CyPhy Part 2 – How big of a problem do we have? Why we need Security Convergence today.
 By David Strickland, Vice President of Kenton Brothers
By David Strickland, Vice President of Kenton Brothers
The second of a three part series covering the Cybersecurity and Infrastructure Security Administrations (CISA) newest announcements around Security Convergence. Kenton Brothers Systems For Security hopes to help organizations understand this concept and adopt best practices for securing the Cyber-Physical Systems (CPS) currently deployed.
(Part 1 | Part 2 | Part 3 | Part 4)
In our last blog, we discussed what Security Convergence is and why it’s so important. In this blog, we will discuss how large the problem is and how many systems and verticals are affected by not having a converged security plan.
CISA Explains a Connected Environment
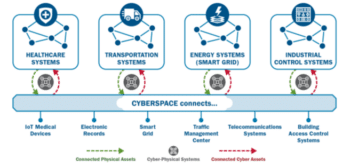 CISA Explains that the adoption and integration of Internet of Things (IoT) and Industrial Internet of Things (IIoT) devices have led to an increasingly interconnected mesh of cyber-physical systems (CPS), which expands the attack surface and blurs the once clear functions of cybersecurity and physical security.
CISA Explains that the adoption and integration of Internet of Things (IoT) and Industrial Internet of Things (IIoT) devices have led to an increasingly interconnected mesh of cyber-physical systems (CPS), which expands the attack surface and blurs the once clear functions of cybersecurity and physical security.
Juniper research reports that there are at least 46 billion IOT and IIOT devices on the connected network across the world. This number is expected to reach 125 billion by 2030. 18,788 are added every minute across the globe. There are approximately 6 IOT and IIOT devices per every human being on the planet. This will grow to approximately 12 per person (every man woman and child) by 2030.
The average number of devices per American household in 2021 was 10.
IOT Devices
 Beecham research provides a very useful look at the nature of IoT devices. (See graphic.)
Beecham research provides a very useful look at the nature of IoT devices. (See graphic.)
This trend makes up a large part of the world’s economy. However, for every device on a network there is a vulnerability introduced. This presents a unique problem for commercial, government and critical infrastructure entities. Each physical security device that is connected to the network is also an IoT device.
Every cell phone that connects to the network is also a vulnerability. Every surveillance camera, video doorbell, IP telephone, television and computer present there own unique threats and risks.
IoT and IIoT to be considered secure on a network will normally have updated firmware, current certificates, have default username and passwords changed, have an updated OS and have at least dual authentication. As you may deduce with 46 billion devices out there, this is quite the task. Especially when each of these devices may have different manufacturers and communication protocols to let organizations know that there is a new vulnerability or a patch that needs to be applied.
46 Billion Devices
 This 46 billion device reality, coupled with the fact that most organizations have siloed Physical and Cyber Security offices, has led to the vulnerabilities you hear about on the news every night. When the vulnerabilities affect critical infrastructure, such as energy or supply chain, the ramifications are far reaching.
This 46 billion device reality, coupled with the fact that most organizations have siloed Physical and Cyber Security offices, has led to the vulnerabilities you hear about on the news every night. When the vulnerabilities affect critical infrastructure, such as energy or supply chain, the ramifications are far reaching.
In our next blog, we will concentrate on breaking down the CISO and CSO silos and the specific steps an organization can take to reach security Convergence. Organizations with converged cybersecurity and physical security functions are more resilient and better prepared to identify, prevent, mitigate, and respond to threats. Convergence also encourages information sharing and the development of unified security policies across security divisions.
Kenton Brothers Systems for Security can help your organization understand this initiative and begin to help you close the gap. Please reach out with any questions.



Leave a Reply
Want to join the discussion?Feel free to contribute!