Unveiling the New AXIS P1468-XLE: Revolutionizing Surveillance in Hazardous Environments
By David Strickland, Vice President of Kenton Brothers
 As part of the Kenton Brothers Systems for Security core values: Innovation, we strive not only stay on top of the newest technology but bring it to you, our customers, when we come across true game changers. The Axis P1468-XLE is one those game changers.
As part of the Kenton Brothers Systems for Security core values: Innovation, we strive not only stay on top of the newest technology but bring it to you, our customers, when we come across true game changers. The Axis P1468-XLE is one those game changers.
The NEW AXIS P1468-XLE Explosion-Protected Bullet Camera has emerged as a groundbreaking solution tailored for Class 1/Division 2 and ATEX Zone 2 environments. This state-of-the-art camera redefines safety and security, offering unprecedented features designed to meet the stringent requirements of hazardous areas.
Class 1/Division 2 and ATEX Zone 2 environments are known for their potentially explosive atmospheres, often found in industries such as oil and gas, petrochemicals, distilleries and manufacturing. In these settings, conventional surveillance systems may pose safety risks due to the presence of flammable gases, vapors, or dust. The AXIS P1468-XLE addresses this challenge by providing a robust and reliable solution that ensures continuous monitoring without compromising safety.
Key Features:
Explosion-Protected Design:
The AXIS P1468-XLE is engineered with an explosion-protected housing, ensuring that it can operate safely in hazardous environments. This design minimizes the risk of ignition in the presence of combustible substances, making it an ideal choice for areas where safety is paramount.
Built In Plume Detection
Smoke alert analytics monitors for signs of smoke or fire in potentially combustible environments. In operational efficiency applications, “There’s no smoke without fire” is a proverb most of us are familiar with, but even taking its literal meaning is of value: smoke is an early warning sign of a much more serious potential issue if not tackled quickly.
In any environment – from public spaces to warehouses, from stadiums to factories – it’s obvious to say that smoke itself and certainly the fire that might follow is a serious risk to human life, let alone the damage it can cause to buildings and their contents.
But in those environments where even the smallest fire or source of ignition could cause a catastrophic explosion, rapid reaction is absolutely essential. Modern network cameras combined with advanced image analysis can be used to detect possible signs of smoke or fire in a scene, complementing and providing valuable time before smoke is detected using traditional methods.
High-Quality Imaging:
Equipped with advanced imaging capabilities, this camera delivers high-resolution video even in challenging lighting conditions. Its ability to capture clear and detailed footage ensures that security personnel can identify potential threats or incidents with precision.
Extended Low-Light Performance:
 The camera’s low-light capabilities are enhanced, allowing it to capture usable footage in conditions with minimal illumination. This feature is crucial for maintaining surveillance effectiveness during nighttime or in poorly lit areas.
The camera’s low-light capabilities are enhanced, allowing it to capture usable footage in conditions with minimal illumination. This feature is crucial for maintaining surveillance effectiveness during nighttime or in poorly lit areas.
Integrated Infrared (IR) Illumination:
The AXIS P1468-XLE comes equipped with integrated IR illumination, extending its surveillance capabilities into the dark. This feature is essential for 24/7 monitoring, providing continuous security coverage regardless of external lighting conditions.
Remote Management and Monitoring:
The camera is designed to facilitate remote management and monitoring, allowing security personnel to access live feeds and recorded footage from a central location. This feature enhances situational awareness and enables swift response to potential incidents.
Compliance with Industry Standards:
The AXIS P1468-XLE complies with international standards and certifications for hazardous environments, including ATEX and UL certifications. This ensures that the camera meets the strict safety requirements necessary for deployment in Class 1/Division 2 and ATEX Zone 2 areas.
Benefits:
Enhanced Safety:
The foremost benefit of the AXIS P1468-XLE is its contribution to enhanced safety. By providing reliable surveillance in hazardous environments, it helps prevent incidents and ensures the well-being of personnel and assets.
Operational Continuity:
The camera’s robust design and advanced features enable it to operate seamlessly in challenging conditions. This contributes to operational continuity by maintaining surveillance capabilities in all circumstances.
Cost-Effective Security:
 Investing in a specialized camera designed for hazardous environments is a cost-effective solution. The AXIS P1468-XLE minimizes the risk of equipment failure and potential damage caused by explosive atmospheres, reducing the overall cost of security infrastructure.
Investing in a specialized camera designed for hazardous environments is a cost-effective solution. The AXIS P1468-XLE minimizes the risk of equipment failure and potential damage caused by explosive atmospheres, reducing the overall cost of security infrastructure.
Regulatory Compliance:
With its adherence to international safety standards, the AXIS P1468-XLE assists organizations in meeting regulatory requirements for surveillance in hazardous locations. This compliance is essential for legal and insurance purposes.
The AXIS P1468-XLE
The AXIS P1468-XLE Explosion-Protected Bullet Camera stands at the forefront of innovation, addressing the unique challenges posed by Class 1/Division 2 and ATEX Zone 2 environments. Its combination of advanced features, compliance with safety standards, and commitment to reliability make it an indispensable tool for industries where safety and security are non-negotiable. As technology continues to evolve, the AXIS P1468-XLE sets a new standard for surveillance in hazardous environments, ensuring that organizations can embrace the future with confidence and peace of mind.
Give us a call today to demo one of these amazing cameras!

