Secure Credentials: Access Cards, Biometrics, Multi-Factor and Mobile
By Neal Bellamy, IT Director at Kenton Brothers
A couple of months ago, we talked about higher levels of security and Multi-Factor authentication for your computers and servers. Today, I’d like to bring that discussion back to Commercial Access Control.
Cards and Fobs are the number one method of gaining access to your building.
Card and fobs identify the “cardholder” with a string of bits (ones and zeros). Those bits are broken down to a “Facility Code” and a “Card Number”. The facility code is used to group the cards together or designate that card belongs to a certain building. Additionally, the cards weren’t originally encrypted, meaning that if you had the right technology, you could read any access card.
Even worse, on the common 26-bit access cards, there are only 256 unique facility codes and 65,536 unique card numbers. I’m pretty sure there are more than 256 companies using commercial access control. I don’t want to spend a lot of time talking about old technology… but I implore you: If you’re using true proximity cards (there are a lot of you out there), come talk with us about using an encrypted card that can’t be easily duplicated!
Okay, so if most cards aren’t that secure, how do we make things better?
Step 1: Encrypt the card
 Encryption for the cards and readers has been around for a while. As an example, HID iClass was introduced in 2002. The general premise is that the card is encrypted with a Public Key Infrastructure or PKI. Then the reader is loaded with the matching key. When the card is presented, the reader decrypts the credential and gives the access control system the unencrypted credential number. This number can still just be the same 26 bits as above, but only a reader with a matching key can read the credential.
Encryption for the cards and readers has been around for a while. As an example, HID iClass was introduced in 2002. The general premise is that the card is encrypted with a Public Key Infrastructure or PKI. Then the reader is loaded with the matching key. When the card is presented, the reader decrypts the credential and gives the access control system the unencrypted credential number. This number can still just be the same 26 bits as above, but only a reader with a matching key can read the credential.
Several technologies use encryption as a base layer of protection including HID iClass, Mifare, and FeliCA. There are several variations for each type.
Step 2: Increase the “uniqueness” of the card
Now we have a card that can’t be read by every reader in the world. However, there is still a good chance, with only 26 bits, that the exact sequence of bits exists on another card somewhere. The answer is simple… increase the number of bits. For every bit you add, you increase the possible card numbers by a power of 2. (16 bits = 65,535 possibilities, 17 bits = 131,072.)
The common 37-bit format allows for 65,536 facilities (16 bits) and 524,288 cardholders (19 bits). Although 37-bits allow for more variation in the sequence, there is still a chance of overlap. An even better solution is where your “Facility code” is registered and can never be duplicated.
Several Card manufacturers offer a program where your facility code is guaranteed to be unique. HID corporate 1000 is one such offering, Gallagher does this by default.
Biometrics
 Another strategy for creating a unique card is to not use a card at all. Biometrics fall into this category.
Another strategy for creating a unique card is to not use a card at all. Biometrics fall into this category.
The premise is that by providing a “reader” that reads a unique feature of a person and then sends the 1s and 0s to the access control system, the credential can be duplicated when all those things are combined in the right order. Hand scanners, fingerprint readers, vein readers, iris scanners, and facial recognition all fall into this category.
Biometric readers solve or circumvent many of the issues above. No encryption is needed between the credential (the person being read) and the reader because a person can’t be duplicated. The systems can even tell twins apart.
The downside to biometrics has been ease of use. Biometric systems require enrollment to create and store the “credential”. Early adopters also faced a reliability issue where the biometric was not recognized even is it was the right person. This false negative issue has mostly been resolved. With the right biometric system in place, I would argue that it is better than any card based system. It cannot be reasonably duplicated and cannot be lost or shared.
If we decide that we don’t want to use biometrics, we at least have a card that’s encrypted and probably (or guaranteed) unique. However, we still just have one form of authentication. If your card gets lost or stolen, someone has access to your facility until you can get it disabled. That’s where multi-factor authentication comes in.
