Viakoo can proactively update IoT devices, strengthening your protection against hacking attempts.
By Neal Bellamy, IT Director at Kenton Brothers
 Hacking, at its root level, is a person using a computer program for a purpose that is not intended. It’s like discovering a person walking a dog and then using the dog to attack someone. That wasn’t the intent of the person walking the dog, but the hacker was able to take control. In order to “hack”, the attacker must find a weakness in the software and then exploit the weakness. In the ever-evolving game of cat and mouse, weaknesses get found and software gets modified to patch those weaknesses.
Hacking, at its root level, is a person using a computer program for a purpose that is not intended. It’s like discovering a person walking a dog and then using the dog to attack someone. That wasn’t the intent of the person walking the dog, but the hacker was able to take control. In order to “hack”, the attacker must find a weakness in the software and then exploit the weakness. In the ever-evolving game of cat and mouse, weaknesses get found and software gets modified to patch those weaknesses.
Most successful hacks are possible because the software on a device is outdated.
Even though previous weaknesses have been fixed with software updates, the newest software has not yet been installed, and new weaknesses are found that can be exploited.
In other areas of information technology (IT), we have tools to detect and notify us when software needs to be updated. Most people are probably familiar with Windows Update, the little icon on the lower right that tells us new software is ready to be installed. There are many other systems that can also notify and even update the software automatically. But there is an area of IT that generally gets missed…
The Internet of Things
 The Internet of Things (IoT) is defined as “a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers (UIDs) and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.”
The Internet of Things (IoT) is defined as “a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers (UIDs) and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.”
IoT has been around for decades. We’ve used and interacted with IoT devices in our offices for as long as I can remember. Things like copiers, scanners, and credit card machines are all examples of devices that usually are on the network and can send and receive data.
In the commercial security world, cameras and access control panels are also IoT devices. Anything that you can interact with and not have to touch is an IoT device. Can you adjust your thermostat from anywhere in the world? If so, It’s an IoT device. IoT is transforming our world and has been for many years now. It is making our lives more convenient and more connected. The security risk with IoT is that most devices are installed and never updated. If there is a security weakness detected, the software may never get installed… leaving that device wide open for being compromised.
Most companies spend a lot of IT time and money protecting servers, firewalls, and desktops to make sure that they have the latest software updates and are secure. But the IoT devices are usually left out of the discussion. IoT devices are now one of the largest attack vectors for malicious hackers. These “Set and Forget” devices are often left unprotected and sometimes directly connected to the internet. (Please don’t connect anything, except a firewall, directly to the internet; There are better ways.) As a whole, we have to do a better job of protecting these devices.
Part of the answer for the physical security world could be Viakoo’s new offering.
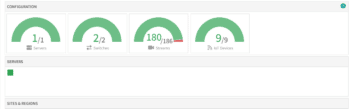 Viakoo has been offering camera, access control, and IoT monitoring for quite a while.
Viakoo has been offering camera, access control, and IoT monitoring for quite a while.
At their core, Viakoo will catalog all of your devices and monitor them at varying levels to make sure they are operational. And now Viakoo is taking it to the next level. Viakoo is offering IoT risk evaluation and IoT risk remediation. In evaluating the risk of each IoT device, Viakoo looks at the password, security certificates, and installed firmware version for each of the IoT devices. In supported devices, passwords can be changed and because Viakoo is already connected to some video management software (VMS), it can even change the password in the VMS so the video is not lost. Viakoo can also install new certificates in supported IoT devices so that they can be trusted at a higher level.
Viakoo can push new firmware to all the devices across the network. Since Viakoo architecture is already designed to be installed at multiple sites and buildings, the firmware can be pushed across the entire corporate footprint at the same time. Viakoo works across many hardware and software manufacturers, which most competing systems are not yet capable of doing, making Viakoo a good choice for almost any business with IoT devices.
Viakoo is a simple subscription-based software that can catalog, evaluate and secure all of your IoT devices. If you want help in securing your IoT Devices, please give us a call!

 That is a great question and one I hope to answer with this story. Eleven years ago, I had no idea what a security integrator was either. It wasn’t until I got involved in the security industry and saw firsthand what a Security Systems Integrator was and why they’re so important to so many organizations.
