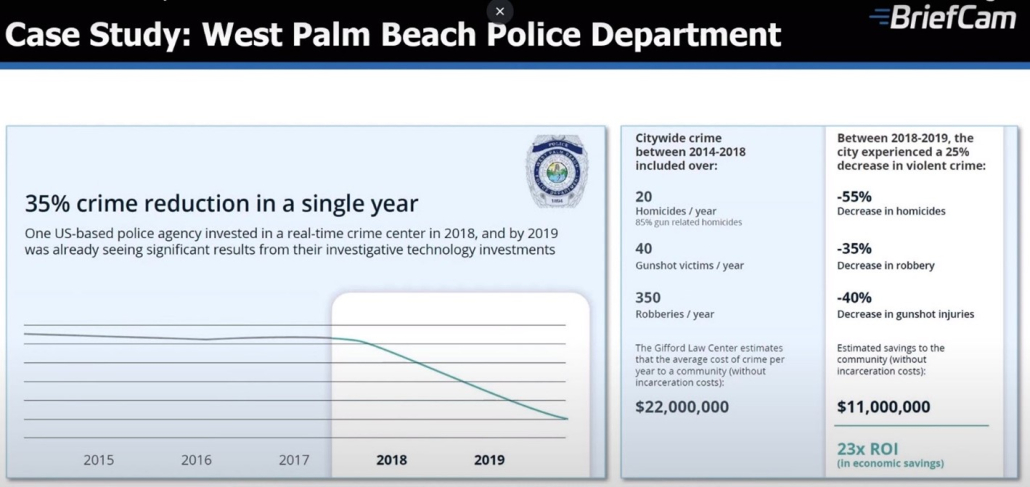
Credential Technologies: You may not be as protected as you think
By Neal Bellamy, IT Director at Kenton Brothers
 Today, I want to talk about credential technology. While not an extremely exciting topic, it can be, and often is the weakest link in many organization’s access control system. Remember that an attacker doesn’t need to get through every defense in your system, most often they just need to get past the weakest one (or two).
Today, I want to talk about credential technology. While not an extremely exciting topic, it can be, and often is the weakest link in many organization’s access control system. Remember that an attacker doesn’t need to get through every defense in your system, most often they just need to get past the weakest one (or two).
Let’s start with how cards and readers work.
Any RFID reader, including the ones used for access control, puts out an electromagnetic field around the reader. This field is usually measured in inches, but in special readers like a Nedap long-range reader, fields can be measured in feet.
When a credential (card, fob, wristband, sticker, etc.) passes through the field, it electrifies the antenna giving the chip on the credential enough electricity to transmit the data stored on the chip. Most often the data that is stored is the “Card number”. I put it in quotes because that “Card number” could be many things.
Next, we need to talk about card numbers or more specifically card formats.
Unfortunately, most card formats are simple and relatively easy to guess. The most common card formation is 26 bits in length. HID calls this H10301. The first 8 bits designate the facility code and the next 16 bits designate the card number itself. The facility code is a way to group the cards together and in theory, verify that the card belongs to the access control system.
The low bit count means that there are only 256 possible facility codes and 65,535 card numbers. For those people paying attention to the details, the extra 2 bits are used for error checking.
Most people start with card number 1 and work their way up. There are other card formats like 33-bit, 37-bit, 40-bit, and so on. Each increases the possible facility code and card number options. The important takeaway is that once an attacker has the card format, facility code, and card number of a person who has access, they can gain access to your facility.
Encryption
Like most things in commercial security, encryption is a way to combat the wrong people seeing the real card number. Encryption and card formats are independent of each other. You can have a 26-bit card that uses encryption and a 26-bit card that does not use encryption. That is based on the card technology.
Card technology like Prox and Indala are not encrypted. This means that almost any card reader can read the actual card format, facility code, and card number, it just has to get close enough to a card that has access.
Some technologies are encrypted but have already been cracked. Examples of these are Mifare Classic, HID iclass Classic, etc. Because the technology is already cracked, there are several ways of reading the encrypted data, and then applying the workaround to get to the actual card data again. Using a cracked technology is better than unencrypted, but it is still not advised.
Some technologies are not yet cracked like Mifare EV3 and HID iclass SEOS.
Encryption Usage
 When an encrypted technology is in use, both the card and reader must be using the same set of keys. Public/Private key is a long topic, but effectively a matching pair of keys are used to encrypt and decrypt data. (More information here.)
