Why Physical Security has to be part of the convergence discussion of OT/ICS security.
By David Strickland, Vice President of Kenton Brothers
 There is a real buzz in the security world right now around securing Operational Technology (OT) and Industrial Control Systems (ICS). This buzz comes from two sources: companies and organizations that are being attacked through cyber security and physical attacks, and government agencies trying to get information broadcast to counter these threats. Threat levels have been increasing over the last few years and the cost of these attacks have risen to devastating levels.
There is a real buzz in the security world right now around securing Operational Technology (OT) and Industrial Control Systems (ICS). This buzz comes from two sources: companies and organizations that are being attacked through cyber security and physical attacks, and government agencies trying to get information broadcast to counter these threats. Threat levels have been increasing over the last few years and the cost of these attacks have risen to devastating levels.
According to CISA, in the first half of 2022 there were at least 22 reported large impact attacks on critical infrastructure leading to billions of dollars in losses. As the second half of 2022 numbers are being compiled, the sense of urgency to shore up the vulnerabilities is at an all time high.
How is OT security different than IT Cybersecurity?
IT – Information technology is just that. It is the transfer of data or information through physical appliances such as routers, switches and servers. Security for this technology centers around the prevention, detection and mitigation of attacks from software.
OT or Operational Technology is the manipulation of real world physical devices such as pumps, valves and controls through software or human interaction. These are called Industrial Control systems. In contrast to IT cybersecurity attacks, the outcomes of successful OT / ICS attacks include the potential to impact human safety and damage physical equipment. For example, taking any industrial processes OT / ICS equipment offline for extended time periods. This can be done through software or physical attacks known as sabotage.
Many organizations point to the Purdue Model for protecting OT and ICS.
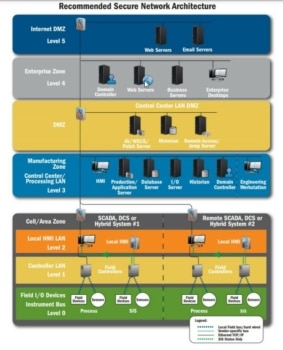 The Purdue model, created in the 1990’s is a comprehensive look at protecting ICS and has been the standard for many years. The Purdue Model has five zones that are considered when creating a robust security model. Yes, this model is the current standard, but in our opinion does not adequately address physical security.
The Purdue model, created in the 1990’s is a comprehensive look at protecting ICS and has been the standard for many years. The Purdue Model has five zones that are considered when creating a robust security model. Yes, this model is the current standard, but in our opinion does not adequately address physical security.
Cybersecurity of IT, IIT (Industrial IT) and OT systems is still a very high priority.
A recent comprehensive report provided by the Department of Homeland Security (DHS) pointed out a few concerns. “Many organizations lack visibility into their complete OT environments, including IT/OT interconnections and supply chain dependencies. Cybersecurity is overwhelming for organizations and entities with small staffs and budgets. As a result, many are not able to achieve the cybersecurity posture required to adequately secure their IT/OT infrastructure. The majority of legacy OT equipment was never designed for internet connectivity, and may not easily be replaced, making it increasingly challenging to secure in converged environments.”
We must not make the mistake of ignoring the real probability of physical attacks on these same organizations that are overwhelmed with cybersecurity.
“A top priority must be to prevent unauthorized physical access, damage and interference to the organization’s information and information processing facilities. Essentially a key aspect of this standard is to implement effective access control and protection of systems and equipment from damage.”
Physical Security for the OT Starts here:
Policies and Procedures:
 It’s a well-known fact that most breaches (95%+) are a failure of procedure or policy over systems. A good red team will tell you that their most effective weapon for entry is a poorly trained or poorly disciplined employee. Polices and procedures must be created, trained, followed and tested constantly.
It’s a well-known fact that most breaches (95%+) are a failure of procedure or policy over systems. A good red team will tell you that their most effective weapon for entry is a poorly trained or poorly disciplined employee. Polices and procedures must be created, trained, followed and tested constantly.
