Introducing the Kenton Brothers CyPhy Security Plan
By Neal Bellamy, IT Director at Kenton Brothers
 Lately we’ve been talking a lot about Cyber Security. As with all types of commercial security, Cyber Security is best implemented as layered defense. In other words, a single key or credential won’t gain access to the entire kingdom. Also, like Physical Security, even a small oversight can become the launch point for a larger attack.
Lately we’ve been talking a lot about Cyber Security. As with all types of commercial security, Cyber Security is best implemented as layered defense. In other words, a single key or credential won’t gain access to the entire kingdom. Also, like Physical Security, even a small oversight can become the launch point for a larger attack.
For years, Kenton Brothers has been doing our part to help maintain security on your physical security devices. We use unique, randomly generated passwords for all of your devices. We make sure the firmware is updated at the time of install and implement other industry standard security best practices. While it’s a good start, there were still some gaps. So we are taking it to the next level.
The Kenton Brothers CyPhy Security Plan
Kenton Brothers is introducing our CyPhy Security Plan. Security is not a “set it and forget it” proposition. The security landscape, both Cyber and Physical, is always changing. It must be evaluated and re-evaluated to make sure the greatest number of holes are closed. With the CyPhy Security Plan we will still make sure your physical security systems are set up with the latest software, unique passwords, etc.
With this new program, we will follow the security hardening guides from all manufacturers, lock down all switch ports and ensure firewalls are set up and configured properly. After the initial installation is complete, we will be involved ongoing. We will monitor new releases from the manufacturer and alert you to any critical security related issues for your system. Furthermore, if you have the manufacturer’s software upgrade plan in place, we will remotely upgrade your systems and firmware every 6 months.
Where applicable, the CyPhy Security Plan includes:
• Using unique and randomly generated passwords for each purpose and user
• Upgrading firmware to the latest supported version
• Setting the server firewall to only allow authorized communications
• Locking switch ports to allow only authorized devices
• Monitoring manufacturer’s software for critical security alerts
• Enforcing encrypted communication wherever possible
• Disabling services, applications and ports not being used on devices
• Using unprivileged account for normal system usage
• Enforcing encrypted edge storage
• Filtering communication to local IP addresses only
• Disabling SD card slots not being used
• Following hardening guides from all installed manufacturers
We want the CyPhy Security Plan to dovetail into your existing cyber security plan.
If you have other cyber security initiatives already installed, like MFA, managed firewall, managed global service accounts, VPNs etc., we will help you integrate those into the physical security devices, networks and servers. We will also make suggestions to improve the security and operations of your systems. For example, deploying internet facing servers in the DMZ or connecting the security systems to Active Directory for ease of user management.
If you don’t have a cyber security plan in place, you can rest assured that the physical security devices will be protected and can even use our commercial security best practices to increase the security for your other systems.
Of course, there is no un-pickable/un-hackable lock, and there will never be a perfect defense for cyber attacks. Setting up a layered defense will significantly decrease the chances of a successful cyber attack on your network. The CyPhy Security Plan is our commitment to protect you whether the attack comes to your front door, or from the internet.
To learn more about our CyPhy Security Plan, please give us a call and we will discuss your current setup as well as the benefits of ramping up your security efforts.

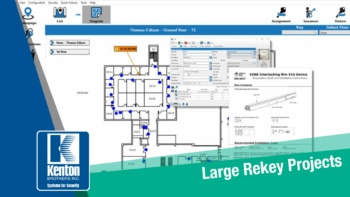 In a company or organization, it’s up to the organizational leaders to make sure that their people, property and possessions are kept safe and secure. Part of the strategy relies on the keying method used in the building(s). Kenton Brothers has been helping companies with large rekey projects since 1897.
