Convenience is not worth the price of a life: Security failures at Robb Elementary School in Uvalde.
 By David Strickland, Vice President of Kenton Brothers
By David Strickland, Vice President of Kenton Brothers
At the meeting point between commercial security and convenience, a decision must be made. Is the convenience worth the price of a life? This all too real scenario was laid out on July 17, 2022 in the pages of the Investigative Committee Report on the Robb Elementary Shooting.
As I write this blog, I’m heartbroken to receive the news that more life has been tragically lost due to poor execution of physical security procedures. As a father of school aged kids, and an industry advocate, I find myself concerned by what I read in the report. It has spawned new conversations with local school districts and how they are managing the risk of active shooters.
Systemic Failures and Poor Decision Making
The Texas state police released their report on the Uvalde School shooting and at the heart of it is “systemic failures and egregious poor decision making.” The report included a scathing rebuke of a culture of complacency. This coupled with a tragically flawed response led to the “loss of 21 souls stolen from their families and friends.”
At 11:33 an armed suspect walked into Robb elementary through an unlocked door. The door was unlocked for the convenience of staff members.
In 2019 Uvalde adopted a policy for responding to an active shooter emergency.
Part of this policy includes:
LOCKED CLASSROOM DOOR POLICY – Teachers are instructed to keep their classroom doors closed and locked at all times. Barriers are not to be used. Substitutes shall follow the same policy, with campuses ensuring they have access to the classrooms they need throughout the day. The Standard Response Protocol procedures are on the back of all of our badges issued to substitute teachers.
STAFF TRAINING – All staff members are trained annually in emergency protocols for the campus. Key campus personnel are CPI-trained.
STUDENT TRAINING & DRILLS – Students receive training on the Standard Response Protocol for lockout, lockdown, evacuate, shelter, and hold. In addition, drills are held for each of these emergency actions on a regular basis
While building security systems including Access Control, IP Video Surveillance, Intrusion detection and Weapons Detection are crucial to physical security, they are only effective if the human element of discipline and accountability to process and procedure are adhered to.
Practice, practice, practice.
Daily habits, that become routine when practiced regularly, dramatically improve the effectiveness of the security systems at any physical site. When these same habits are sacrificed for convenience, it renders your systems ineffective and risk goes through the roof. I can place a $5,000 lock at every door, but If I prop the door open because I don’t like carrying my credential with me, or I don’t like walking around the building to get back in, I have exposed every single soul in that building to a potentially tragic scenario.
I can tell myself that it’s only this one time – but it only takes one time. We don’t get to choose when or where an active shooter will bring violence to our doorstep. We can only control how we prepare and manage the risk of it happening.
The report points out that the door the shooter came in was either unlocked or propped open for the convenience of the staff to leave and reenter the building. “This practice became the norm at the school as there was no accountability from leadership around following security procedures.”
 Some will say that hindsight is 20/20.
Some will say that hindsight is 20/20.
The report goes on to point out that the school staff were trained in active shooter drills and did have a physical security plan in place, but didn’t follow it properly.
This tragedy should act as a wake-up call and an invitation to evaluate the current organizational management of your physical security systems and practices. Physical security systems, practices and procedures are designed to prevent, delay and reduce loss of life and gain precious seconds and minutes for authorities or designated personnel to respond with overwhelming force.
When was the last time you reviewed your organization’s emergency plan?
When was the last time you had drills to practice the response?
In part 2 of this series on Convenience vs. Security, we will discuss the top 5 ways to help your organization be secure and ready for emergencies.



 By
By 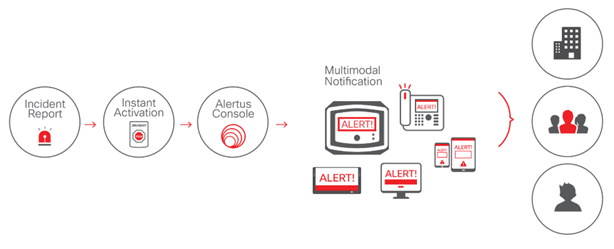
 Scenario 1: Active Shooter or Disgruntled Person
Scenario 1: Active Shooter or Disgruntled Person Scenario 2: Tornado
Scenario 2: Tornado Scenario 3: Medical Alert
Scenario 3: Medical Alert Kenton Brothers is celebrating its 125th year of being a commercial locksmith located in Kansas City, MO. Over the years, we’ve rekeyed just about everything. One of the types of projects we really enjoy is bringing large scale buildings onto master key systems. We’ve talked about
Kenton Brothers is celebrating its 125th year of being a commercial locksmith located in Kansas City, MO. Over the years, we’ve rekeyed just about everything. One of the types of projects we really enjoy is bringing large scale buildings onto master key systems. We’ve talked about