Technology Update from ISC West 2021
By David Strickland, Vice President of Kenton Brothers
 The 2021 International Security Conference West Coast (ISC West) was much smaller this year, but still packed a punch for technology announcements. The smaller crowd still showed a lot of enthusiasm for the latest and greatest innovations in Commercial Video Surveillance, Access Control, Visitor Management, Intrusion detection, Public Safety and Emergency management.
The 2021 International Security Conference West Coast (ISC West) was much smaller this year, but still packed a punch for technology announcements. The smaller crowd still showed a lot of enthusiasm for the latest and greatest innovations in Commercial Video Surveillance, Access Control, Visitor Management, Intrusion detection, Public Safety and Emergency management.
Cyber and Physical Security Convergence
The overwhelming conversation this year was around the convergence of cyber and physical security. The physical security of cyber networks and the management of commercial and industrial IOT (Internet of Things) devices. High profile hacks have made the world pause and analyze how to better protect their networks and data from outside intrusion.
Currently Worldwide – 65 billion IOT devices
- 127 IOT devices being connected every second.
- Each device allows for the possibility of a vulnerability onto your network.
- More to come on this from Kenton Brothers in the future.
Artificial Intelligence
 Artificial intelligence and Robotics continued it’s flag waving this year. There are always large crowds around booths and displays for this type of technology. The use of artificial intelligence to analyze commercial video surveillance and create a proactive approach to stopping intrusion or crime continues to be a very strong driver for many companies.
Artificial intelligence and Robotics continued it’s flag waving this year. There are always large crowds around booths and displays for this type of technology. The use of artificial intelligence to analyze commercial video surveillance and create a proactive approach to stopping intrusion or crime continues to be a very strong driver for many companies.
Davantis, BriefCam and Avigilon continue to lead the way and evolve the technology to more use cases. The video analytics, AI learning and user input continue to make huge gains in deep learning and proactive measures.
With diminishing law enforcement personnel levels all across the country AI can help bridge the gap. There is no doubt that it is a force multiplier and will change the law enforcement and security industries forever.
Robotics
 The robotics offerings showed very well this year at ISC West. Cobalt robotics continued to show the strength of AI, Deep Learning and Human Intelligence all working together to create secure spaces. Their announcement of the open IP addresses check was a topic that many responded to. “Robots can also help with wireless signal intelligence: WiFi and cellular signal strength heatmaps, locations of rogue wireless access points, and the presence and identity of nearby electronic devices through techniques such as MAC address fingerprinting.”
The robotics offerings showed very well this year at ISC West. Cobalt robotics continued to show the strength of AI, Deep Learning and Human Intelligence all working together to create secure spaces. Their announcement of the open IP addresses check was a topic that many responded to. “Robots can also help with wireless signal intelligence: WiFi and cellular signal strength heatmaps, locations of rogue wireless access points, and the presence and identity of nearby electronic devices through techniques such as MAC address fingerprinting.”
Cobalt continues to wow customers with it’s ability to adapt to the workspace and create endless services.
Schedule a demo today
 The show saw some exciting new technology surface this year. Asylon showed off the its offering of Robotic perimeter security. This includes their offerings of both drones and “Guard Dogs or cats”. The combination of these two platforms gives you complete coverage and the ability to gain proactive intelligence quickly. The space is innovating quickly!
The show saw some exciting new technology surface this year. Asylon showed off the its offering of Robotic perimeter security. This includes their offerings of both drones and “Guard Dogs or cats”. The combination of these two platforms gives you complete coverage and the ability to gain proactive intelligence quickly. The space is innovating quickly!
Commercial IP Video Surveillance
Axis Communications
Axis Communications enables a smarter and safer world by creating network solutions that provide insights for improving security and new ways of doing business. As the industry leader in network video, Axis offers products and services for video surveillance and analytics, access control, and audio systems. This year, Axis spotlighted their ability to converge their platforms to one united system. Axis produced a great video that showcases the new convergence of their offerings.
Avigilon
Avigilon was busy fielding questions around the H5A system cameras. This FIPS compliant line of video surveillance has produced some excellent cameras for a wide range of needs. This line has truly raised the bar for cyber and physical security compliance. The addition of convolutional neural networks as the edge greatly increases the ability to have better, faster analytics driving commercial video surveillance. All while encrypting the footage. Check out their video explaining the line in more detail.
One new product that deserves a mention is the G.L.O.V.E. system.
The GLOVE, which stands for Generated Low Output Voltage Emitter, is a conducted electrical weapon (CEW) from Compliant Technologies. It is designed to be used in conjunction with an officer’s defensive tactics training and other use of force tools to more effectively de-escalate use of force incidents and bring non-compliant subjects under control in a safe and timely manner. Another force multiplier that is more reliable than a Taser.
In conclusion, the show was smaller this year but still packed the same punch! We look forward to next year and getting back to normal soon.


 The reader was functioning, it would read badges, but the lock wouldn’t unlock. He located the panel and determined the fuse on the power supply for that door had blown and tried replacing it with a spare from the panel. After attempting to use the lock again, the fuse popped, indicating a short in the wire or the lock, which provided more information for the customer and for our service department for when they arrived on site.
The reader was functioning, it would read badges, but the lock wouldn’t unlock. He located the panel and determined the fuse on the power supply for that door had blown and tried replacing it with a spare from the panel. After attempting to use the lock again, the fuse popped, indicating a short in the wire or the lock, which provided more information for the customer and for our service department for when they arrived on site. What was thought to be a routine visit to look at one problem turned into a four hour impromptu training and education session on the abilities available in the tools they already had. Garrett and the Remote Services Group were able to not only help Leon start using his systems in their most basic functions, but also enhance his experience and comfort by creating specific and tailored solutions within his existing environment. The time spent with The Children’s Place solidified our stance as their building safety partners and removed many potential pain points before they became a problem.
What was thought to be a routine visit to look at one problem turned into a four hour impromptu training and education session on the abilities available in the tools they already had. Garrett and the Remote Services Group were able to not only help Leon start using his systems in their most basic functions, but also enhance his experience and comfort by creating specific and tailored solutions within his existing environment. The time spent with The Children’s Place solidified our stance as their building safety partners and removed many potential pain points before they became a problem. Garrett called our manufacturing partner
Garrett called our manufacturing partner 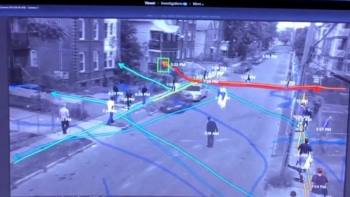 One of our local captains related, “It’s a force multiplier. One officer can run the entire system. This system will help with officer shortages.”
One of our local captains related, “It’s a force multiplier. One officer can run the entire system. This system will help with officer shortages.” In addition to this high security update, the Avigilon H5A camera line also features next-generation video analytics technology.
In addition to this high security update, the Avigilon H5A camera line also features next-generation video analytics technology.