Glazer’s Beer & Beverage Invests in Protecting Their People, Property and Possessions
We recently completed our fifth commercial security system installation for Glazer’s Beer & Beverage, this time in Waco, Texas.
electronic access control
We recently completed our fifth commercial security system installation for Glazer’s Beer & Beverage, this time in Waco, Texas.
The Kenton Brothers headquarters is based in Kansas City, MO but we do work across the United States to take care of our customers. Some of the most rewarding jobs are those close to home.
In 2021, Kenton Brothers was awarded a job for Bartle Hall Convention Center located in Downtown Kansas City, MO. What also makes this job special are two of the gentlemen involved in this project. Bill Harris of Kenton Brothers and David Mullins with Bartle Hall. Both Bill and David have been long standing pillars with their respective companies and both are going to be retiring in the near future. The job itself is being run by Zack Holden, one of Kenton Brothers’ Project Managers.

From left to right: Zack Holden (Kenton Brothers), David Mullins (Bartle Hall) and Bill Harris (Kenton Brothers)
The two main vendors involved in this project are Alarm Lock and Sargent Manufacturing.
The scope of the project is installing door hardware, new power supplies, Alarm Locks, coordinating new door & frame installs, new electrical work, and more across 75+ openings. This job has many tricky facets to it including coordination of sub-contractors, coordination of where we can work (different rooms are in use for events), keeping low voltage wires hidden, and even the coordination of parts being delivered. All of these variables add complexity to the project.
This is a door to an event space in Bartle Hall. They initially thought that we would have to bring wire mold down from the ceiling. For a cleaner and aesthetically pleasing install, we were able to design a solution by pulling cable in the drywall instead of having the cables exposed.
We added exit bars to dozens of doors for this project. This was required to get their facility up to current life safety code standards.
Large, complicated projects allow us to show what makes us different than our competition. Kenton Brothers, under one roof, has technicians that understand locksmith work, mechanical door hardware, commercial access control integration, commercial video surveillance and the ability to source and coordinate subcontractors. The end result is that our customers look to us as their single point of contact for large projects.
We want to thank Bartle Hall for trusting us for this project and we also want to give a farewell send off to Bill Harris who has been with Kenton Brothers 17+ years, you picked a great time to sell your largest project!
By David Strickland, Vice President of Kenton Brothers
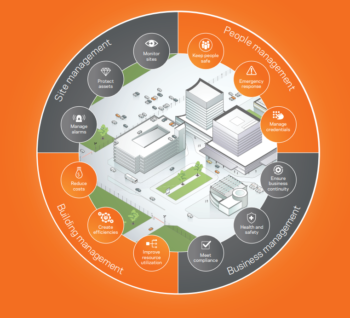 Wouldn’t it be incredible if you could manage your whole company or organization, including multiple sites, from one pane of glass? Wouldn’t it be awesome if you had one system to monitor security systems, alarms, building controls, power usage, employee certifications, risk compliance, regulatory inspections, vehicle maintenance, safety standards, attendance and visitor management? Well you can!
Wouldn’t it be incredible if you could manage your whole company or organization, including multiple sites, from one pane of glass? Wouldn’t it be awesome if you had one system to monitor security systems, alarms, building controls, power usage, employee certifications, risk compliance, regulatory inspections, vehicle maintenance, safety standards, attendance and visitor management? Well you can!
Kenton Brothers, as a part of its KB Advantage Program, can help companies, universities, school districts, municipalities, utilities and health care facilities reduce risk, increase job satisfaction, support compliance, and lower energy bills.
Imagine for a moment a true to life scenario using currently available technology.
Jenna is a high school teacher and likes to get to work early to start her day off right. As Jenna uses her smartphone to badge into the staff member parking lot or the employee entrance, the system goes to work turning on the power to her room, turning on her phone, adjusting the temperature in her room the the preset level. The system reminds Jenna that her teacher certification expires in 49 days and needs three more continuing education credits to be certified.
The system also sends her a message that there is a fire drill later that day.
The lighting to her classroom illuminates until she is inside her classroom, then switches off behind her.
This scenario is repeated multiple times throughout the morning, helping the system utilize only the power and resources necessary. Saving energy, helping to insure compliance and improving team member satisfaction.
Later that day, the fire drill starts and she’s alerted on her phone where to go. She and her students arrive safely at the muster point and she is able to check herself and her classroom in as safe and accounted for.
This is a true to life scenario that’s currently in place and can be integrated in your organization.
The Gallagher Command Centre integrates through active directory to your Human Resource database. It can manage which team members have the correct certifications to operate specialized machinery, have passed all safety or certification requirements, or whose licensing is about to expire.
In a cost-driven and energy-conscious business environment, you need to have confidence that your building management services are running correctly and not consuming power and resources when they aren’t required.
High-level communication between Command Centre and building management systems using the BACnet protocol provide opportunities for significant cost and energy savings. BACnet is a data communication protocol for building automation and control networks. It’s the national standard in over 30 countries, including the United States and Europe, and an International Organization for Standardization (ISO) global standards.
 Create a central repository for all alarm management to monitor and control your HVAC (heating, ventilation, and air conditioning) and other business management systems through Command Centre.
Create a central repository for all alarm management to monitor and control your HVAC (heating, ventilation, and air conditioning) and other business management systems through Command Centre.Kenton Brothers Systems for security offer a free security assessment to explore this solution. Give us a call today!