Establishing your perimeter:
As with most things involving physical security, you must start with a strong perimeter. This perimeter must be extended as far as physically possible. Access should be granted to only authorized personnel that have been through proper background checks and assigned clearance based on their job function. The perimeter is your best chance at early detection, reaction and mitigation.
Access Control:
Only authorized personnel with the proper clearance and certifications should ever be allowed access to your OT systems. These authorized personnel should constantly be vetted. Many organizations don’t remove terminated employees from this list quickly. No visitors or vendors should ever be allowed access without proper vetting and escort. Your access control systems should be set up in concentric circles with stronger policy the closer you get to critical infrastructure. All access control devices should be kept in proper working order and updated with proper firmware and cyber security practices.
Alarms:
 Too many times we see organizations practice poor alarm management. Alarms in any form (Fire, Access Control, Intrusion Detection, Car) should never be ignored yet many times are. OT devices are vulnerable to physical attack and to things like flooding, fire and electrical damage. A system alarm can help bring immediate attention if properly managed.
Too many times we see organizations practice poor alarm management. Alarms in any form (Fire, Access Control, Intrusion Detection, Car) should never be ignored yet many times are. OT devices are vulnerable to physical attack and to things like flooding, fire and electrical damage. A system alarm can help bring immediate attention if properly managed.
Surveillance:
Who inspects the inspector? Your IP video surveillance system. It keeps honest people honest and identifies those who are not. Critical infrastructure devices should have surveillance on the device itself and the human interaction point. This of course is on top of all perimeter entrance areas and key points throughout your property.
Knowledge and Cooperation:
The United States can leverage an existing body of knowledge to secure OT infrastructure. Prioritizing and applying these best practices, recommendations, and standards more broadly, in a comprehensive and accelerated manner, would strengthen security and achieve strategic outcomes.
Kenton Brothers Systems for Security stands by to do our part. Please let us know how we can help your organization.

 1. Scalability: Cloud-based systems can easily scale to accommodate a growing number of users and devices, without the need for expensive hardware upgrades. This makes them a cost-effective solution for businesses that are expanding or experiencing high levels of turnover.
1. Scalability: Cloud-based systems can easily scale to accommodate a growing number of users and devices, without the need for expensive hardware upgrades. This makes them a cost-effective solution for businesses that are expanding or experiencing high levels of turnover. It’s certainly not the best blog I’ve ever written, but it might not be the worst either. It’s factual, it is the top 5 reasons IT companies got to the cloud, and it has no grammatical errors. The coolest part about this content is that I asked only a single question to the AI… “Can you write a blog post on why cloud based physical access control is better than on premise access control server?”
It’s certainly not the best blog I’ve ever written, but it might not be the worst either. It’s factual, it is the top 5 reasons IT companies got to the cloud, and it has no grammatical errors. The coolest part about this content is that I asked only a single question to the AI… “Can you write a blog post on why cloud based physical access control is better than on premise access control server?” October is Cybersecurity awareness month!
October is Cybersecurity awareness month! 3) USE MULTI-FACTOR AUTHENTICATION
3) USE MULTI-FACTOR AUTHENTICATION 
 Hacking, at its root level, is a person using a computer program for a purpose that is not intended. It’s like discovering a person walking a dog and then using the dog to attack someone. That wasn’t the intent of the person walking the dog, but the hacker was able to take control. In order to “hack”, the attacker must find a weakness in the software and then exploit the weakness. In the ever-evolving game of cat and mouse, weaknesses get found and software gets modified to patch those weaknesses.
Hacking, at its root level, is a person using a computer program for a purpose that is not intended. It’s like discovering a person walking a dog and then using the dog to attack someone. That wasn’t the intent of the person walking the dog, but the hacker was able to take control. In order to “hack”, the attacker must find a weakness in the software and then exploit the weakness. In the ever-evolving game of cat and mouse, weaknesses get found and software gets modified to patch those weaknesses. The Internet of Things (IoT) is defined as “a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers (UIDs) and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.”
The Internet of Things (IoT) is defined as “a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers (UIDs) and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction.”