Exciting News From Axis Communications – Device Manager Extend is a Major Innovation!
 By David Strickland, Vice President of Kenton Brothers
By David Strickland, Vice President of Kenton Brothers
Axis recently announced a huge innovation that will impact Axis camera users all over the world. Innovation is one of Kenton Brothers core values and we use the tagline “Innovate or Die” all the time. We enjoy seeing technology evolve and take the next step. In this case Axis took a huge leap!
Device Manager Extend
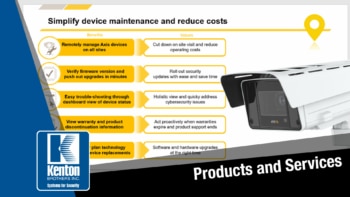
Axis rolled out the Axis Device Manager Extend tool that will help users worldwide manage all of their Axis Communications devices. It’s an easy-to-use utility tool that allows users to interact with AXIS devices in real time and make updates from a single dashboard. This is a huge advantage for enterprise level commercial surveillance systems.
 The New Axis Device Manager Extend will give you real time status awareness of all devices across all sites. It also gives you an inventory of all devices and if there are any anomalies. The dashboard provides warranty information and if components are reaching end of life. You can even determine the replacement model and start to budget for new equipment. The dashboard also allows you to export a list of all your devices including serial numbers, MAC addresses and model numbers.
The New Axis Device Manager Extend will give you real time status awareness of all devices across all sites. It also gives you an inventory of all devices and if there are any anomalies. The dashboard provides warranty information and if components are reaching end of life. You can even determine the replacement model and start to budget for new equipment. The dashboard also allows you to export a list of all your devices including serial numbers, MAC addresses and model numbers.
Device Status
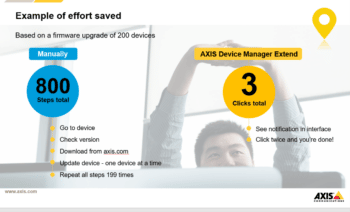
A user can get real time device status including firmware, cybersecurity status and how applications are working on the device. You can access your Axis devices remotely, giving you centralized control of your security platform. You can discover the firmware of your devices and then push the updates to your entire platform in three clicks. (This used to be a device-by-device task that would take days or weeks to accomplish.) You can remotely fix many problems without the expense of rolling at truck.
Have you ever updated a device’s firmware and found a problem?
 Axis Device Manager Extend will also allow you to roll back firmware updates if an issue pops up. Before you upgrade, the manager will analyze your system and make recommendations on what firmware versions to use during the upgrade.
Axis Device Manager Extend will also allow you to roll back firmware updates if an issue pops up. Before you upgrade, the manager will analyze your system and make recommendations on what firmware versions to use during the upgrade.
How about Cybersecurity Control?
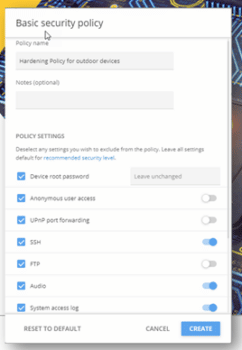
You can now control device settings remotely for the entire platform. You can require password changes, turn off anonymous access, turn off port forwarding and log every interaction with every device. Using the tool will ensure and maintain compliance and consistency across your systems. (The key word being consistent.)
The best news about this tool is that it’s available today! Whether you’re an IT Professional trying to stay on top of a 6,000 camera commercial video surveillance system or a business owner trying to make sure your 16 camera system isn’t creating a cybersecurity risk, this tool is for you!
Please give us a call to learn how you can deploy this amazing, innovative tool today.







 Access control is typically a Ho-Hum discussion. Who gets access to your doors? When during the day do they get access? Do you want pictures on your badges? What doesn’t get discussed often is how access control can make it easier to manage your facility. Ease of use is vastly different across access control platforms. Your decision on access control software can significantly affect how you manage your facility!
Access control is typically a Ho-Hum discussion. Who gets access to your doors? When during the day do they get access? Do you want pictures on your badges? What doesn’t get discussed often is how access control can make it easier to manage your facility. Ease of use is vastly different across access control platforms. Your decision on access control software can significantly affect how you manage your facility!
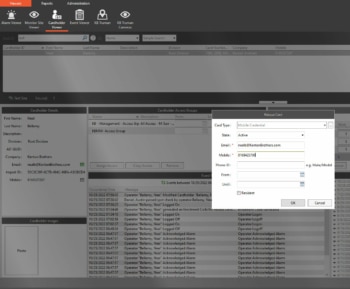

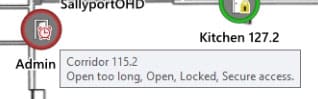
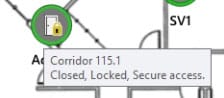
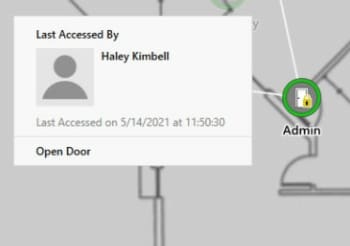

 So, you have your network secure? Great! Now what kind of hardware are you using? Something as simple as a plunger switch on a cabinet can be bypassed and let someone short the lock to the back door. Do your cameras still use ‘username’ and ‘password’ for the login? Did you put resistors in line with the reader you hung on the wall? Lastly, did you leave the keys in the cabinet lock because Steve keeps losing them? Get Steve a retractable key chain and make sure your hardware is as secure as your network.
So, you have your network secure? Great! Now what kind of hardware are you using? Something as simple as a plunger switch on a cabinet can be bypassed and let someone short the lock to the back door. Do your cameras still use ‘username’ and ‘password’ for the login? Did you put resistors in line with the reader you hung on the wall? Lastly, did you leave the keys in the cabinet lock because Steve keeps losing them? Get Steve a retractable key chain and make sure your hardware is as secure as your network. This one is the hardest. People are predictable… until they’re not. Training staff and enforcing policies can be difficult. That’s why having a system that can help you mitigate the exposures people are sure to cause is a must.
This one is the hardest. People are predictable… until they’re not. Training staff and enforcing policies can be difficult. That’s why having a system that can help you mitigate the exposures people are sure to cause is a must.