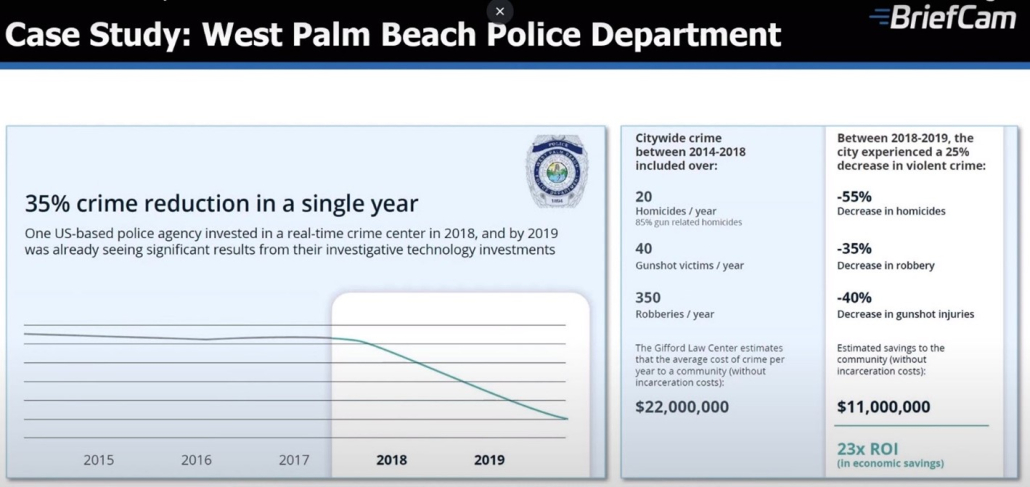
 Presented with these obstacles, Kenton Brothers went to work on understanding their current capabilities and their infrastructure through our Needs Analysis Assessment. As a part of our KB Advantage process, we set out to interview and completely understand the organizations needs from multiple points of view. Administration, HR, Facilities, Police Officers and Students. After a full assessment, Kenton Brothers recommended BriefCam analytics to solve their most pressing issues.
Presented with these obstacles, Kenton Brothers went to work on understanding their current capabilities and their infrastructure through our Needs Analysis Assessment. As a part of our KB Advantage process, we set out to interview and completely understand the organizations needs from multiple points of view. Administration, HR, Facilities, Police Officers and Students. After a full assessment, Kenton Brothers recommended BriefCam analytics to solve their most pressing issues.


 We recently received a Chain of Custody request from one of our banking clients. They had an event that they deemed legally significant and requested our help in documenting what had happened. They needed our help to get the video segments exported properly. They wanted footage from all of the cameras at one of their locations over the past 30 days. (That’s a good amount of video data!)
We recently received a Chain of Custody request from one of our banking clients. They had an event that they deemed legally significant and requested our help in documenting what had happened. They needed our help to get the video segments exported properly. They wanted footage from all of the cameras at one of their locations over the past 30 days. (That’s a good amount of video data!) Chain of Custody is something Kenton Brothers takes extremely seriously for many reasons. One, we want to make sure we are providing our customers with a level of service and reliability they can count on. We also want to make sure law enforcement has what they need to support or refute claims. This is also a great example of how the commercial security systems we sell and support do what they’re supposed to do.
Chain of Custody is something Kenton Brothers takes extremely seriously for many reasons. One, we want to make sure we are providing our customers with a level of service and reliability they can count on. We also want to make sure law enforcement has what they need to support or refute claims. This is also a great example of how the commercial security systems we sell and support do what they’re supposed to do. In today’s episode of “Yes, we can do that”, I bring you Radio Towers. It’s not the first time we have placed equipment on towers, but this time I have pictures!
In today’s episode of “Yes, we can do that”, I bring you Radio Towers. It’s not the first time we have placed equipment on towers, but this time I have pictures!







 Critical infrastructure protection has become a paramount concern for the US government and private organizations alike. From power plants to transportation hubs, food manufacturing to water and waste facilities… these sites are critical to a properly functioning society. Their importance makes them a prime target for a range of threats, from physical attacks to cyber-attacks. As far as commercial security goes, technology is playing a crucial role, and one such technological marvel is the drone.
Critical infrastructure protection has become a paramount concern for the US government and private organizations alike. From power plants to transportation hubs, food manufacturing to water and waste facilities… these sites are critical to a properly functioning society. Their importance makes them a prime target for a range of threats, from physical attacks to cyber-attacks. As far as commercial security goes, technology is playing a crucial role, and one such technological marvel is the drone. The video imagery captured by a UAV is ideally suited for reconnaissance or rapid situation awareness. It has the advantage for security personnel to detect and monitor potential threats from a safe distance. UAVs in perimeter security reduce the requirement for foot patrols by security guards. They provide real time situational awareness with the added perk of recording video for analysis later on.
The video imagery captured by a UAV is ideally suited for reconnaissance or rapid situation awareness. It has the advantage for security personnel to detect and monitor potential threats from a safe distance. UAVs in perimeter security reduce the requirement for foot patrols by security guards. They provide real time situational awareness with the added perk of recording video for analysis later on.