Enlightened Security: The single greatest defense in a security system.
By Baer Halvorson, Security Systems Engineer at Kenton Brothers
 Randomized Control Experiments are considered to be one of the most effective ways to study cause-and-effect relationships. This method helps minimize biases by randomly assigning participants to either a treatment group (which receives the intervention) or a control group (which does not), ensuring that any differences between the groups can be attributed to the intervention itself, rather than other variables. This method is the gold standard in several major industries like medical intervention, psychology and more.
Randomized Control Experiments are considered to be one of the most effective ways to study cause-and-effect relationships. This method helps minimize biases by randomly assigning participants to either a treatment group (which receives the intervention) or a control group (which does not), ensuring that any differences between the groups can be attributed to the intervention itself, rather than other variables. This method is the gold standard in several major industries like medical intervention, psychology and more.
In 2018, working alongside the Mayor’s Office of Criminal Justice, the New York City Police Department, and the New York City Housing Authority, a research team called The Crime Lab, carried out a six-month randomized controlled trial at nearly 40 public housing developments with high crime levels. Half of these developments were outfitted with new, temporary street lights, while the other half remained unchanged.
Results from the study showed that there was a 39% reduction in index crimes (murder, rape, burglary, motor-vehicle theft, etc.). This percentage deduction in the world of criminological studies is an extreme result in deterring crime. While studies will show video surveillance and alarms reducing at a rate of 30-60% this is often attributed to one or two specific crimes, like robberies or burglary. 39% across all index crimes is a significant reduction and should be something that security consultants lead with.
Hardening Your Property With Lighting
If you are looking to harden your property (commercial or residential), even if you currently have a security system in place, you should consider adding lighting in areas that you might see activity. There are a couple of ways to implement lighting onto a property.
Triggered Lighting
Integrating lighting into something like motion or as a trigger to an alarm is a very effective way to create the appearance of presence. Motion lighting can often be very effective in giving the appearance that someone has turned the light on and caught the threat in the act. This extra bit of psychological strain on an attacker can cause them to instinctually flee the scene.
Lighting can also be activated by a triggered alarm; for example if the front of a property is being breached and a shock sensor goes off because the intruder is trying to kick in the front door, having an alarm trigger the lighting in an office to turn on, or click upstairs lighting on in a house can be a very effective way to deter an attempted intrusion.
Area Lighting
Parking lot lighting and adequate lighting around the property can help assure that threats or attackers can’t lie in wait or find a dark area to access the building from. Lighting around the property also gives surveillance cameras an advantage by bolstering the field of view, pushing visibility that much further. Landscape lighting can be the means to this end without sacrificing aesthetics.
Getting a consultation from a security integrator and taking their lighting recommendations to a landscaping company can be one way to assure that you are hardening a site without making it look like a prison.
Dynamic Lighting
There are also creative ways to use lighting to accomplish specific needs and provide solutions to a site. For instance you can use zoned threat-based activation in perimeter response lighting. This is where instead of just using motion sensors or alarm-triggered lighting, you can layer lighting activations to respond dynamically based on detected movement.
For example, motion on the outer fence line activates perimeter flood lights, moving closer to the building, additional higher-intensity security lights activate in stages, creating an escalating deterrence effect. Strobe and pulsing lights can also be used as a deterrent, whether that’s on the outside of the building to act as a natural surveillance and pull eyes to where the intruder is, or in interior situations to confuse and cause panic in an intruder.
Using different colors to communicate what is happening, using up-lighting at entrances to make it difficult to see in, but easy to see out and integrating lighting into building automation, access control or video surveillance are all ways that lighting can be used to strengthen a security system.
Let’s Talk Lighting!
Light is one of the most underrated and most research-proven, effective ways to deter criminal activity on a property. Access control, intrusion detection and video surveillance can all be improved when integrating these systems with light. When pondering on how to strengthen the security around your business or home, consider first if adding light can deter the criminal. We can help you lock in your lighting security solution. Give us a call!

