrations with your company’s physical assets (buildings, vehicles, networks, people) and measure the company’s response and how long it took to detect and act on those tests. They will measure the effectiveness of your policies and procedures and how they affect your deterrence and detection systems.