By David Strickland, Vice President of Kenton Brothers
Welcome to Eldoria
 In a distant medieval realm, nestled between rolling hills and dense forests, there existed a peaceful village named Eldoria. The villagers, content in their simple lives, lived in harmony with the land. However, peace is a fragile thing, and the tranquility of Eldoria was shattered when rumors of marauding bandits spread like wildfire. Travelling caravans spoke of their perils and the destruction left behind by these marauders.
In a distant medieval realm, nestled between rolling hills and dense forests, there existed a peaceful village named Eldoria. The villagers, content in their simple lives, lived in harmony with the land. However, peace is a fragile thing, and the tranquility of Eldoria was shattered when rumors of marauding bandits spread like wildfire. Travelling caravans spoke of their perils and the destruction left behind by these marauders.
These bandits, known for their cunning and ruthlessness, struck fear into the hearts of the villagers. As the threat loomed larger with each passing day, the village elders gathered to seek a solution. It was then that a wise elder, known for his sagacity, spoke of a distant land named Kansas City where Kenton Brothers Systems for Security thrived. This organization, led by the great Lady Gina of Lee’s Summit, was known across the land as the protector of the realm.
Emissaries were dispatched to seek the aid of Lady Gina and Kenton Brothers, and after a long and perilous journey, they arrived at the gates of the city to visit the renowned security experts. The village’s plight reached the ears of Lady Gina and her band of Knights. It was agreed that something must be done to help the people of Eldoria.
The emissaries returned to Eldoria with the good news.
The villagers were filled with hope as they eagerly awaited the arrival of the Kenton Brothers Knights that promised to fortify their village and repel the bandit threat. A caravan bearing the emblem of Kenton Brothers arrived in Eldoria. The villagers marveled at the advanced equipment and the skilled craftsmen who had journeyed to their humble abode.
The head of the caravan, a seasoned security expert named Sir Neal of Systems addressed the villagers.
“Fear not, good people of Eldoria, Lady Gina has heard your pleas for help. Kenton Brothers stands ready to fortify your village against the menace that plagues you,” Sir Neal proclaimed. The crowd cheered as Sir Neal dispatched the Knights of Kenton Brothers across the village to assess the current state of defenses.
Gathering that evening in the Great Tent of Engineering, the knights reported all levels of defensive capabilities and the changes need to repel the great horde of bandits quickly closing in on the village. The Eldoria leaders grew fearful as they heard the reports and understood how poorly the city was prepared for what was to come.
All Eldorian hearts were heavy until Sir Ryan of Service loudly proclaimed that there was no task too great for Kenton Brothers Systems for Security and that working together with Eldoria, great works could be done and they will be prepared to face the threat! The Eldorians were filled with confidence from the Knight’s enthusiastic statement and cheered their support! Laboring through the night, assisted by oil lamps, Kenton Brothers and the Eldoria leaders created a plan that would preserve their village and surrounding areas.
And so, the work began.
The craftsmen from Kenton Brothers labored day and night, constructing a formidable perimeter around the village. Towering walls were erected, equipped with state-of-the-art surveillance systems that could detect the slightest movement in the surrounding forests. Access control points were installed, ensuring that only those with the villagers’ best interests at heart could enter. Village elders were trained in recognizing threats and identifying counter measures. They in turn trained other villagers on situational awareness and what steps to take to keep their crops, livestock and family safe.
As the villagers observed the transformation, a newfound sense of security enveloped Eldoria. The once fearful whispers were replaced with hopeful conversations, and the children played freely in the meadows once again.
The Bandits
The bandits, hackers, thieves and nare do wells have had an easy time raiding villages throughout the land. Running unopposed across the lands, growing rich in spoils and reputation. Many times raiding abandoned villages as the people would run away in fear the night before. The Bandits numbers growing daily as evildoers all over the realm sought out easy payoffs.
Unaware of the changes taking place in Eldoria, the bandits planned their next raid. Little did they know that Eldoria was no longer an easy target. The night they chose to strike was a dark and bitter night.
As the bandits approached under cover of darkness, they began to set off perimeter alarms. The Eldorian villagers were alerted and immediately sprang to action. Alerts were repeated and everyone assumed their given role and position on the defensive line. All of this before the bandits even knew they had been detected.
