CyPhy Part 4 – Testing Your Knowledge about the Convergence of Cyber and Physical Security
By David Strickland, Vice President of Kenton Brothers
Welcome to a bonus 4th part in our series of CyPhy – The convergence of Cyber and Physical Security.
(Part 1 | Part 2 | Part 3 | Part 4)
Is your organization up to speed with the new directives and recommendations from CISA around the convergence of Cyber and Physical Convergence?
Here’s a quiz to find out.
1) Someone removes a camera from the side of your building and connects their laptop to your network by using the Cat 6 cable connection at the camera. Is this a physical security issue or a cyber security issue?
2) Through social engineering, someone gains access to your network using a valid username and password. Is this a physical or cyber security issue?
3) Someone exploits the outdated access control reader software on the network to gain access your network. Is this a physical or cyber security issue?
4) Unknowingly, 50 of the IP video Surveillance cameras on your network are three versions behind in firmware and licensing updates. Is this a physical or cyber security issue?
5) The credentials you use are vulnerable to quick copying and duplication – even at Home Depot. Is this a physical or cyber security issue?
6) Does every IOT and IIOT device on your physical security network have updated OS software with the most current patches installed?
7) Does your physical security network have any end of life devices connected to it, such as outdated badge printers, end of life cameras?
8) Are any of the devices on your Physical security network using default, fixed or known passwords?
9) Does your physical security network and every device on it require 2 factor authentication for access?
10) Are all the components on your physical security network mac addressed to the server?
11) Are all the ports on your server or switch not being used turned off?
12) Does your Chief information Security Officer and Chief Security Officer meet regularly to discuss the security provisions in place and strategize next steps and mitigation?

Answers:
1) Cyber security of the physical network is the responsibility of both parties. Every port on the network should be Mac addressed to the device.
2) Physical – The Physical Security team controls policy and procedures and the education of mitigating social engineering threats.
3) Both parties have responsibility to understand every device connected to the physical and cyber security of the network should understand the status of that device’s firmware, OS and certificates.
4) Both parties have responsibility to understand every device connected to the physical and cyber security of the network should understand the status of that device’s firmware, OS and certificates.
5) Physical – The physical security team is responsible to select the physical components of the system and keep up to speed on the vulnerabilities inherent in them.
6) You should have a device map with every device on it and its current status of software, firmware, OS and certificates issued.
7) You should have a device map with every device on it and its current status of software, firmware, OS and certificates issued.
8) You should have policies and procedures in place to require regular password changes for each device on your network.
9) You should have dual authentication as a standard practice.
10) All components on your physical security network should be mac addressed to the server.
11) All the ports on your server or switch not being used should be disabled/turned off.
12) Your CISO and CSO should meet regularly to discuss the security provisions in place and strategize next steps and mitigation.
How did you score?
Unfortunately, even one wrong answer leaves you vulnerable.
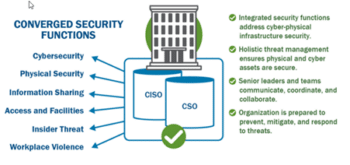
Items 7,8 and 9 are considered CISA’s ugly three. If your answers are not in alignment with the answers above, then you have an opportunity to improve your physical and cyber security.
Give Kenton Brothers Systems for Security a call today and we can help you start the conversation and make impactful changes to your network security.

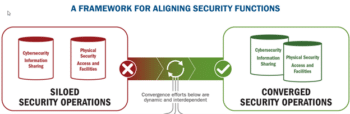
 The third of a three part series covering the Cybersecurity and Infrastructure Security Administrations (CISA) newest announcements around Security Convergence. Kenton Brothers Systems For Security hopes to help organizations understand this concept and adopt best practices for securing the Cyber-Physical Systems (CPS) currently deployed.
The third of a three part series covering the Cybersecurity and Infrastructure Security Administrations (CISA) newest announcements around Security Convergence. Kenton Brothers Systems For Security hopes to help organizations understand this concept and adopt best practices for securing the Cyber-Physical Systems (CPS) currently deployed.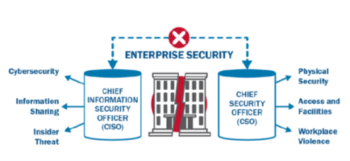

 By
By 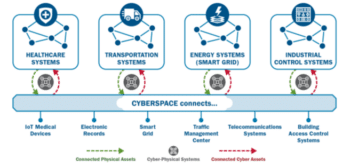


 By
By 
