By Gina Stuelke, CEO of Kenton Brothers
 In our continuing series of educational posts, we love sharing the layered capabilities of access control systems.
In our continuing series of educational posts, we love sharing the layered capabilities of access control systems.
Anti-passback is a security feature in an access control system that prevents a user from passing their access credential (like a key card or mobile badge) to another person for unauthorized entry. It requires users to “exit” before they can “re-enter” and enforces a logical sequence of “in” and “out” events to prevent fraudulent or unauthorized use of credentials.
Capabilities
Prevents Credential Sharing
- Purpose: Ensures that access cards or credentials aren’t passed between individuals to bypass security.
- Benefit: Stops unauthorized access by enforcing that a badge used to enter must also be used to exit before it can be used again
Enhances Occupancy Tracking
- Purpose: Keeps accurate logs of who is inside the building or specific areas.
- Benefit: Useful for emergency evacuations, audits, or real-time occupancy monitoring (e.g., for energy efficiency or space planning).
Supports Compliance and Safety Protocols
- Purpose: Helps meet regulatory or internal policies related to controlled access.
- Benefit: Assists with compliance in industries requiring strict access monitoring (e.g., data centers, pharmaceuticals, finance).
Deters Tailgating and Piggybacking
- Purpose: Discourages people from entering secured areas by following others without scanning a credential.
- Benefit: Strengthens per-person authentication, especially at critical security points.
Improves Audit and Incident Response
- Purpose: Maintains a more accurate access log history.
- Benefit: Allows faster and more reliable investigations when security breaches or incidents occur.
Enables Logical Access Pairing
- Purpose: Links physical access to logical access (e.g., network login).
- Benefit: Ensures users are logged into systems only when they are physically present in the building.
Increases Operational Control
- Purpose: Forces users to follow defined traffic patterns (e.g., enter through the main lobby, exit through designated doors).
- Benefit: Helps manage crowd flow, security checkpoint coverage, and staffing.
Reduces Risk of Occupancy Overload
- Purpose: Limits the number of people in a given area at any one time.
- Benefit: Useful for high-security zones, labs, or rooms with occupancy limits (fire code, clean rooms, etc.).
Industry Segments
Here’s a breakdown of how different commercial industries apply anti-passback:
Corporate Office Buildings
- Use Case: Preventing employees from “buddy-badging” others into secured areas.
- Example: Employees must badge in and out of a high-security R&D lab or executive suite.
Data Centers
- Use Case: Enforcing strict audit trails for every entry and exit.
- Example: Technicians cannot badge into a server room unless they’ve properly exited previously, helping ensure tight compliance with SOC 2 or ISO 27001.
Manufacturing and Warehousing
- Use Case: Managing time and attendance and ensuring safe evacuation procedures.
- Example: Workers badge in at the start of a shift; anti-passback ensures only present workers are recorded in the building for safety drills or emergencies.
Education and Research Institutions
- Use Case: Controlling access to restricted labs or testing facilities.
- Example: Students or researchers must badge out of clean rooms before they can re-enter, reducing contamination and enforcing accountability.
Healthcare Facilities
- Use Case: Securing medication storage or surgical zones.
- Example: Staff cannot re-enter drug dispensary rooms without properly badging out — this ensures individual access is logged and traceable.
Commercial Real Estate (Shared Workspaces, etc.)
- Use Case: Preventing non-tenant access in shared environments.
- Example: Tenants or contractors cannot “lend” badges to guests or friends to gain unauthorized access
Using Anti-Passback to Acclimate Employees Back to the Office
Anti-passback can be a strategic tool to help ease employees back into office routines while reinforcing attendance, accountability, and a sense of structure. Here’s how it can be thoughtfully used for return-to-office (RTO) efforts:
Reinforces Routine and Presence
- Benefit: Employees scan in and out each day, re-establishing regular work habits and physical presence.
- Tactic: Use the entry/exit data to support hybrid schedules — e.g., ensuring employees are present on their designated in-office days.
Supports a Trust-But-Verify Approach
- Benefit: Encourages autonomy while gently enforcing accountability.
- Tactic: Managers can use reports to confirm that team members are showing up consistently without intrusive check-ins.
Helps With Space Planning and Resource Allocation
- Benefit: Anti-passback data shows how many employees are in the office and when.
- Tactic: Use this insight to adjust cleaning schedules, security staffing, HVAC needs, or shared desk booking systems.
Encourages Safe Occupancy Monitoring
- Benefit: Promotes a sense of security for employees concerned about overcrowding or emergency preparedness.
- Tactic: Let employees know their presence is logged for emergency evacuation and space management purposes — not micromanagement.
Integrates Seamlessly with Wellness or Perk Programs
- Benefit: Pair office attendance with perks (e.g., free lunches, parking passes, wellness credits).
- Tactic: Trigger incentives based on verified in-office days via anti-passback logs (e.g., “badge in 3 days this week, get a coffee gift card”).
Reduces Badge Sharing in Hybrid Environments
- Benefit: Prevents employees from “gaming” the system by having a friend badge in for them.
- Tactic: Makes it clear that presence tracking is tied to legitimate entry/exit behavior, not just one-time check-ins.
