Innovation: Drones. The Guardian Angels of Critical Infrastructure
By David Strickland, Vice President of Kenton Brothers
Kenton Brothers is celebrating 125 years in business this year, and over those decades we’ve seen our share of innovative technology. KB was around for the first cars, motorized bikes, airplanes, rockets, robots and now security drones. As you may have read before, we believe strongly in the premise “Innovate or die”.
We get excited when technology innovates to solve a problem.
 Critical infrastructure protection has become a paramount concern for the US government and private organizations alike. From power plants to transportation hubs, food manufacturing to water and waste facilities… these sites are critical to a properly functioning society. Their importance makes them a prime target for a range of threats, from physical attacks to cyber-attacks. As far as commercial security goes, technology is playing a crucial role, and one such technological marvel is the drone.
Critical infrastructure protection has become a paramount concern for the US government and private organizations alike. From power plants to transportation hubs, food manufacturing to water and waste facilities… these sites are critical to a properly functioning society. Their importance makes them a prime target for a range of threats, from physical attacks to cyber-attacks. As far as commercial security goes, technology is playing a crucial role, and one such technological marvel is the drone.
Drones, once confined to hobbyists and aerial photography enthusiasts, have now emerged as powerful tools in the realm of physical security for critical infrastructure.
Terrorist organizations, criminal syndicates, and even disgruntled individuals may attempt to breach the security of critical infrastructure through physical means. These attacks can range from sabotage to theft of sensitive materials. To address these threats, security measures must be proactive, adaptable, and capable of providing real-time information. This is where drones come into play.
Guardian Angel – Aerial Surveillance
Drones offer a versatile platform for aerial surveillance. Equipped with high-definition cameras, thermal imaging, LIDAR and other advanced sensors, drones can provide a bird’s-eye view of critical infrastructure, offering security personnel unprecedented situational awareness. They can patrol vast areas efficiently and discreetly, making them ideal for spotting suspicious activities, unauthorized access, or potential vulnerabilities.
Incorporating machine learning algorithms and artificial intelligence, drones can be programmed to identify unusual behavior patterns, such as trespassing or loitering, and issue alerts in real-time. This proactive approach allows security teams to respond swiftly to potential threats before they escalate into security breaches. Unmanned aerial vehicles (UAVs) provide a rapid response and fast “eyes on” to the target area. They also provide live updates to control stations while active waypoint tracking can be maintained based on target parameters like thermal signatures.
A key advantage of a UAV is its ability to collect video.
 The video imagery captured by a UAV is ideally suited for reconnaissance or rapid situation awareness. It has the advantage for security personnel to detect and monitor potential threats from a safe distance. UAVs in perimeter security reduce the requirement for foot patrols by security guards. They provide real time situational awareness with the added perk of recording video for analysis later on.
The video imagery captured by a UAV is ideally suited for reconnaissance or rapid situation awareness. It has the advantage for security personnel to detect and monitor potential threats from a safe distance. UAVs in perimeter security reduce the requirement for foot patrols by security guards. They provide real time situational awareness with the added perk of recording video for analysis later on.
The speed, size, maneuverability, and additional technologies make UAVs the perfect supplement to ground security. They allow security teams to perform monitoring tasks more quickly and efficiently. For this reason, drones have a competitive edge over stationary cameras, as the drone can be flown at different times and be guided to blind spots.
Another significant advantage of using drones for commercial security is their ability to provide rapid intelligence and response. In the event of an intrusion or emergency, drones can be deployed within minutes, whereas traditional security personnel may take much longer to arrive at the scene. This quick response time can be critical in preventing or minimizing damage to critical infrastructure. Additionally, upon alert a drone can cover up to 10 times the area of a vehicle response in a fraction of the time.
Drones can also access areas that may be challenging or dangerous for human responders. Scenarious include climbing steep terrain or inspecting hard-to-reach locations like the tops of tall structures. This ensures that security teams have eyes on the situation even in the most challenging circumstances.
Super Human Capabilities
Drones equipped with environmental sensors can play a vital role in safeguarding critical infrastructure from natural disasters.
By regularly monitoring factors like water levels, temperature, humidity, and seismic activity, drones can provide early warnings and data for disaster preparedness and response plans.
For instance, a drone surveying a dam can detect signs of structural weakness or unusual water flow patterns, allowing for timely maintenance or intervention to prevent a catastrophic failure.
Similarly, drones can monitor forests surrounding power lines for signs of wildfires, helping utilities take proactive measures to prevent electrical equipment from sparking fires during dry, windy conditions.
Routine inspections of critical infrastructure are essential to ensure their continued operation and safety. Traditionally, these inspections have been carried out by human inspectors, often requiring extensive downtime and posing safety risks. Drones can revolutionize this process. Equipped with high-resolution cameras, infrared sensors and low frequency radar, drones can conduct detailed inspections of infrastructure such as bridges, pipelines, and power lines. They can capture images and data that are difficult or impossible for human inspectors to obtain.
As critical infrastructure continues to be a prime target for a wide range of threats, the adoption of drone technology for physical security is becoming increasingly important.
Drones offer a unique set of capabilities, including aerial surveillance, rapid response, environmental monitoring, infrastructure inspection, and scalability. Like we mentioned, our team at Kenton Brothers Systems for Security gets excited when technology innovates to solve a problem. In this case, drones and critical infrastructure are a match made in heaven and we couldn’t be more excited!
If you are thinking about ways to help secure your critical infrastructure location and would like to explore the use of drones, please let us know and we will set up a demo with you!






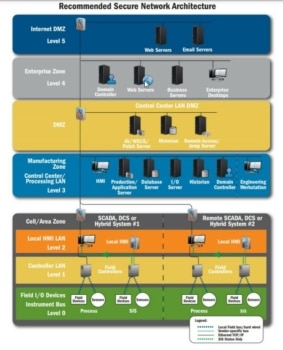
 It’s a well-known fact that most breaches (95%+) are a failure of procedure or policy over systems. A good
It’s a well-known fact that most breaches (95%+) are a failure of procedure or policy over systems. A good  Too many times we see organizations practice poor alarm management. Alarms in any form (Fire, Access Control, Intrusion Detection, Car) should never be ignored yet many times are. OT devices are vulnerable to physical attack and to things like flooding, fire and electrical damage. A system alarm can help bring immediate attention if properly managed.
Too many times we see organizations practice poor alarm management. Alarms in any form (Fire, Access Control, Intrusion Detection, Car) should never be ignored yet many times are. OT devices are vulnerable to physical attack and to things like flooding, fire and electrical damage. A system alarm can help bring immediate attention if properly managed. 1. Scalability: Cloud-based systems can easily scale to accommodate a growing number of users and devices, without the need for expensive hardware upgrades. This makes them a cost-effective solution for businesses that are expanding or experiencing high levels of turnover.
1. Scalability: Cloud-based systems can easily scale to accommodate a growing number of users and devices, without the need for expensive hardware upgrades. This makes them a cost-effective solution for businesses that are expanding or experiencing high levels of turnover. It’s certainly not the best blog I’ve ever written, but it might not be the worst either. It’s factual, it is the top 5 reasons IT companies got to the cloud, and it has no grammatical errors. The coolest part about this content is that I asked only a single question to the AI… “Can you write a blog post on why cloud based physical access control is better than on premise access control server?”
It’s certainly not the best blog I’ve ever written, but it might not be the worst either. It’s factual, it is the top 5 reasons IT companies got to the cloud, and it has no grammatical errors. The coolest part about this content is that I asked only a single question to the AI… “Can you write a blog post on why cloud based physical access control is better than on premise access control server?”