When an encrypted technology is in use, both the card and reader must be using the same set of keys. Public/Private key is a long topic, but effectively a matching pair of keys are used to encrypt and decrypt data. (More information here.)
This means that readers and credentials are matched for the different manufacturers. If you are using HID readers, you almost always need to use HID credentials. Even with an encrypted, uncracked, card technology, the most commonly sold readers and credentials use the same key pair across all readers and credentials. This means that anyone can buy the latest HID reader to read almost every HID card ever sold.
There are special programs where a business can “own” its own set of keys. Another option is to use a system that generates a unique key and then can use that key to encrypt the cards specifically for a given system like Gallagher.
I know this was a lot of information, so let’s distill it a bit.
First, make sure you are using encrypted card technology.
Second, use the latest technology when you are using encryption. This will be based on the card readers you are using.
Finally, if at all possible, own your public/private keys. Sign up for a unique key system like Corporate 1000, or use a system like Gallagher to generate a unique key for your system.
If you have more questions or need help with your current/future commercial security solution, please give us a call.

 As part of the Kenton Brothers Systems for Security core values: Innovation, we strive not only stay on top of the newest technology but bring it to you, our customers, when we come across true game changers. The Axis P1468-XLE is one those game changers.
As part of the Kenton Brothers Systems for Security core values: Innovation, we strive not only stay on top of the newest technology but bring it to you, our customers, when we come across true game changers. The Axis P1468-XLE is one those game changers.
 The camera’s low-light capabilities are enhanced, allowing it to capture usable footage in conditions with minimal illumination. This feature is crucial for maintaining surveillance effectiveness during nighttime or in poorly lit areas.
The camera’s low-light capabilities are enhanced, allowing it to capture usable footage in conditions with minimal illumination. This feature is crucial for maintaining surveillance effectiveness during nighttime or in poorly lit areas. Investing in a specialized camera designed for hazardous environments is a cost-effective solution. The AXIS P1468-XLE minimizes the risk of equipment failure and potential damage caused by explosive atmospheres, reducing the overall cost of security infrastructure.
Investing in a specialized camera designed for hazardous environments is a cost-effective solution. The AXIS P1468-XLE minimizes the risk of equipment failure and potential damage caused by explosive atmospheres, reducing the overall cost of security infrastructure.


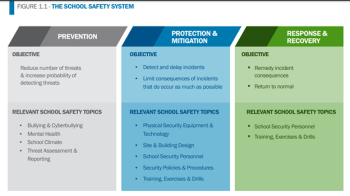
 For Kenton Brothers, ensuring the safety and security of students, teachers, and staff in schools across the country is of paramount importance. In recent years, the need for robust physical security measures in school districts has become increasingly evident due to unfortunate incidents of violence and threats. One of our areas of expertise is
For Kenton Brothers, ensuring the safety and security of students, teachers, and staff in schools across the country is of paramount importance. In recent years, the need for robust physical security measures in school districts has become increasingly evident due to unfortunate incidents of violence and threats. One of our areas of expertise is 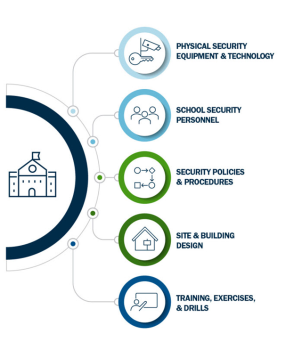
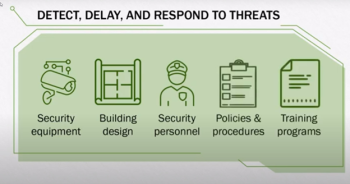
 Presented with these obstacles, Kenton Brothers went to work on understanding their current capabilities and their infrastructure through our Needs Analysis Assessment. As a part of our KB Advantage process, we set out to interview and completely understand the organizations needs from multiple points of view. Administration, HR, Facilities, Police Officers and Students. After a full assessment, Kenton Brothers recommended BriefCam analytics to solve their most pressing issues.
Presented with these obstacles, Kenton Brothers went to work on understanding their current capabilities and their infrastructure through our Needs Analysis Assessment. As a part of our KB Advantage process, we set out to interview and completely understand the organizations needs from multiple points of view. Administration, HR, Facilities, Police Officers and Students. After a full assessment, Kenton Brothers recommended BriefCam analytics to solve their most pressing issues.