What is a Security Systems Integrator? A robbery gives some perspective.
By David Strickland, Vice President of Kenton Brothers
What in the world is a Security Systems Integrator?
 That is a great question and one I hope to answer with this story. Eleven years ago, I had no idea what a security integrator was either. It wasn’t until I got involved in the security industry and saw firsthand what a Security Systems Integrator was and why they’re so important to so many organizations.
That is a great question and one I hope to answer with this story. Eleven years ago, I had no idea what a security integrator was either. It wasn’t until I got involved in the security industry and saw firsthand what a Security Systems Integrator was and why they’re so important to so many organizations.
First let me tell you a story about a time we got robbed…
It might surprise you to know that my first involvement with a security company was like many of you. I had an alarm system put into my business. I did my research and picked a reputable, big-name company to do the work. It was a straightforward process. I was happy with my provider and trusted that they knew what they were doing. The alarm system worked great for years.
Fifteen years later I had sold my company to a much larger organization and was working with them in a brand new, large operational center in the southeast United States. This operational center counted and stored very large amounts of cash and checks and processed them daily. Security was critically important. The large company I worked for did the same thing I had done fifteen years prior. They called a big-name company to come out and install a security system to protect their assets.
The representative from the security company was in the 30,000 sq ft building for 30 minutes. A week later, they installed 2 keypads, 4 glass break sensors, some motion detectors, 2 sets of door contacts and one siren. They also installed three cameras… One in the cash room and one at the front door.
It was a great idea to have the cameras installed.
 Within the first week of opening, late at night, we were able to see a person shoot out the glass entryway of our lobby and enter the building. He ran straight to the cash room and kicked in the door. We watched him go right to the safe we had installed and enter the code. He opened the door of the safe within two minutes of entering the building. And he was on his way out carrying an armful of envelopes full of cash and checks, dropping some along the way. It was obviously a person with inside knowledge of our systems and the location of the security devices.
Within the first week of opening, late at night, we were able to see a person shoot out the glass entryway of our lobby and enter the building. He ran straight to the cash room and kicked in the door. We watched him go right to the safe we had installed and enter the code. He opened the door of the safe within two minutes of entering the building. And he was on his way out carrying an armful of envelopes full of cash and checks, dropping some along the way. It was obviously a person with inside knowledge of our systems and the location of the security devices.
It turns out the alarm didn’t go off and no one was notified until 6am the next morning when the first employees arrived and saw the carnage. Our security system was not installed by a Security Systems Integrator. It was installed by a subcontractor of a national alarm company. There’s a big difference.
A Security Systems Integrator like Kenton Brothers Systems for Security would approach this building and the liability of the cash and checks in a very different way.
Using the Defense in Depth model we would have recommended a layered approach with the following considerations:
- An exterior camera would be added to extend the perimeter and alert when there was car activity in the parking lot after operating hours
- All doors would always be locked and require key or credential entrance
- The alarm would arm automatically at a predetermined time
- If the alarm did not arm or was disarmed outside of normal hours, an alert would be issued
- The cash room door would be reinforced with a five-point door and a steel reinforced frame
- All the codes on the safe would have been changed after install and assigned to the person opening the safe, which would require dual authentication for access
- The intrusion system would be tied to the surveillance system. A video feed would be sent to the monitoring company to dispatch police as a verified crime in progress for priority response.
This true story seeks to point out the differences between an alarm company and a Security Systems Integrator. A Security Systems Integrator specializes in bringing independent security components together ensuring that those components function together properly to protect people, property, and possessions. These components include IP video surveillance, access control, intrusion detection, mass notification, weapons detection, analytics and more. Fully developed Security Systems Integrators are considered ‘design-build’ integrators.
Security Systems Integrators can provide the following services:
- Security risk or needs assessments
- Customized system engineering and design
- Broad access to the leading manufacturers and product lines
- Procurement, staging, installation, commissioning and training
- Full lifecycle service and maintenance
- System updates and operational upgrades
A Security Systems Integrator can take advantage of their unique perspective on the key ingredients for successful development of a physical security program. We like to call it the KB Advantage – utilizing over a century worth of experience and wisdom to assess, design, engineer, install, commission, train and maintain a remarkable physical security system.
If you want to know more about how we can help you develop a layered security approach for your organization, please give us a call.

 Over the last 10 years, companies, schools, churches and local government entities have invested billions of dollars in improving physical security to reduce risk and keep their people, property and possessions safe. As crime has increased, security directors and those responsible for security have done their best to meet the challenge and adapt to the threat levels they face.