Builds Data for HR and Facilities Team
- Benefit: Provides objective usage metrics over time.
- Tactic: HR can use this data to tailor RTO policies, and Facilities can monitor office re-engagement trends by team or department
Tips for Effective Implementation of Anti-Passback Features
Use Hardware That Supports Directional Logic
- Install entry and exit readers at all controlled points.
- Pair with turnstiles or optical gates where feasible for enforcement.
Define Logical vs Physical Anti-Passback
- Hard Anti-Passback: Denies entry if proper exit hasn’t occurred — strict.
- Soft Anti-Passback: Logs a violation but allows access — good for training or early adoption phases.
Set Grace Periods or Exceptions
- Allow for system errors or emergencies by permitting admin override or setting time-based resets (e.g., after midnight)
Use with Video Surveillance Integration
- Cross-reference access logs with video footage to verify compliance and investigate tailgating.
Combine with Mobile Credentials or Biometrics
- Reduces badge sharing even further.
- Encourages personalized access — especially valuable in high-risk zones.
Train Users and Security Staff
- Make sure everyone understands how anti-passback works.
Provide clear signage and onboarding to avoid frustration.
Communication Tips to Ensure Success
- Frame anti-passback positively: as a way to ensure safety, comfort, and fairness, not as surveillance.
- Communicate clearly with employees about why it’s being implemented and how it benefits them.
- Provide self-service tools so employees can view their own access history and flag inconsistencies.
If you need help implementing Anti-passback technologies in your access control systems, we are here for you. Give us a call!
 Although cloud-based systems are getting more popular, many security systems still have on-premise servers at their heart. Servers, like all electronics, can fail and will need to be replaced. Servers also need updating in many ways. Sometimes they can show signs of issues overnight, and sometimes more slowly over time. The overnight issues are easier to detect, but the slower failures can be harder to detect, so I thought I would share some things to look out for.
Although cloud-based systems are getting more popular, many security systems still have on-premise servers at their heart. Servers, like all electronics, can fail and will need to be replaced. Servers also need updating in many ways. Sometimes they can show signs of issues overnight, and sometimes more slowly over time. The overnight issues are easier to detect, but the slower failures can be harder to detect, so I thought I would share some things to look out for. Server software, like all software, can have security or feature updates. Server software like Windows, Linux, MAC OS, etc., needs to be maintained to have the latest features and security patches. Depending on the settings, security patches will download and install themselves, but if you’re not sure, you should check with your IT team.
Server software, like all software, can have security or feature updates. Server software like Windows, Linux, MAC OS, etc., needs to be maintained to have the latest features and security patches. Depending on the settings, security patches will download and install themselves, but if you’re not sure, you should check with your IT team.
 For those of you using Genetec™ access control systems… did you know that Genetec offers Federation™? Federated licensing in Genetec’s security solutions provides organizations with a flexible, efficient, and scalable way to manage and optimize their security licenses across multiple locations or systems, ultimately improving resource allocation and reducing operational costs.
For those of you using Genetec™ access control systems… did you know that Genetec offers Federation™? Federated licensing in Genetec’s security solutions provides organizations with a flexible, efficient, and scalable way to manage and optimize their security licenses across multiple locations or systems, ultimately improving resource allocation and reducing operational costs.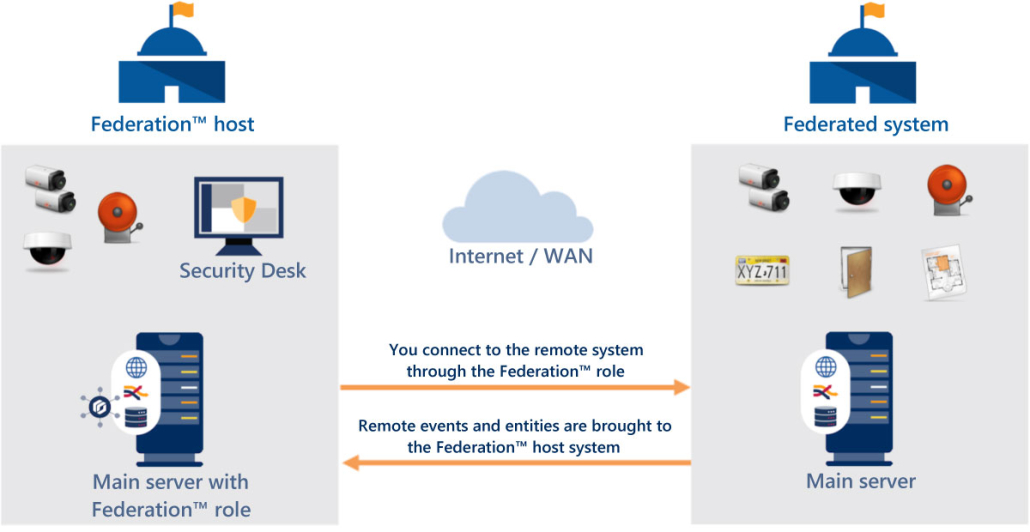
 In our continuing series of educational posts, we love sharing the layered capabilities of access control systems.
In our continuing series of educational posts, we love sharing the layered capabilities of access control systems. Overview
Overview


