Don’t let a secret tunnel topple your castle. OSDP encryption is crucial to your commercial security.
By Neal Bellamy, IT Director at Kenton Brothers
 As in all security, it only takes one weak link to bring the whole castle down. You can have the best moat, the best turrets, and the best drawbridge. But if there was a secret, unguarded passage and the enemy discovered it, it could certainly lead to your demise. In the commercial access control world, the Weigand Protocol is that un-guarded secret passage.
As in all security, it only takes one weak link to bring the whole castle down. You can have the best moat, the best turrets, and the best drawbridge. But if there was a secret, unguarded passage and the enemy discovered it, it could certainly lead to your demise. In the commercial access control world, the Weigand Protocol is that un-guarded secret passage.
The Weigand Protocol
The Weigand protocol has been used since the 1980s and is named after the Weigand Effect. The Weigand protocol is used to detect the 1’s and 0’s sent from a commercial security reader to the access control panel. (To be clear, there are two separate transmissions that happen when you present a card to a reader.)
The first communication is from the card to the reader itself. This transmission can be protected by the card technology being used. Both the card and the reader have to have the same technology to be compatible. iClass®, Mifare®, and Felica® are examples of card technology where the transmission is encrypted between the card and reader. Proximity is another type of card technology, but the transmission is not encrypted
The second transmission is from the reader to the door controller. With very few exceptions, the Weigand protocol has been the method to support this transmission. If you have an encrypted card technology (and you should) it’s like encoding a message with the Enigma machine, then translating back to plain German and sending the un-encrypted message on horseback to its next location. If the courier gets intercepted while the message is unencrypted… all of that amazing security of the message has been wasted. If someone could change the message without you knowing, you might even make the wrong decision. You might think this is CIA/MI5 material, but it is way more accessible than you think.
Enter the $25 Weigand interface.
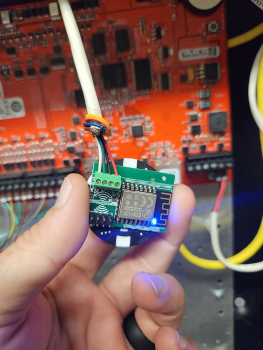 If you look online, you can find a board that can be installed between a reader and control panel that will intercept and log every access card being used. The board is smaller than a poker chip and can be installed behind a reader pretty easily. Once installed, it is powered by the door controller and is completely invisible to the reader and access control system. The attacker can leave it in place for a few days or a few weeks, while it collects every card read. Then, when they are ready, they can retrieve the list of cards from the built-in Wi-Fi interface. If the attacker only needs access to get into that single door, they can even “replay” the card number from the Weigand interface back to the door controller, probably granting access. If they need access to multiple doors, they could use the information to recreate identical cards to the ones you are using.
If you look online, you can find a board that can be installed between a reader and control panel that will intercept and log every access card being used. The board is smaller than a poker chip and can be installed behind a reader pretty easily. Once installed, it is powered by the door controller and is completely invisible to the reader and access control system. The attacker can leave it in place for a few days or a few weeks, while it collects every card read. Then, when they are ready, they can retrieve the list of cards from the built-in Wi-Fi interface. If the attacker only needs access to get into that single door, they can even “replay” the card number from the Weigand interface back to the door controller, probably granting access. If they need access to multiple doors, they could use the information to recreate identical cards to the ones you are using.
Placing one of these Weigand interfaces at the front door of a facility could be devastating for your building security.
OSDP = Open Supervised Device Protocol
There is hope. The answer is to also encrypt communication from the reader to the panel.
Open Supervised Device Protocol (OSDP) aims to do this and more. OSDP has been an international standard since 2020 and is all about encrypted communications. It also adds bi-directional communication with readers (know when readers are offline/disconnected), allowing more than one reader on a port, etc. Over the last couple of years, board and reader manufacturers have been implementing OSDP into access control hardware. While not every manufacturer or model supports OSDP, support is growing. For most systems, OSDP can be added on a door-by-door basis. You can convert high-profile doors to OSDP while waiting to upgrade low-risk doors if your budget doesn’t support an all-or-nothing approach.
 I need to mention a side note here for Gallagher. When I first encountered Gallagher security products in 2010, they were already using their HBUS technology for their readers. While Gallagher supports OSDP, the HBUS technology provides very similar benefits as OSDP like encryption, bi-directional communication, and multiple readers on a port… but HBUS has been doing it for much longer. An additional benefit with Gallagher HBUS and readers is being able to create your own card encryption key easily. This means that no other organization in the world will have a card that can be read on your Gallagher system. This is not a requirement for Gallagher, but it is super simple to do and is part of our standard procedures when installing a new Gallagher system.
I need to mention a side note here for Gallagher. When I first encountered Gallagher security products in 2010, they were already using their HBUS technology for their readers. While Gallagher supports OSDP, the HBUS technology provides very similar benefits as OSDP like encryption, bi-directional communication, and multiple readers on a port… but HBUS has been doing it for much longer. An additional benefit with Gallagher HBUS and readers is being able to create your own card encryption key easily. This means that no other organization in the world will have a card that can be read on your Gallagher system. This is not a requirement for Gallagher, but it is super simple to do and is part of our standard procedures when installing a new Gallagher system.
Transmitting card numbers from the reader to your access control panels might be the chink in your access control’s armor. As part of our security standard, KB will make sure you are using encrypted communication from the card all the way to the access control system.
If you need help evaluating the next steps in your access control setup or how to get started on the right foot, let us know! Just give us a call and we will be happy to help.

 When walking through Kenton Brothers Systems for Security, you will see this phrase prominently displayed on the walls throughout our building. Innovation is one of our core values and it’s a big reason we continue to provide remarkable physical security solutions for our customers… going on 126 years.
When walking through Kenton Brothers Systems for Security, you will see this phrase prominently displayed on the walls throughout our building. Innovation is one of our core values and it’s a big reason we continue to provide remarkable physical security solutions for our customers… going on 126 years. Facial recognition technology operates at impressive speeds, providing real-time identification results. This capability is especially valuable in high-traffic areas like airports, offices, and educational institutions, where quick and efficient access control is necessary. The system can process multiple faces simultaneously, reducing bottlenecks and ensuring smooth entry flows.
Facial recognition technology operates at impressive speeds, providing real-time identification results. This capability is especially valuable in high-traffic areas like airports, offices, and educational institutions, where quick and efficient access control is necessary. The system can process multiple faces simultaneously, reducing bottlenecks and ensuring smooth entry flows.



 A customer, Rich, recently came to us with a problem. His access control environment has three generations of
A customer, Rich, recently came to us with a problem. His access control environment has three generations of  Creating a training wall with four different boards and two doors per board would take up a lot of room and be fairly costly. We ended up creating two demonstration doors where they could be switched to one of the four access control boards. One of the doors we set up as fail-secure, meaning the door is still locked if power is removed. The other door was set up as fail-safe, meaning the door is unlocked when the power is removed. We did this to demonstrate the different ways of connecting the power supply and to provide a realistic scenario that might be found in the field.
Creating a training wall with four different boards and two doors per board would take up a lot of room and be fairly costly. We ended up creating two demonstration doors where they could be switched to one of the four access control boards. One of the doors we set up as fail-secure, meaning the door is still locked if power is removed. The other door was set up as fail-safe, meaning the door is unlocked when the power is removed. We did this to demonstrate the different ways of connecting the power supply and to provide a realistic scenario that might be found in the field.