Over the last 10 years, companies, schools, churches and local government entities have invested billions of dollars in improving physical security to reduce risk and keep their people, property and possessions safe. As crime has increased, security directors and those responsible for security have done their best to meet the challenge and adapt to the threat levels they face.
 One of the best ways to get rid of this debt is to outsource the maintenance and support of your systems. Establishing a relationship with a trusted security partner such as Kenton Brothers Systems for Security is something we would love to talk with you about. Think of us as a fractional Chief Security Officer. Kenton Brothers has manufacturer trained personnel to help maintain your investment as well as manage your daily alarms, annual firmware upgrades and ongoing operating system updates. We have certified physical security experts on staff that can help create policy and procedures for your specific situation.
One of the best ways to get rid of this debt is to outsource the maintenance and support of your systems. Establishing a relationship with a trusted security partner such as Kenton Brothers Systems for Security is something we would love to talk with you about. Think of us as a fractional Chief Security Officer. Kenton Brothers has manufacturer trained personnel to help maintain your investment as well as manage your daily alarms, annual firmware upgrades and ongoing operating system updates. We have certified physical security experts on staff that can help create policy and procedures for your specific situation.
 So, you have your network secure? Great! Now what kind of hardware are you using? Something as simple as a plunger switch on a cabinet can be bypassed and let someone short the lock to the back door. Do your cameras still use ‘username’ and ‘password’ for the login? Did you put resistors in line with the reader you hung on the wall? Lastly, did you leave the keys in the cabinet lock because Steve keeps losing them? Get Steve a retractable key chain and make sure your hardware is as secure as your network.
So, you have your network secure? Great! Now what kind of hardware are you using? Something as simple as a plunger switch on a cabinet can be bypassed and let someone short the lock to the back door. Do your cameras still use ‘username’ and ‘password’ for the login? Did you put resistors in line with the reader you hung on the wall? Lastly, did you leave the keys in the cabinet lock because Steve keeps losing them? Get Steve a retractable key chain and make sure your hardware is as secure as your network. This one is the hardest. People are predictable… until they’re not. Training staff and enforcing policies can be difficult. That’s why having a system that can help you mitigate the exposures people are sure to cause is a must.
This one is the hardest. People are predictable… until they’re not. Training staff and enforcing policies can be difficult. That’s why having a system that can help you mitigate the exposures people are sure to cause is a must. Access Control systems seem to be designed for 2 scenarios. Either they’re designed for hundreds of doors with a very large feature set or 1-2 doors with very few features. And finally… an access control vendor has entered the space with a product that fills the gap. Gallagher has introduced their “SMB” line.
Access Control systems seem to be designed for 2 scenarios. Either they’re designed for hundreds of doors with a very large feature set or 1-2 doors with very few features. And finally… an access control vendor has entered the space with a product that fills the gap. Gallagher has introduced their “SMB” line. By
By 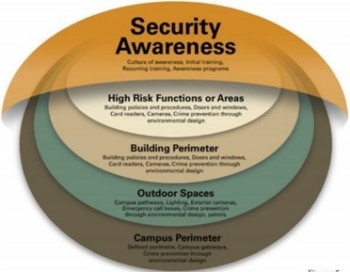 This assessment is critical for your organization to understand where it is today and where it needs to be tomorrow.
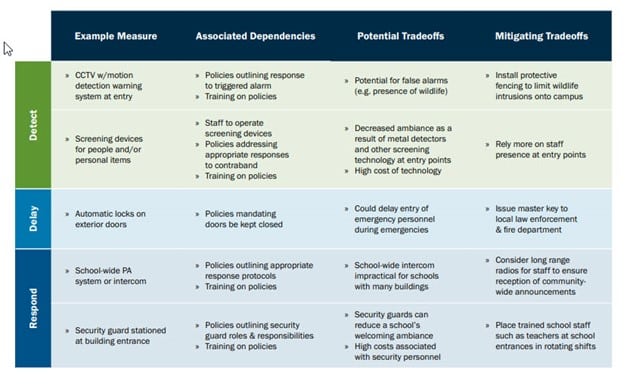
This assessment is critical for your organization to understand where it is today and where it needs to be tomorrow.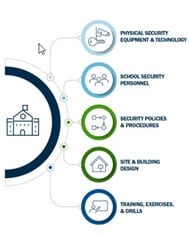 Action items might include adopting new physical security measures or improving the capacity of existing measures to detect, delay, and respond to threats across various layers of the school campus.
Action items might include adopting new physical security measures or improving the capacity of existing measures to detect, delay, and respond to threats across various layers of the school campus.