Step 3: Multi-factor authentication
The multi-factor comes in many flavors. The oldest is “pin and prox” (The prox part can and should be encrypted and unique), where the person presents the credential and then enters a PIN on the reader. Biometrics can also be used as a second form of authentication. The user presents their credential and then presets their biometric. This form of biometric makes biometric even more secure than biometrics alone. Instead of the biometric matching anyone in the database, it has to match the same person that presented the card. Dual factor authentication doesn’t have to be on every door in your facility. It could be used for the exterior doors only, highly sensitive doors only, or any combination.
So far, we haven’t talked about the latest tech in credentials, which is using your phone as a card.
Using Your Phone as a Card
Multiple vendors offer a “mobile” Credential, but they all work similarly. An application on your phone receives an encrypted package that identifies who you are. When you present your phone to the reader, it sends the 1s and 0s to the access control. If this sounds exactly like a unique encrypted card… it is.
As an administrator, you can enforce the application to require a second form of authentication (Pin, Fingerprint, Face) in order to send the credential to the reader. Now you have a uniquely encrypted credential with two-factor authentication, without the headache of enrolling users in a biometric database. Mobile credentials aren’t compatible with all systems, and some systems offer easier management of mobile credentials than others. That said, mobile credentials are going to be the next wave of authentication. They provide ease of use and high security in a single package.
Want to know more? Give us a call!




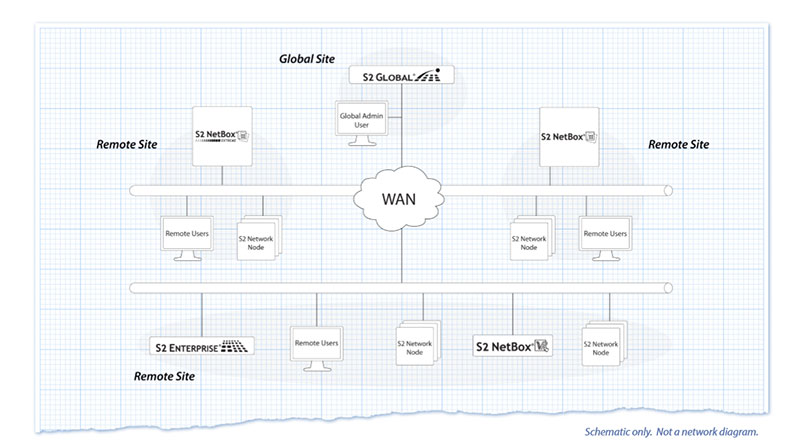
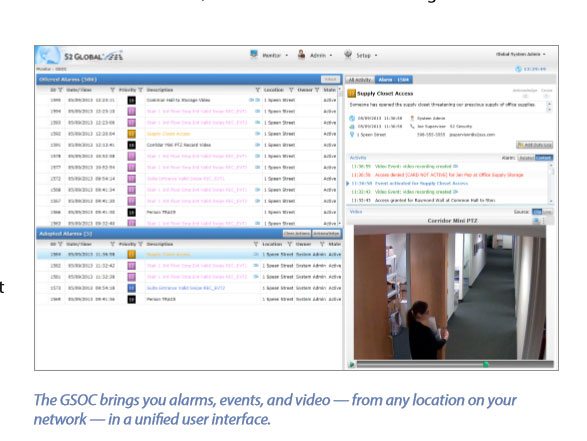
 This specific customer uses S2, an access control platform that Kenton Brothers supports and installs. This access control application made sense for the customer for many reasons, including the ability to monitor and manage multiple locations centrally. They can quickly build reports that run on a schedule, make security changes immediately that are reflected across the entire system, and build and administer global access levers that grant permissions across the entire organization.
This specific customer uses S2, an access control platform that Kenton Brothers supports and installs. This access control application made sense for the customer for many reasons, including the ability to monitor and manage multiple locations centrally. They can quickly build reports that run on a schedule, make security changes immediately that are reflected across the entire system, and build and administer global access levers that grant permissions across the entire organization.