Why Drive a Model T When You Could Be Driving a Tesla?
By Neal Bellamy, IT Director at Kenton Brothers
 When a mechanic looks at a car, he doesn’t see a specific brand, model or color. He really sees the overall system. He sees an engine, brakes and wheels. Whether it’s a Model T or a Tesla, if the engine doesn’t work, it won’t go anywhere; if the brakes don’t work, it doesn’t stop and of course flat wheels don’t roll. Access control systems are similar. They’re really just a set of inputs, output and readers.
When a mechanic looks at a car, he doesn’t see a specific brand, model or color. He really sees the overall system. He sees an engine, brakes and wheels. Whether it’s a Model T or a Tesla, if the engine doesn’t work, it won’t go anywhere; if the brakes don’t work, it doesn’t stop and of course flat wheels don’t roll. Access control systems are similar. They’re really just a set of inputs, output and readers.
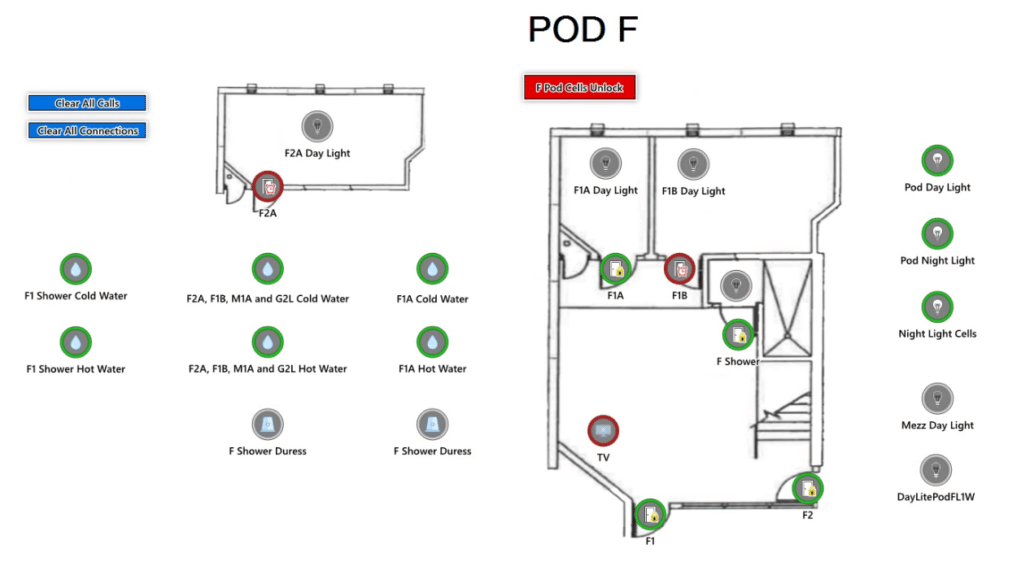
When it comes to access control systems in detention centers, they usually don’t need readers. This is the reason that PLCs (Programming Logic Controllers) dominate access control for detention centers.
What are PLCs?
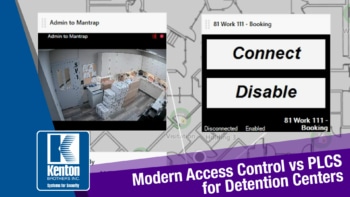
PLCs, created in the 1960’s, are most commonly a simple set of inputs and outputs. Because they’ve been around for so long, and lend themselves to centralized control, most detention centers are driven from a PLC. A PLC reads an input from a touchscreen to open a door, connect an intercom, or turn on a light. An open door illuminates on the touchscreen to show it’s not secured. The PLC might even be tied to cameras to show a specific camera when an intercom is pressed. It’s all ITTT logic; If This, Then That.
There is a lot of overlap between a PLC in a detention center and access control. Access control still needs to be able to open a door and show that a door is unlocked. An access control system might even be tied to intercoms or a video system. However, most access control systems are not designed for lights, water valves or guard tours. That’s when you need something that fits in between.
PLC Challenges
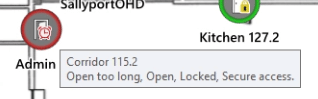 One of the issues with a PLC is that it’s mostly wires. Changes to a PLC system are difficult and can be expensive. Most integrations from an intercom system or a video system are done with wires. If you have a hundred cameras, you have a hundred wires. 50 intercoms require 50 wires.
One of the issues with a PLC is that it’s mostly wires. Changes to a PLC system are difficult and can be expensive. Most integrations from an intercom system or a video system are done with wires. If you have a hundred cameras, you have a hundred wires. 50 intercoms require 50 wires.