By Gina Stuelke, CEO of Kenton Brothers
Thank you to the Kansas Sheriffs’ Association for a great outing in Topeka this week at the 27th Annual Sheriffs’ Administration and Management Seminar (SAMS).
Everyone was happy to be with their peers and share camaraderie. We appreciate our partnership with Gallagher Security. They create solutions that make law enforcement and jail administrator’s lives easier and more efficient! Brinton Hallum, our detention specialist, works with the jail administrators and sheriffs to create a seamless solution that makes the correctional officers happy for many reasons.

 The new solution begins with a card access control system by Gallagher. This system is tied to a custom programmable logic controller for general jail control, including lighting and water control. We also implement a Milestone commercial video surveillance system with Axis cameras and intercoms for verbal communication. All systems operate over the detention centers network.
The new solution begins with a card access control system by Gallagher. This system is tied to a custom programmable logic controller for general jail control, including lighting and water control. We also implement a Milestone commercial video surveillance system with Axis cameras and intercoms for verbal communication. All systems operate over the detention centers network.
Please check out the solution we installed for Sheriff Murphy in Allen County, Kansas.
Special thanks to Alex Wojcik from Gallagher for lending his support and expertise at the event!
For more information send the problem solvers at Kenton Brothers a note or call 888-536-8661.
By Ryan Kaullen, Field Services Manager at Kenton Brothers
Keying Systems Series
Part 1: Importance of Master Key Systems and Restricted Keyways
Part 2: Restricted vs. Standard Keyways
Part 3: Peace of Mind with Keying Systems (this story)
 As a building owner, business owner or manager, you may wonder how the keys for your business are maintained. Are they being properly taken care of? How many copies are floating around? Has anyone lost one? Which of the employees have them? The list of questions goes on. The good news? The answers don’t have to be as complex as you think.
As a building owner, business owner or manager, you may wonder how the keys for your business are maintained. Are they being properly taken care of? How many copies are floating around? Has anyone lost one? Which of the employees have them? The list of questions goes on. The good news? The answers don’t have to be as complex as you think.
There are several checks and balances you can implement to have peace of mind with your access control systems.
A restricted keying system comes with many benefits. These include, but aren’t limited to, the following:
Kenton Brothers has run into the first example many times. We’ve had customers come in to request keys. We ask their name, and they weren’t on the authorized user list. So we turned them away. It was later found out that the person in question had been let go earlier in the week.
![]() As mentioned above, there is an authorized user list associated with all restricted key systems.
As mentioned above, there is an authorized user list associated with all restricted key systems.
What this does is stop employees or individuals from getting keys made, new cylinders created, etc. This is extremely beneficial for employees who’ve lost a key or have bad intentions at the facility.
Understanding how a key system can work to your benefit is also important.
A properly planned master key system can be set up that allows employees specific access to certain areas. This is an important component of securing your facility.
A great example of how this works is for one of our customers that owns a 10 floor building. Each floor has a different tenant, and each tenant should only have access to their floor. We created an overall master key system, created floor masters, and keyed the cylinders to flow traffic properly.
The result? Tenants knew they had secure spaces.
Kenton Brothers has been designing key systems since 1897.
Let us help you find peace of mind with your keying and security needs.