The bandits launched their first attack! The bandits encountered an impenetrable barrier – the walls of Eldoria fortified by Kenton Brothers Systems for Security. As the bandits futilely attempted to breach the village, the surveillance systems alerted the villagers and the guards stationed at strategic points. Sir Neal of Systems, leading the defense, rallied the villagers to stand united against the common enemy. The bandits, disoriented and outmatched, were forced to retreat into the darkness from whence they came.
Enraged, the leader of the bandits decided to try again by attacking the rear defenses. There stood Sir Ryan and his Eldorian defenders waiting on the bandits as the surveillance system tracked their movements through the forest. All night long, wave after wave of bandits crashed unsuccessfully against the defenses. Cheers arose at dawn’s light as the bandits scurried into the forest in defeat.
Huzzah!
Word of Eldoria’s successful defense spread far and wide, reaching the ears of neighboring villages facing similar threats. The reputation of lady Gina and Kenton Brothers Systems for Security soared, and emissaries from other realms sought their expertise to fortify their own villages against banditry and other perils.
Emboldened by their success, the villagers of Eldoria embraced their newfound security with gratitude. The partnership forged with Kenton Brothers became a symbol of hope, illustrating how advanced security solutions could safeguard even the most vulnerable communities.
As the years passed, Eldoria thrived under the watchful eyes of the Kenton Brothers and their band of Knights and craftsmen. The villagers no longer lived in constant fear, and the bandits, aware of the impenetrable defense, dared not approach the fortified village. The people of Eldoria flourished, their once humble abode transformed into a beacon of safety and prosperity across the lands.
And so, the tale of Eldoria became a legend passed down through generations – a testament to the transformative power of Kenton Brothers Systems for Security in a medieval realm. The villagers lived in peace, secure in the knowledge that their fortified village was a shining example of how innovation and collaboration could triumph over adversity.
If your village is in danger, please send a rider at once!
 In a lot of ways, the requirements to install a commercial security camera are usually pretty easy to accomodate. 90% of the time we need just one wire that is smaller than your pinky finger. We can install that wire inside, outside, in conduit, or even stretch it between poles. We used to have limits on how far away a camera could be installed, but with new wire technologies and PoE extenders (Power over Ethernet), distance is rarely an issue. However, there are still times when you just can’t get a wire to where you want to install a camera.
In a lot of ways, the requirements to install a commercial security camera are usually pretty easy to accomodate. 90% of the time we need just one wire that is smaller than your pinky finger. We can install that wire inside, outside, in conduit, or even stretch it between poles. We used to have limits on how far away a camera could be installed, but with new wire technologies and PoE extenders (Power over Ethernet), distance is rarely an issue. However, there are still times when you just can’t get a wire to where you want to install a camera. Solar power is not a new thing. It’s been around for decades. The hard part about solar is not the technology or the calculations, the hard part about solar is deploying it. Solar panels work by charging a bank of batteries when the sun is out and then using the batteries to power equipment when it’s dark.
Solar power is not a new thing. It’s been around for decades. The hard part about solar is not the technology or the calculations, the hard part about solar is deploying it. Solar panels work by charging a bank of batteries when the sun is out and then using the batteries to power equipment when it’s dark.


 Where do you feel safe? Home? Work? In your car?
Where do you feel safe? Home? Work? In your car? Is the congregation and board willing to make these changes?
Is the congregation and board willing to make these changes? 5 MP video with two-way audio.
5 MP video with two-way audio. The AXIS W110 Body Worn Camera provides security personnel with a powerful tool for documenting incidents and enhancing situational awareness. Compact and lightweight, this body-worn camera can be easily attached to uniforms or vests, enabling hands-free operation without impeding mobility.
The AXIS W110 Body Worn Camera provides security personnel with a powerful tool for documenting incidents and enhancing situational awareness. Compact and lightweight, this body-worn camera can be easily attached to uniforms or vests, enabling hands-free operation without impeding mobility. The AXIS D2210-VE Radar represents a paradigm shift in perimeter protection, leveraging advanced radar technology to detect and track intrusions with unparalleled accuracy. Unlike traditional motion sensors, which are prone to false alarms triggered by environmental factors, this radar device offers reliable detection capabilities in all weather conditions and lighting environments.