Sometimes, there are communication-based integrations. But even then, station 10 will always be station 10. Even if station 10 ends up being in a closet after a remodel, it is still station 10. Even small changes to a touchscreen require hours of programming by specialized personnel. While PLC systems can talk to other systems like intercoms and cameras, they are still separate systems with separate interfaces. It’s not all managed through one “pane of glass”.
It’s time for this situation to change.
 Access control systems like Gallagher still handle the inputs and outputs like a PLC system does, but these updated systems add flexibility.
Access control systems like Gallagher still handle the inputs and outputs like a PLC system does, but these updated systems add flexibility.
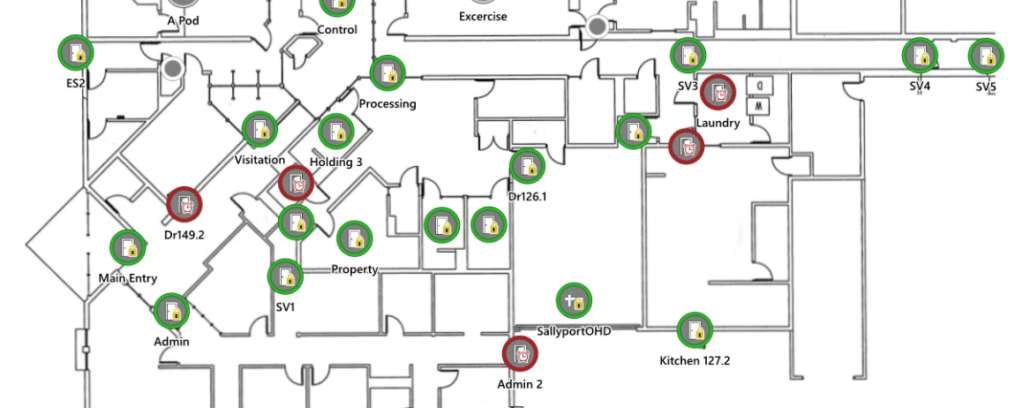
Gallagher integrations with intercom systems like Harding, and video systems like Milestone are purely programming and IP based. Changes in the Milestone system get reflected in the Gallagher programming. Changing and adding cameras, intercoms, doors or moving a map are as simple as clicking edit on the site map. Everything can be managed through the Gallagher interface. Connecting an intercom, initiating a lockdown, turning lights on and off are all handled through the click of a button. If a door is opened and it shouldn’t be, Gallagher can bring it to the forefront so it can be dealt with. Alerts, automated instructions, logs and alarm escalations are all built right into the software.
While a Model T and a Tesla might both have an engine, brakes and wheels, no one would ever say that they’re equals. Both cars might get you to where you’re going, but one of them will drive itself to your destination with the AC on while playing music from your favorite radio station.
PLCs are getting the job done for detention centers across the country, but wouldn’t you like to have a solution that gives you more features and flexibility, while costing you less?
We can help you get there. Just give us a call.

 In the security industry, cloud based video recording, retrieval, storage and archiving solutions are leading the charge for growing video subscriptions as a service.
In the security industry, cloud based video recording, retrieval, storage and archiving solutions are leading the charge for growing video subscriptions as a service. 1. Scalability: Cloud-based systems can easily scale to accommodate a growing number of users and devices, without the need for expensive hardware upgrades. This makes them a cost-effective solution for businesses that are expanding or experiencing high levels of turnover.
1. Scalability: Cloud-based systems can easily scale to accommodate a growing number of users and devices, without the need for expensive hardware upgrades. This makes them a cost-effective solution for businesses that are expanding or experiencing high levels of turnover. It’s certainly not the best blog I’ve ever written, but it might not be the worst either. It’s factual, it is the top 5 reasons IT companies got to the cloud, and it has no grammatical errors. The coolest part about this content is that I asked only a single question to the AI… “Can you write a blog post on why cloud based physical access control is better than on premise access control server?”
It’s certainly not the best blog I’ve ever written, but it might not be the worst either. It’s factual, it is the top 5 reasons IT companies got to the cloud, and it has no grammatical errors. The coolest part about this content is that I asked only a single question to the AI… “Can you write a blog post on why cloud based physical access control is better than on premise access control server?” By
By  Based on the research of industry experts, here is a breakdown of things to come in 2023 based on their insights and opinions.
Based on the research of industry experts, here is a breakdown of things to come in 2023 based on their insights and opinions.