Chain of Custody in Commercial Security
 By Ryan Kaullen, Field Services Manager at Kenton Brothers
By Ryan Kaullen, Field Services Manager at Kenton Brothers
Many of you know that our goal is to protect people, property, and possessions. Something that comes up related to this goal is Chain of Custody.
You may be wondering what Kenton Brothers has to do with Chain of Custody and how we would be involved. Unfortunately, part of the work we do in the commercial security industry is capturing evidence. This evidence comes in many forms. Evidence may include video surveillance recordings, security system audit trails and more. We capture this information to help protect companies from theft, fraud, and work place incidents. There are plenty of scenarios that result in law enforcement being involved.
What is Chain of Custody?
Chain of Custody is the documentation of chronological events related to an incident. Protection of how the evidence is handled, who handles it and more matters. The idea is that law enforcement needs to be able to review and use video and other forms of documentation as evidence in a trial or hearing.
A Recent Example for a Banking Client
 We recently received a Chain of Custody request from one of our banking clients. They had an event that they deemed legally significant and requested our help in documenting what had happened. They needed our help to get the video segments exported properly. They wanted footage from all of the cameras at one of their locations over the past 30 days. (That’s a good amount of video data!)
We recently received a Chain of Custody request from one of our banking clients. They had an event that they deemed legally significant and requested our help in documenting what had happened. They needed our help to get the video segments exported properly. They wanted footage from all of the cameras at one of their locations over the past 30 days. (That’s a good amount of video data!)
Our first step was to download the footage locally to external hard drives. The video data had to have password encryption. And the video footage had to be time stamped. We also had to fill out Chain of Custody paperwork.
On top of those requirements, the equipment and external drives couldn’t be left unsecured while we were downloading the video segments. We also had to be in an access-controlled room for audit purposes. It was crucial that we followed every step correctly to make sure their case against the accused is rock solid. We had to make sure the evidence we helped provide would not get thrown out due to Chain of Custody problems.
Once the video had been downloaded onto the drives, our technician had to hand deliver the hard drives to the bank’s lawyer and provide the Chain of Custody paperwork.
We Take Chain of Custody Seriously
 Chain of Custody is something Kenton Brothers takes extremely seriously for many reasons. One, we want to make sure we are providing our customers with a level of service and reliability they can count on. We also want to make sure law enforcement has what they need to support or refute claims. This is also a great example of how the commercial security systems we sell and support do what they’re supposed to do.
Chain of Custody is something Kenton Brothers takes extremely seriously for many reasons. One, we want to make sure we are providing our customers with a level of service and reliability they can count on. We also want to make sure law enforcement has what they need to support or refute claims. This is also a great example of how the commercial security systems we sell and support do what they’re supposed to do.
The reality is that you hope you never have to use footage, audits, etc. against someone working for you or coming in to your place of business. But when something does happen, you want to make sure you have the right systems in place to protect the people, property, and possessions of those who work there.
To learn more about how Kenton Brothers Systems for Security can protect you and your business, please give us a call.

 As in all security, it only takes one weak link to bring the whole castle down. You can have the best moat, the best turrets, and the best drawbridge. But if there was a secret, unguarded passage and the enemy discovered it, it could certainly lead to your demise. In the commercial access control world, the Weigand Protocol is that un-guarded secret passage.
As in all security, it only takes one weak link to bring the whole castle down. You can have the best moat, the best turrets, and the best drawbridge. But if there was a secret, unguarded passage and the enemy discovered it, it could certainly lead to your demise. In the commercial access control world, the Weigand Protocol is that un-guarded secret passage.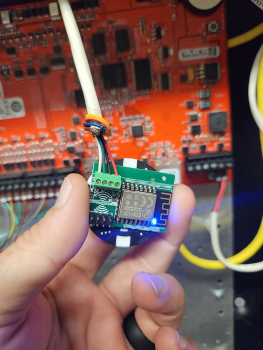 If you look online, you can find a board that can be installed between a reader and control panel that will intercept and log every access card being used. The board is smaller than a poker chip and can be installed behind a reader pretty easily. Once installed, it is powered by the door controller and is completely invisible to the reader and access control system. The attacker can leave it in place for a few days or a few weeks, while it collects every card read. Then, when they are ready, they can retrieve the list of cards from the built-in Wi-Fi interface. If the attacker only needs access to get into that single door, they can even “replay” the card number from the Weigand interface back to the door controller, probably granting access. If they need access to multiple doors, they could use the information to recreate identical cards to the ones you are using.
If you look online, you can find a board that can be installed between a reader and control panel that will intercept and log every access card being used. The board is smaller than a poker chip and can be installed behind a reader pretty easily. Once installed, it is powered by the door controller and is completely invisible to the reader and access control system. The attacker can leave it in place for a few days or a few weeks, while it collects every card read. Then, when they are ready, they can retrieve the list of cards from the built-in Wi-Fi interface. If the attacker only needs access to get into that single door, they can even “replay” the card number from the Weigand interface back to the door controller, probably granting access. If they need access to multiple doors, they could use the information to recreate identical cards to the ones you are using. I need to mention a side note here for
I need to mention a side note here for  When walking through Kenton Brothers Systems for Security, you will see this phrase prominently displayed on the walls throughout our building. Innovation is one of our core values and it’s a big reason we continue to provide remarkable physical security solutions for our customers… going on 126 years.
When walking through Kenton Brothers Systems for Security, you will see this phrase prominently displayed on the walls throughout our building. Innovation is one of our core values and it’s a big reason we continue to provide remarkable physical security solutions for our customers… going on 126 years. Facial recognition technology operates at impressive speeds, providing real-time identification results. This capability is especially valuable in high-traffic areas like airports, offices, and educational institutions, where quick and efficient access control is necessary. The system can process multiple faces simultaneously, reducing bottlenecks and ensuring smooth entry flows.
Facial recognition technology operates at impressive speeds, providing real-time identification results. This capability is especially valuable in high-traffic areas like airports, offices, and educational institutions, where quick and efficient access control is necessary. The system can process multiple faces simultaneously, reducing bottlenecks and ensuring smooth entry flows.