The AXIS D2210-VE Radar represents a paradigm shift in perimeter protection, leveraging advanced radar technology to detect and track intrusions with unparalleled accuracy. Unlike traditional motion sensors, which are prone to false alarms triggered by environmental factors, this radar device offers reliable detection capabilities in all weather conditions and lighting environments.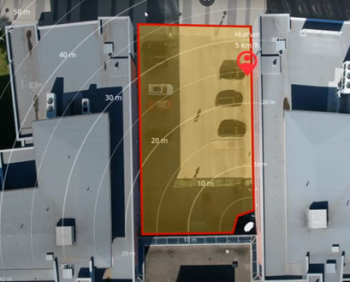 AXIS D2210-VE offers a 95° field of detection and can detect, classify, and track humans up to 60 m (200 feet) and vehicles up to 90 m (295 feet). And, with road monitoring profile enabled, the detection range for vehicles increases up to 150 m (492 feet). The radar also provides the exact position of the detected objects. AXIS D2210-VE can be used stand-alone for non-visual monitoring while safeguarding privacy. Or it can be used to steer a PTZ camera for visual verification. Furthermore, with smart coexistence functionality, it’s possible to combine up to eight AXIS D2210-VE radars in close proximity. And, you can even expand the installation with up to six AXIS D2110-VE radars and customize your detection area depending on your needs.
AXIS D2210-VE offers a 95° field of detection and can detect, classify, and track humans up to 60 m (200 feet) and vehicles up to 90 m (295 feet). And, with road monitoring profile enabled, the detection range for vehicles increases up to 150 m (492 feet). The radar also provides the exact position of the detected objects. AXIS D2210-VE can be used stand-alone for non-visual monitoring while safeguarding privacy. Or it can be used to steer a PTZ camera for visual verification. Furthermore, with smart coexistence functionality, it’s possible to combine up to eight AXIS D2210-VE radars in close proximity. And, you can even expand the installation with up to six AXIS D2110-VE radars and customize your detection area depending on your needs. I get a lot of questions about intercoms and what can be done with them as part of a robust commercial security system. Most companies secure the entrances and gates to their facility. Intercoms provide a balance between security and accessibility for visitors. Unfortunately, there can be a lot of confusion around intercoms. Including intercoms in your security setup is valuable, but you have to start with the end goal in mind. If you start down the wrong path, you may not get exactly what you want, or it might not be as easy to implement and use as you had hoped.
I get a lot of questions about intercoms and what can be done with them as part of a robust commercial security system. Most companies secure the entrances and gates to their facility. Intercoms provide a balance between security and accessibility for visitors. Unfortunately, there can be a lot of confusion around intercoms. Including intercoms in your security setup is valuable, but you have to start with the end goal in mind. If you start down the wrong path, you may not get exactly what you want, or it might not be as easy to implement and use as you had hoped. Do you need a directory listing so the visitor can call the host like what you would typically see in an apartment building? Most people want a camera on the intercom so they can see the guests, but some intercoms exist without a camera as well. The most commonly used intercom options are 1 button, 5 buttons, or a directory. Less commonly used options are a keypad, Bluetooth reader, and an induction loop.
Do you need a directory listing so the visitor can call the host like what you would typically see in an apartment building? Most people want a camera on the intercom so they can see the guests, but some intercoms exist without a camera as well. The most commonly used intercom options are 1 button, 5 buttons, or a directory. Less commonly used options are a keypad, Bluetooth reader, and an induction loop. You can have several answering stations ring at the same time, you can have calls roll over when there is no answer. You can have calls routed to one answering station during a specific time and then call another answering station during a different time. Again, you can mix and match stations that ring together, roll over, and timing.
You can have several answering stations ring at the same time, you can have calls roll over when there is no answer. You can have calls routed to one answering station during a specific time and then call another answering station during a different time. Again, you can mix and match stations that ring together, roll over, and timing. In a distant medieval realm, nestled between rolling hills and dense forests, there existed a peaceful village named Eldoria. The villagers, content in their simple lives, lived in harmony with the land. However, peace is a fragile thing, and the tranquility of Eldoria was shattered when rumors of marauding bandits spread like wildfire. Travelling caravans spoke of their perils and the destruction left behind by these marauders.
In a distant medieval realm, nestled between rolling hills and dense forests, there existed a peaceful village named Eldoria. The villagers, content in their simple lives, lived in harmony with the land. However, peace is a fragile thing, and the tranquility of Eldoria was shattered when rumors of marauding bandits spread like wildfire. Travelling caravans spoke of their perils and the destruction left behind by these marauders.