That is a great question and one I hope to answer with this story. Eleven years ago, I had no idea what a security integrator was either. It wasn’t until I got involved in the security industry and saw firsthand what a Security Systems Integrator was and why they’re so important to so many organizations. Within the first week of opening, late at night, we were able to see a person shoot out the glass entryway of our lobby and enter the building. He ran straight to the cash room and kicked in the door. We watched him go right to the safe we had installed and enter the code. He opened the door of the safe within two minutes of entering the building. And he was on his way out carrying an armful of envelopes full of cash and checks, dropping some along the way. It was obviously a person with inside knowledge of our systems and the location of the security devices.
Within the first week of opening, late at night, we were able to see a person shoot out the glass entryway of our lobby and enter the building. He ran straight to the cash room and kicked in the door. We watched him go right to the safe we had installed and enter the code. He opened the door of the safe within two minutes of entering the building. And he was on his way out carrying an armful of envelopes full of cash and checks, dropping some along the way. It was obviously a person with inside knowledge of our systems and the location of the security devices. Over the last 10 years, companies, schools, churches and local government entities have invested billions of dollars in improving physical security to reduce risk and keep their people, property and possessions safe. As crime has increased, security directors and those responsible for security have done their best to meet the challenge and adapt to the threat levels they face.
Over the last 10 years, companies, schools, churches and local government entities have invested billions of dollars in improving physical security to reduce risk and keep their people, property and possessions safe. As crime has increased, security directors and those responsible for security have done their best to meet the challenge and adapt to the threat levels they face.
 One of the best ways to get rid of this debt is to outsource the maintenance and support of your systems. Establishing a relationship with a trusted security partner such as Kenton Brothers Systems for Security is something we would love to talk with you about. Think of us as a fractional Chief Security Officer. Kenton Brothers has manufacturer trained personnel to help maintain your investment as well as manage your daily alarms, annual firmware upgrades and ongoing operating system updates. We have certified physical security experts on staff that can help create policy and procedures for your specific situation.
One of the best ways to get rid of this debt is to outsource the maintenance and support of your systems. Establishing a relationship with a trusted security partner such as Kenton Brothers Systems for Security is something we would love to talk with you about. Think of us as a fractional Chief Security Officer. Kenton Brothers has manufacturer trained personnel to help maintain your investment as well as manage your daily alarms, annual firmware upgrades and ongoing operating system updates. We have certified physical security experts on staff that can help create policy and procedures for your specific situation.
 So, you have your network secure? Great! Now what kind of hardware are you using? Something as simple as a plunger switch on a cabinet can be bypassed and let someone short the lock to the back door. Do your cameras still use ‘username’ and ‘password’ for the login? Did you put resistors in line with the reader you hung on the wall? Lastly, did you leave the keys in the cabinet lock because Steve keeps losing them? Get Steve a retractable key chain and make sure your hardware is as secure as your network.
So, you have your network secure? Great! Now what kind of hardware are you using? Something as simple as a plunger switch on a cabinet can be bypassed and let someone short the lock to the back door. Do your cameras still use ‘username’ and ‘password’ for the login? Did you put resistors in line with the reader you hung on the wall? Lastly, did you leave the keys in the cabinet lock because Steve keeps losing them? Get Steve a retractable key chain and make sure your hardware is as secure as your network. This one is the hardest. People are predictable… until they’re not. Training staff and enforcing policies can be difficult. That’s why having a system that can help you mitigate the exposures people are sure to cause is a must.
This one is the hardest. People are predictable… until they’re not. Training staff and enforcing policies can be difficult. That’s why having a system that can help you mitigate the exposures people are sure to cause is a must. Access Control systems seem to be designed for 2 scenarios. Either they’re designed for hundreds of doors with a very large feature set or 1-2 doors with very few features. And finally… an access control vendor has entered the space with a product that fills the gap. Gallagher has introduced their “SMB” line.
Access Control systems seem to be designed for 2 scenarios. Either they’re designed for hundreds of doors with a very large feature set or 1-2 doors with very few features. And finally… an access control vendor has entered the space with a product that fills the gap. Gallagher has introduced their “SMB” line.