In a company or organization, it’s up to the organizational leaders to make sure that their people, property and possessions are kept safe and secure. Part of the strategy relies on the keying method used in the building(s). Kenton Brothers has been helping companies with large rekey projects since 1897.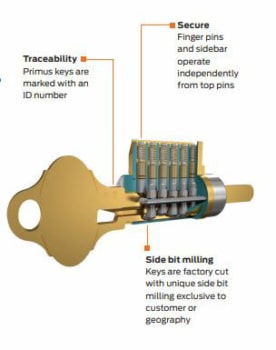 Setting up a master key system for one large facility, a campus environment with multiple buildings, or even a scenario where there are different buildings across the country can all be handled by setting up a master key system that allows for growth/expansion and the flexibility within that system to do so.
Setting up a master key system for one large facility, a campus environment with multiple buildings, or even a scenario where there are different buildings across the country can all be handled by setting up a master key system that allows for growth/expansion and the flexibility within that system to do so. So now that a master key system has been agreed upon, pricing approved, and materials are on order, what are the next steps? At this point, you will have chosen the path of how you will manage your key system; either internally or through a company such as Kenton Brothers. 80% of the effectiveness of the new keying system is in maintaining control of the keys!
So now that a master key system has been agreed upon, pricing approved, and materials are on order, what are the next steps? At this point, you will have chosen the path of how you will manage your key system; either internally or through a company such as Kenton Brothers. 80% of the effectiveness of the new keying system is in maintaining control of the keys! The install itself will begin with a Project Manager (PM) introducing you to the technicians who will be working on the project. The PM makes sure that once on site, the techs have clear expectations of their daily goals, know the location of material being stored onsite (if applicable), and any other project related questions they might have. Then the work begins!
The install itself will begin with a Project Manager (PM) introducing you to the technicians who will be working on the project. The PM makes sure that once on site, the techs have clear expectations of their daily goals, know the location of material being stored onsite (if applicable), and any other project related questions they might have. Then the work begins! CPTED is defined as “the proper design and effective use of the built environment that can lead to a reduction in the fear and incidence of crime and an improvement in the quality of life.” In other words, a CPTED analysis focuses on creating changes to the physical and social environment, that may reinforce positive behavior, with the goal of reducing opportunities for crime that may be inherent in the design of the built environment. CPTED is a multi-disciplinary approach to deterring criminal behavior.
CPTED is defined as “the proper design and effective use of the built environment that can lead to a reduction in the fear and incidence of crime and an improvement in the quality of life.” In other words, a CPTED analysis focuses on creating changes to the physical and social environment, that may reinforce positive behavior, with the goal of reducing opportunities for crime that may be inherent in the design of the built environment. CPTED is a multi-disciplinary approach to deterring criminal behavior. Natural Surveillance – the placement of physical features, activities, and people in a way that maximized visibility from the surrounding environment. This increases the threat of apprehension by taking steps to increase the perception that people can be seen.
Natural Surveillance – the placement of physical features, activities, and people in a way that maximized visibility from the surrounding environment. This increases the threat of apprehension by taking steps to increase the perception that people can be seen. That is a great question and one I hope to answer with this story. Eleven years ago, I had no idea what a security integrator was either. It wasn’t until I got involved in the security industry and saw firsthand what a Security Systems Integrator was and why they’re so important to so many organizations.
That is a great question and one I hope to answer with this story. Eleven years ago, I had no idea what a security integrator was either. It wasn’t until I got involved in the security industry and saw firsthand what a Security Systems Integrator was and why they’re so important to so many organizations. Within the first week of opening, late at night, we were able to see a person shoot out the glass entryway of our lobby and enter the building. He ran straight to the cash room and kicked in the door. We watched him go right to the safe we had installed and enter the code. He opened the door of the safe within two minutes of entering the building. And he was on his way out carrying an armful of envelopes full of cash and checks, dropping some along the way. It was obviously a person with inside knowledge of our systems and the location of the security devices.
Within the first week of opening, late at night, we were able to see a person shoot out the glass entryway of our lobby and enter the building. He ran straight to the cash room and kicked in the door. We watched him go right to the safe we had installed and enter the code. He opened the door of the safe within two minutes of entering the building. And he was on his way out carrying an armful of envelopes full of cash and checks, dropping some along the way. It was obviously a person with inside knowledge of our systems and the location of the security devices.