Upgraded Security with Alcatraz AI Facial Recognition: Your FACE is your CREDENTIAL!
By Gina Stuelke, CEO of Kenton Brothers
 Overview
Overview
One of our customers, a major player in financial services, transportation logistics, and international trade, wanted to step up their physical security game. With a growing team and increasing security needs, the company needed an advanced access control system that was both seamless and highly secure. By rolling out Alcatraz AI’s facial recognition access control, we helped this customer create a hassle-free, high-tech security solution that improves efficiency and keeps their facilities safe.
Challenges
Before bringing in Alcatraz AI, this customer faced a few key security issues:
- Key Card Hassles: Traditional access cards and codes were easy to lose, steal, or misuse.
- Slow Entry Process: Employees sometimes got stuck at entry points due to lost or forgotten credentials.
- Growing Pains: As the company expanded, it needed a security system that could scale easily.
- Hygiene Concerns: In a post-pandemic world, a touch-free access solution was a must-have.
Solution
Kenton Brothers introduced Alcatraz AI’s facial recognition technology to upgrade its access control system.
Here’s what they got:
- Effortless Access: Employees could simply walk up, get recognized, and enter—no more fumbling for badges.
- Stronger Security: AI-driven facial recognition ensured that only authorized individuals could gain entry.
- Easy Integration: The system worked smoothly with existing security setups, avoiding major disruptions.
- Scalability: The technology easily adapts as the company continues to grow.
- Touch-Free Convenience: Eliminating the need for physical touchpoints improved hygiene and safety.
Implementation and Results
Our customer rolled out Alcatraz AI at key entry points in its headquarters. We played a crucial role in the successful installation and programming of the new Alcatraz system, ensuring a seamless transition with minimal disruption to daily operations. Our expertise in access control allowed our customer to quickly and effectively deploy the technology. The process included:
- Planning & Customization: Security teams worked with Alcatraz AI and Kenton Brothers to identify priority areas and fine-tune the system.
- Professional Installation: Kenton Brothers handled the installation and programming, ensuring the system functioned flawlessly from day one.
- Smooth Deployment: The solution was seamlessly integrated with existing infrastructure, requiring minimal employee training.
- Ongoing Optimization: The company used real-time data and analytics to refine security measures post-launch.
The results spoke for themselves:
- Drop in Credential Issues: Reduction in lost or stolen badges causing security headaches.
- Faster Entry Times: Employees could get to work more quickly and efficiently.
- Better Security Insights: Real-time monitoring helped security teams track access patterns and prevent potential threats.
- Happier Employees: A smooth and secure entry experience boosted workplace convenience.
Conclusion
With Alcatraz AI’s facial recognition system in place, we helped our customer significantly improve their security while making daily operations smoother. We made sure that the installation and deployment were efficient and hassle-free. The technology’s ability to provide secure, touchless, and scalable access control helped future-proof the company’s security infrastructure. As our customer continues to grow, they’re confident that Alcatraz AI and our team at Kenton Brothers will keep up with their evolving needs.
Learn more about biometric technologies in the Alcatraz.ai Resource Center.

 The IP video surveillance industry has been evolving rapidly, driven by advancements in artificial intelligence (AI), cybersecurity, edge computing, and cloud storage. As security concerns continue to grow, organizations are investing in cutting-edge surveillance technology to enhance their capabilities. Among the top players in this space, Hanwha Vision (formerly Hanwha Techwin) and Axis Communications lead the camera market, while Genetec and Milestone dominate in video management software (VMS).
The IP video surveillance industry has been evolving rapidly, driven by advancements in artificial intelligence (AI), cybersecurity, edge computing, and cloud storage. As security concerns continue to grow, organizations are investing in cutting-edge surveillance technology to enhance their capabilities. Among the top players in this space, Hanwha Vision (formerly Hanwha Techwin) and Axis Communications lead the camera market, while Genetec and Milestone dominate in video management software (VMS). Often our security systems are in a defensive position. A Video Management System can be used to find out what happened forensically. Our Access Control Systems are used to deny access to sensitive areas or equipment. Gunshot detection systems detect the gunshot after it happens. I don’t mean to say these systems aren’t important. In fact, they’re the foundation that is required. Without these systems, there is no option of doing anything better. However, once you have the foundation, there are ways to move to the offensive position.
Often our security systems are in a defensive position. A Video Management System can be used to find out what happened forensically. Our Access Control Systems are used to deny access to sensitive areas or equipment. Gunshot detection systems detect the gunshot after it happens. I don’t mean to say these systems aren’t important. In fact, they’re the foundation that is required. Without these systems, there is no option of doing anything better. However, once you have the foundation, there are ways to move to the offensive position. Over the last decade, we’ve experienced two major types of convergence: Physical security and IP networks, and then came Physical security and Cyber security.
Over the last decade, we’ve experienced two major types of convergence: Physical security and IP networks, and then came Physical security and Cyber security.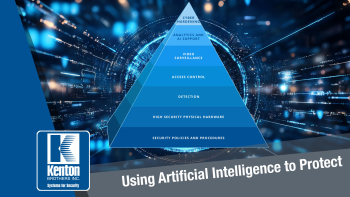 In line with our core values of continuous learning, innovation and customer focus, as a physical security integrator, Kenton Brothers is increasingly leveraging AI technology to enhance security operations, improve efficiency, and deliver advanced solutions to our clients.
In line with our core values of continuous learning, innovation and customer focus, as a physical security integrator, Kenton Brothers is increasingly leveraging AI technology to enhance security operations, improve efficiency, and deliver advanced solutions to our clients.