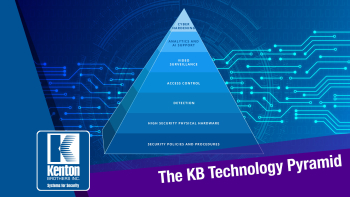

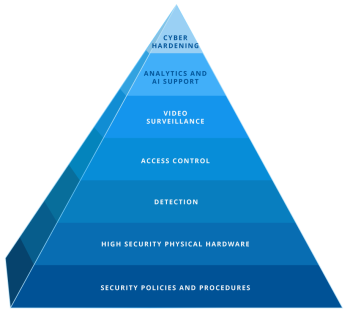
 Key Management Software, especially for larger companies, schools, and companies with multiple locations is a powerful way to keep track of all the keys floating around. The Key Management Software solution that we install and configure for our clients has the following capabilities:
Key Management Software, especially for larger companies, schools, and companies with multiple locations is a powerful way to keep track of all the keys floating around. The Key Management Software solution that we install and configure for our clients has the following capabilities: Over the past decade, companies within the physical security industry have come out with electronic key tracking boxes. The idea is to secure physical keys, manage who issued keys, and make sure keys that are taken are also returned. The electronic key management boxes we install include the following features:
Over the past decade, companies within the physical security industry have come out with electronic key tracking boxes. The idea is to secure physical keys, manage who issued keys, and make sure keys that are taken are also returned. The electronic key management boxes we install include the following features: Federal Agencies are continuously seeking robust solutions to safeguard their assets and personnel. Physical security plays a pivotal role in this endeavor, encompassing a range of measures to Protect People Property and Possessions from unauthorized access or harm. Among these measures, Identity, Credential, and Access Management (ICAM) systems integrated with Physical Access Control Systems (PACS) have emerged as a cornerstone for ensuring comprehensive security solutions. In this blog, we delve into the significance of having Certified Security Engineer Identity Professional (CSEIP) certified engineers managing ICAM PACS and explore real-world use cases across government agencies.
Federal Agencies are continuously seeking robust solutions to safeguard their assets and personnel. Physical security plays a pivotal role in this endeavor, encompassing a range of measures to Protect People Property and Possessions from unauthorized access or harm. Among these measures, Identity, Credential, and Access Management (ICAM) systems integrated with Physical Access Control Systems (PACS) have emerged as a cornerstone for ensuring comprehensive security solutions. In this blog, we delve into the significance of having Certified Security Engineer Identity Professional (CSEIP) certified engineers managing ICAM PACS and explore real-world use cases across government agencies. CSEIP certification is a testament to an engineer’s expertise in designing, installing, and maintaining advanced security systems, including ICAM PACS. Expertise in ICAM PACS Integration: CSEIP certified engineers possess in-depth knowledge of ICAM PACS technologies and standards, ensuring seamless integration with existing security infrastructure. Their expertise enables organizations to optimize system performance while maintaining compliance with regulatory requirements.
CSEIP certification is a testament to an engineer’s expertise in designing, installing, and maintaining advanced security systems, including ICAM PACS. Expertise in ICAM PACS Integration: CSEIP certified engineers possess in-depth knowledge of ICAM PACS technologies and standards, ensuring seamless integration with existing security infrastructure. Their expertise enables organizations to optimize system performance while maintaining compliance with regulatory requirements. The Department of Defense operates a vast network of facilities and installations worldwide, each requiring stringent access control measures to safeguard classified information and sensitive equipment. By employing CSEIP certified engineers to manage ICAM PACS, the DoD ensures that only authorized personnel gain access to restricted areas. These professionals design and implement multifactor authentication systems, incorporating biometric verification and smart card technology to enhance security while streamlining access for authorized personnel.
The Department of Defense operates a vast network of facilities and installations worldwide, each requiring stringent access control measures to safeguard classified information and sensitive equipment. By employing CSEIP certified engineers to manage ICAM PACS, the DoD ensures that only authorized personnel gain access to restricted areas. These professionals design and implement multifactor authentication systems, incorporating biometric verification and smart card technology to enhance security while streamlining access for authorized personnel.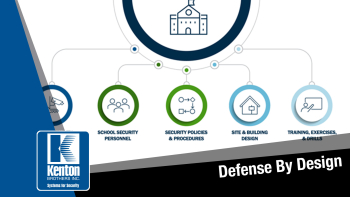 Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy.
Defense by design is a proactive approach to security that involves integrating security measures into the design and architecture of a physical space from the very beginning. Rather than treating security as an afterthought, it becomes an integral part of the overall design process. This approach aims to create layers of security that deter, delay, and ultimately thwart potential threats, providing businesses with a comprehensive defense strategy.